What are the dangers of the Anti-Fraud Center app? How to resist? - Audit Report
As shown above, a Chinese comment recently mentioned "four levels of reality." Maybe you're wondering what it's really like. In fact, what IYP has been showing is the 3rd and 4th layers. This article will once again use the realistic theme of "anti-fraud center" as a demonstration to peel off this "onion".
——Layer 2——
Of all the threats emanating from the ruling class, forcing citizens to install specific applications is the lowest-end (and perhaps the most cost-effective, cheaper than spyware that sells for millions of dollars). Much more – from technology costs to PR costs ).
If we assume that surveillance is its main strategic goal, the effectiveness of forced installation of apps depends solely on citizen compliance . Citizens will not take the initiative to comply, so the ruling class will first set up a series of social engineering methods - from deception to inducement to tightening authority to threaten people's daily lives. This is the story you have already seen in the “Promotion” of the Anti-Fraud Center App, and it is the same story you can see in different countries around the world.
We've published the India story before, and here it is just one example of a more typical set of tactics: authorities force people to install a surveillance app that not only records your every move, but also blocks It prevents other apps on your phone like Facebook and YouTube from working; it even remotely deletes anything on your phone that the authorities are not happy with; if you refuse to install the app, you will lose your job and your family and children will suffer. Hungry, even once installed, you cannot uninstall it. Uninstallation has no effect on preventing surveillance, and the person who performs the uninstallation will be included in the authorities' key stability maintenance blacklist.
For China's "Anti-Fraud Center" application, at least so far, it seems that we have not heard of such horrific mandatory punitive measures and surveillance capabilities as India; however, its nature is exactly the same . As German rebels emphasized during the global anti-police violence protest movement : "We cannot be satisfied without being shot head-on" - we are human beings and we deserve basic human rights, freedom from surveillance and freedom from slaughter. They are all basic human rights.
On the surface, the Anti-Fraud Center application has at least three features that make it different from popular global spyware, such as Israel’s NSO’s “Pegasus” ( see here how to resist this most dangerous attack ); but There are also similarities between them:
1. The anti-fraud center application is clearly informed and forced to be installed by the target population, so it does not require exploits or intrusions to achieve perhaps the same intrusive surveillance capabilities. Thus, security practices and digital literacy that might normally be effective in avoiding spyware and other similar threats may not necessarily be useful here.
2. Spyware is highly targeted and is used as a tool to meet specific repressive strategies, targeting dissidents, opposition parties, opposition groups, independent rights organizations, investigative journalists, human rights lawyers, political opponents... that is, Those individuals and groups who are clearly suspected of threatening the stability of the ruling class's power. Of course, that includes other people around them who have a relationship with those targets (remember the story about the can of protein powder ?).
However, forced installation of applications such as the Anti-Fraud Center does not seem to have a clear target group, and it tries to impose itself on everyone. This is consistent with the JingWang (Clean Network) application that is compulsorily installed in Xinjiang - it claims to combat certain evils, but it presupposes that "everyone has the necessity/risk of being combated/prevented". premise; then its strategy is not to fight evil as it claims, but to fight you.
You will see in the audit conclusion below what this app does on your phone, it doesn’t matter if you don’t understand all the technical related conclusions, you just need to know that it is greedily collecting, its strategy The goal is data power—the hoarding of as much data as possible to bring about the most comprehensive control possible internally, and geopolitical competitiveness externally .
——Level 3——
Data is power, data is capital, and data is politics . Now it is data that plays the role of oil in the geopolitical battle for hegemony. If you don't understand this yet, see:
- " All Information is Strategic: The Geopolitics of Information "
- " All Your Personal Data is Political Data: What You Need to Know Before Moving to Democracy "
This is why China has “walls”; and more and more walls are being erected in different ways in countries around the world (see a detailed explanation here “ The Real Thing That Can Break Down Walls May Not Be Ladders: Balkanization and the Internet” Future "). Yes, walls are not meant to stop you from seeing something, or at least stopping you is not the primary strategy, that is, exclusion is not the primary strategy; on the contrary, full acquisition/collection and centralization is the real purpose.
