Reading Bigeng|What is a cryptocurrency wallet? Mnemonic phrase ≠ seed ≠ private key
This article is excerpted from the popular blockchain science website "Chainee" . What is a cryptocurrency wallet? What are the differences between exchange wallets, hot wallets, and cold wallets? Which one is suitable for me? In this article, let’s clarify the concepts related to “cryptocurrency wallet”.
👉Collect the Writing NFT version of this article👈

Cryptocurrency is a new type of digital asset. You can think of it like the New Taiwan Dollar or the US Dollar. We usually keep cash (fiat currency) in bank accounts, and electronic cash such as Bitcoin, Ethereum, and U.S. dollar stable coins (such as USDT, USDC) also need to be stored in a cryptocurrency wallet (Cryptocurrency Wallet).
This article will tell you everything you need to know about "cryptocurrency wallets", including what is a cryptocurrency wallet? The components, operation methods and classification of cryptocurrency wallets. Before you start trading cryptocurrencies, you must first learn how to securely protect your cryptocurrencies.
Further reading: What is cryptocurrency? What is virtual currency? Explore the characteristics and types of cryptocurrency in one article!
What is a cryptocurrency wallet?
Cryptocurrency wallet is a digital wallet used to store, send, and receive cryptocurrency. It is the most basic part of crypto financial facilities. Users can use this to participate in various applications of blockchain technology, such as participating in DeFi, NFT, GameFi... transactions .
Going back to 2008, when Satoshi Nakamoto invented Bitcoin , he told everyone in his paper that the Bitcoin protocol is a "Peer-to-Peer" decentralized electronic cash system. You can understand "point-to-point" as "person-to-person" without any third party. In other words, the vision outlined by Satoshi Nakamoto is for everyone to hold their own assets , rather than placing assets in custody in a third-party centralized institution.
In order to understand more clearly what "holding your own assets" means, we must first clarify how a cryptocurrency wallet operates and understand the components of a cryptocurrency wallet.
How cryptocurrency wallets work