This is the power that data black holes like the Anti-Fraud Center want to further consolidate.
As Cedric Durand, an economist at the Sorbonne University in Paris, puts it , the total concentration of digital lands is leading to a scenario that Stuart Mill had foreseen: a nation Every piece of land belongs to one owner. The widespread dependence of the masses on their digital masters appears to be “the future of liberal cannibalism in the algorithmic age.”
In other words, even if you install this app (and many others like it) and *do not* face the consequences of drinking tea, being arrested, or being jailed, your very act of installation is already significantly assisting the ruling class in consolidating power. You are playing the role of an accomplice.
3. Applications like the Anti-Fraud Center can blatantly appear on the Apple and Google app stores and rank at the top of the list due to significant downloads. No spyware can achieve this form of shamelessness, although they have similar or even identical intrusive qualities.
You might say that globally popular apps like WeChat, Facebook, etc. are second only to spyware in terms of their intrusive surveillance capabilities. Aren’t they also ranked at the top of the app stores? Yes, but their data power lies in the hands of surveillance capitalists, not governments; the struggle between governments and surveillance capitalists for data power has lasted for decades , from initial cooperation ( public-private surveillance partnerships ) to later intermediaries. characterized by mass surveillance systems (sometimes covert , sometimes overt , involving much collusion ), to more recently, frontal seizures of control disguised as “whistleblowing” (of which we will detail shortly ). What the Chinese government is doing now is basically equivalent to being a surveillance capitalist.
4. The biggest thing that anti-fraud centers and spyware have in common is that they both need to and can only be stopped through resistance movements. There is no other way. Maybe you think, "Can't it be installed in a virtual machine?", "Can't it be enough to develop a fake anti-fraud center application to fool me?", or "Buy two mobile phones," etc., but Unfortunately, these are not solutions. Maybe they will work for now, allowing you to board public transportation, enter your apartment, and conduct business in the public sector ( remember at all times, these are restrictions imposed on you! You are deprived of legitimate rights! ) , but none of them can stop the expansion and spread of evil. Soon, evil will expand to the point where all the above methods are ineffective, it will spread to become more ubiquitous, and no one will be able to escape.
It is always the ruling class that is afraid of you, not the other way around; yes, you read it right, this is not only because the ruling class is wary of and overreacts to every little disturbance in society, but also because control measures are always gradually strengthened , boiled in warm water, they have been testing society's reaction because they know that if we unite and fight back, they will be finished .
If we don't know something that even they know, we have no chance of winning.
As you rejoice in the respite you get with each tightening loop of rope around your neck, there's no doubt that you'll only be greeted by the next, tighter loop.
This is not defense. This is suicidal.

——Level 3——
Old readers know that IYP has been emphasizing two key points in the past two years:
- 1. There are no purely “domestic issues” . In other words, domestic problems cannot be solved if solutions cannot be considered on a global scale ( see here a concrete explanation of this point on the topic of this article; in conjunction with the above).
- 2. In a globalized world, all struggles are interconnected . The struggle in one place is the struggle everywhere. (We will have a long article showing this point again soon)
These two points hold true on all issues. This is especially true when it comes to digital security, where there are no borders.
Just like the weapons that Israel tested on Palestinian civilians and were later sold at arms trade fairs around the world as "battle-tested"; the surveillance technology that the Beijing authorities tested on the people of Xinjiang was later sold as "sufficient practical data." The gimmick is sold all over the world. (Don’t forget, China’s practices are also copied . See here “ How China’s “Xinjiang Model” Learns from the Counter-Insurgency Strategies of the United States, Britain and Israel ”). Such examples could fill a very long list, but the basic conclusion should already be clear to you - the experience of oppression in one place will become a template for oppression in many other places; similarly, the success of resistance in one place may also make a Or multiple means of oppression have failed in many countries around the world, which is why the success of every resistance is the success of all oppressed people around the world.
China is monopolizing ownership of zero-day vulnerabilities (we’ll have more on this soon. You can see why China is doing this here: The United States, China, and Russia: The Dark Web’s Most Powerful Nation-State Hackers ). It may mean that China's self-developed spyware will usher in a leap forward era, although it is not yet certain; and, the Hong Kong victims of Israeli spyware were discovered 3 years ago , in other words, you are better off forgetting what you know of geopolitical common sense, as they are not that good at predicting digital disasters (you can read our list-4, which has a section titled "Perpetrators - Who is helping China" with the worst documented complicity Mostly from American companies; the common sense that China and the United States are enemies does not apply here, and the ruling class has a common interest in dystopian dreams ).
So you know, the reason why we are more inclined to speculate that the forced installation of the "Anti-Fraud Center" app is a collective disaster for big data, rather than an individual disaster for VPN circumvention , in addition to the geopolitics of data power as mentioned above In addition to the reason for gaming, another reason is that the ruling class may also use the most advanced spyware developed by any country at any time to combat local dissent and opposition - the basis for them to do so already exists; but they must first know “Who is likely to be dissident and oppositional?” This is what large-scale data collection and large-scale surveillance can accomplish.
Please note that there are so many things that are and are being done for large-scale data collection and large-scale surveillance! Far from being an “anti-fraud center”. And when they are disguised as so-called "safety" , "fun" , and "convenience" , people tend to ignore their evil nature.
When we released the video below, a Chinese friend accurately pointed out that this is the threat of Minority Report:
Yes, the real threat of Minority Report does not start now, but in 2007 ; it is the main reason for the resistance to the big data movement in the past decade.
So, to reiterate the point of this article once again: What you need to fight is not an app, but the entire tyranny itself — the tyranny that surveillance capitalism feeds off endlessly, not just a nation-state.
IYP has always talked about security, and the audit report in this article is also for security purposes. However, real security does not lie in a technical audit, nor in possible defensive measures. True security depends on the resistance of the oppressed to tyranny, and all defenses are designed to preserve your ability—we assume it has—from dying in the cradle. But you can only be truly safe if you use this ability effectively.
Defense is not escape, but preparation for attack.

Thanks to OTF for assisting with this audit report. This report is mainly an audit of the andriod operating system, and the impact on the ios operating system has not yet been examined.
The following are the main conclusions drawn from the report.
——Level 1——
The application claims to help users detect fraudulent calls, text messages, and fraudulent software installed on their phones, and issue warnings to users. To achieve these functions requires extremely high application permissions, such as inspecting all applications installed on the user's phone, reading log information, reading SMS information, etc.; the application also utilizes many additional sensitive permissions: This includes, but is not limited to, accessing location, using the camera, recording audio, and writing to device and application settings.
Since the application must be registered with a Chinese mobile phone number, the technician responsible for the audit was unable to obtain a Chinese mobile phone number, so complete dynamic analysis could not be achieved. Therefore, most of the content of this audit was conducted through static analysis. A simple dynamic analysis of the accessible parts was performed without registering an account.
The app's user privacy policy states that some services require users to provide sensitive personal information to work properly, but if users don't provide that information, other features should still work. For example, the policy states that users can choose whether to take advantage of the app's virus scanning feature; it also claims that users are not required to use the "authentication" feature, which collects facial recognition features and sends them to a third-party verification agency . The application utilizes the Cloudwalk Technologies software package for facial recognition.
The version of the app analyzed in this report is Android version v1.1.7.
Here are answers to some key questions.
1. What data does the app collect? What does it monitor?
The application can collect a large amount of user data and activity information, both in the background and directly from user input. Upon initial launch, it asks for permission to make and manage phone calls; access location; and access photos, media, and files on the device. Additionally, each request to the main API contains a wealth of user and device information, including:
- Android unique device ID
- Operating system version
- Operating system type
- Operating system brand
- Operating system model
- Application version
- IMEI, MEID, ESN or Android device ID
- Umeng device token
- Node ID
- Node Code
- latitude and longitude
- address
To register for the app, users must provide their phone number and location and set a password. The registration request transmits the following information to the server:
- telephone number
- SMS verification code
- password
- Application version
- Android version
- IMEI
- Requested IP address
- Region ID
- Police User PCode
- Police User ID
In order to authenticate using the app, users must also submit:
- ID photo and current facial image
- Name
- identification number
The app appears to utilize software from facial recognition software company CloudWalk Technology. The company has already been sanctioned for mass surveillance and human rights abuses. For more related content, please see " Illustration of China's Technology Giants - Half of the "Man in the High Castle"" .
The App also utilizes various third-party services to collect information in the background . The privacy policy specifically mentions Antiy Mobile for virus scanning and Umeng for tracking and analysis. The policy also states that app authors are not responsible for the data collected by these third parties. Various additional third-party services observed include Tencent Bugly for exception reporting and analysis, Amap for geographic data, and openinstall for statistics and application installation. (For details, see the appendix to the original report)
Many of the application's core features require sensitive permissions to enhance or modify user actions. Some of these permissions allow the app to read and receive text messages, and are required for the user's ability to report "text message fraud or scams." The app also makes use of a broadcast receiver, which has the ability to receive text messages containing various content, such as "malicious links." The app has the ability to record calls, as well as access call logs and contact information. Users can also reject and/or report unrecorded calls.
2. How does the app collect data? Can users prevent collection by changing permissions?
The application both collects data in the background and transmits data when manually requested. Data is sent to various domains via HTTP requests. In initial dynamic testing, the main domains accessed by the application were:
- fzapp.chanct.cn
- fzapp.gjfzpt.cn
- fzapph5.gjfzpt.cn
Initial dynamic testing consisted of manually using the application as a normal user while intercepting all network requests and performing packet captures to observe additional traffic. The application utilizes certificate pinning, so a Frida script is used to intercept HTTPS traffic. Features available to non-registered users include setting region and location, logging in, registering, forgotten password recovery, viewing the user agreement, and liking social media accounts (not tested).
As mentioned above, third-party libraries in this application collect and transmit data. Antiy Mobile Antivirus and Umeng Statistics and Analytics are specifically mentioned in their privacy policy. In the dynamic test described above, the application sends data to the following additional domains:
- 14.215.158.61:8002
- 203.119.204.254:80
- aaid.umeng.com
- adash.man.aliyuncs.com
- amdcopen.m.taobao.com
- cgi.connect.qq.com
- dns.qq.com
- dualstack-arestapi.amap.com
- login.sina.com
- openinstall.io
- restsdk.amap.com
- stat.openinstall.io
Additionally, when the app is not granted location services permission, every API request includes latitude and longitude values of 0. The limitations of this test make it impossible to determine the effect of denying or revoking permissions for all applications. But users have previously reported that denying all permissions causes the app to crash.
On launch, the app asks for location permission, access to storage, and a phone call. Denying these three permissions did not appear to prevent the app from functioning during pre-registration. The application requires additional permissions to achieve full functionality; these permissions will be required at different stages of use; these stages could not be tested during this audit.
3. Is it possible to completely prevent the application from reading information from the phone by using the Xposed module XPrivacyLua?
As mentioned before, the audit team can only dynamically test app behavior before user registration, but cannot test daily use. This is because a Chinese mobile number was not found to register for the app. The details below are a dynamic test of the accessible parts of the application.
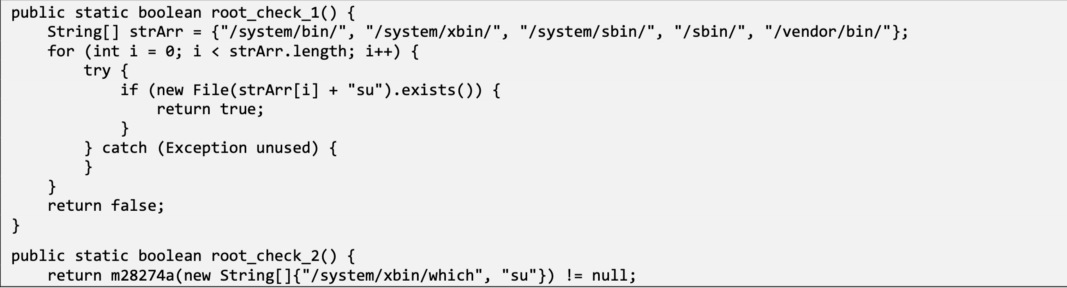
The test device has been refreshed with a custom userdebug version. Attempting to run the application failed with a message that the application does not support rooted devices. The following root checks were found:
After installing the Xposed framework and RootCloak module, these checks were bypassed and the application was launched. The XPrivacyLua module is installed and configured to provide data to the target application. The usable portion of the application still appears to be functioning normally at this time. The data sent with each request, such as latitude and longitude, is generated by the XPrivacyLua module. The module itself shows that on the initial configuration screen the application attempts to access the following data.
- Get the apps installed on your phone
- Get location data
- Get sensor data
- Read identifier
- Read network data
- Usage tracking
A code audit showed that these accesses were not limited to the initial configuration steps.
Additionally, various GPS forgery and device ID spoofing tools can successfully feed data into the application.
4. If Xposed and XPrivacyLua prevent an app from reading user information, will the app alert the authorities and get the user into trouble?
The only place where the app seems likely to report about users using the Xposed framework is the Tencent Bugly crash reporting service.
This function is trying to detect the Xposed framework:
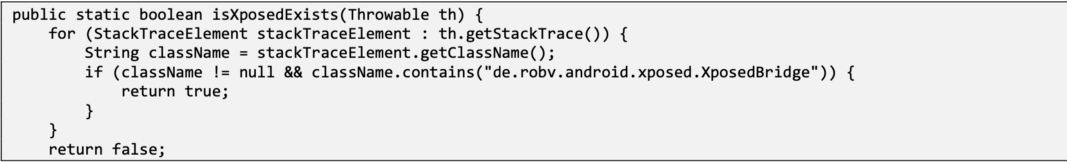
Additionally, com.tencent.bugly.crashreport.common.info.C3194b (obfuscated name) checks the de.robv.android.xposed.XposedBridge and de.robv.android.xposed.installer packages.
One of the checks is to scan /proc/<PID>/maps for .jar and .so files with xposed in their names.
These checks seem to only search the original Xposed framework package. Alternatives like EdXposed and LSPosed may bypass these checks without being reported . EdXposed was tested in this audit; its package name is org.meowcat.edxposed.manager and it was not discovered by the application.
Tencent Bugly also checks the existence of the com.saurik.substrate package in a similar way.
5. How can users avoid being monitored and censored by the app?
If citizens were required to install the app on their phones, some of the methods discussed in this report could help protect users' privacy; specifically revoking or denying permissions and leveraging the Xposed framework or other root techniques to hide information. It is important to understand that these methods do not guarantee privacy or anonymity and may be discovered. Any possible consequences of completely blocking the app's functionality are currently unclear.
Of course, the app may be updated and gain additional or more effective detection, such as more advanced root detection, broader Xposed framework detection, and broader reporting of privacy features. If the current app detects that its version is out of date, it will prompt the user to download the latest version from https://oss.chanct.cn/preventfraud-static/apk-nationalapp/national-antifraud.apk . The app also includes the Tencent Tinker library, which describes itself as a "hotfix solution library for Android that supports updates of dex, libraries, and resources without reinstalling the apk." That said, this library may be used in the future Used to update the app's functionality even if the user refuses to install the newer version.
The application can also perform actions such as writing system settings and installing applications, which can easily be used for nefarious purposes . It's important to pay attention to what permissions installed applications ask for, and to deny and revoke unnecessary permissions whenever possible. (See the relevant detailed instructions here " Do you really understand what application permissions are granted? Here is important knowledge to protect your security ")
Another option for users may be to upgrade to Android 12, which includes new privacy features that notify users when an app accesses sensitive permissions such as microphone, camera, and location. However, please note that mobile operators who control the phone's software may remove or block these features.
This audit saw no indication that the app looked for VPN usage, or exposed users leveraging VPNs to access blocked content. However, given its broad permissions, including the ability to query and scan all installed packages, meaning the ability to find VPNs may be added in the future and no additional permissions will be required. In addition, virus scanning capabilities can include detecting the signatures of legitimate VPN applications.
People seem to have a misunderstanding here, thinking that the use of a VPN will be exposed only if something is installed on the phone or if the phone is intercepted by the police. In fact, this is not the case. Your ISP knows that you are using a VPN. The different results just depend on whether they care. . ISP is the biggest disaster, but it is often ignored by people. This is a mistake.
——Level 4——
Each of us is promised complete self-determination: all institutions of society are expected to honor it. You are born with the right to self-determination, not because it was bestowed upon you by anyone, but because not even the most totalitarian dictatorship can take it away. Because you will resist, you will rebel, and your desire for autonomy is as hard to cover up as a sneeze.
All ruling classes from ancient times to the present are constantly learning how to deceive their people, quietly and step by step depriving people of their right to self-determination, disguised as "security", "convenience", "modernization", "fashion"... " I’m good for you”, making obedience “natural”. The ruling class is the biggest fraudster. The media they control amplifies their voices and aims to manipulate you into forgetting your rights and desires; all your passions and hobbies may be questionable and the result of being induced. They are the most successful scammers. They make you run towards their ideals willingly and forget your own.
If you really hate scams, start by seeing through the scams of the ruling class.

The ruling class likes to talk about "personal responsibility", but if you took full responsibility for all your actions, would you obey their instructions in the first place?
In the digital age, the ruling class has penetrated into every corner of everyone's life to an unprecedented depth, not just an application ; algorithms rule what you see and hear, thereby dominating your cognition ; ISPs rule your connections The ability to cut off your connection and block your mouth when you need the help of teammates and make a sound the most; big data monitors all your life, understands your desires, peeks into your inner thoughts, and even predicts you What will happen in the near future ... In this case, obedience and voluntariness have become increasingly difficult to distinguish - just like when I tell you about Clubhouse that collects your voiceprint and TikTok that collects your facial data Will you pay attention to me when Facebook, which manipulates your perception , is evil and something you shouldn’t install and use? In fact, there is no essential difference between their evil and the forced installation of the "Anti-Fraud Center" and the forced installation of the "Learning Power" - in terms of your human rights and security.
All the while, you have forgotten your own interests and you have given in to too many of these evil scams. The only difference with Anti-Fraud Center is that it comes from the devil you know, selling it to you in a way you're familiar with. You should not be coerced, just as you should not be deceived, it is your right to self-determination, your basic human rights and personal security.
As you can see, narrow-minded and short-sighted people will break down and compress systemic problems into specific group/individual problems - they do not see that corruption is a chronic disease of the government, but only criticize a certain government and individual politicians ;Similarly, they don’t see the disaster of surveillance capitalism, but just rage about an app. This is definitely not to say that a certain politician and a certain application are not worthy of attention, absolutely not, otherwise this article would not exist at all; but, if you ignore the root systemic problems, you will not be able to solve all individual problems, and there will always be next A more evil politician and a more dangerous app.
This is not just a centralized internet, but a centralized world that requires decentralized solutions. If we want true freedom and democracy, we must intervene in all the processes that defraud us - from online to real life.
We must abandon an oppressive regime altogether , not try to manage the details of it "fairer"; not change who is superior and who is subordinate, nor just get hung up on a few authority settings; the purpose of rebellion is not to seek More legitimate rules or more affable rulers, but to demonstrate our own capabilities, the true power of “we the people.” That is direct action .
If you ask "What is layer 4", Hong Kong people have already done it. We have pinned this good news to the top of the " The_New " section of this site " "We want to try a life without hegemony": Interviews with Hong Kong activists " .
We have previously uploaded a podcast " Centralized Problems Need Decentralized Solutions " and discussed " From Democracy to Freedom ", which can help you understand the meaning of this fourth layer. Always remember that you have the right to self-determination, you can say no, you can rebel, and you deserve and deserve the world you want.
IYP is always on Tier 3 and Tier 4 , waiting for you. ⚪️
⚪️
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More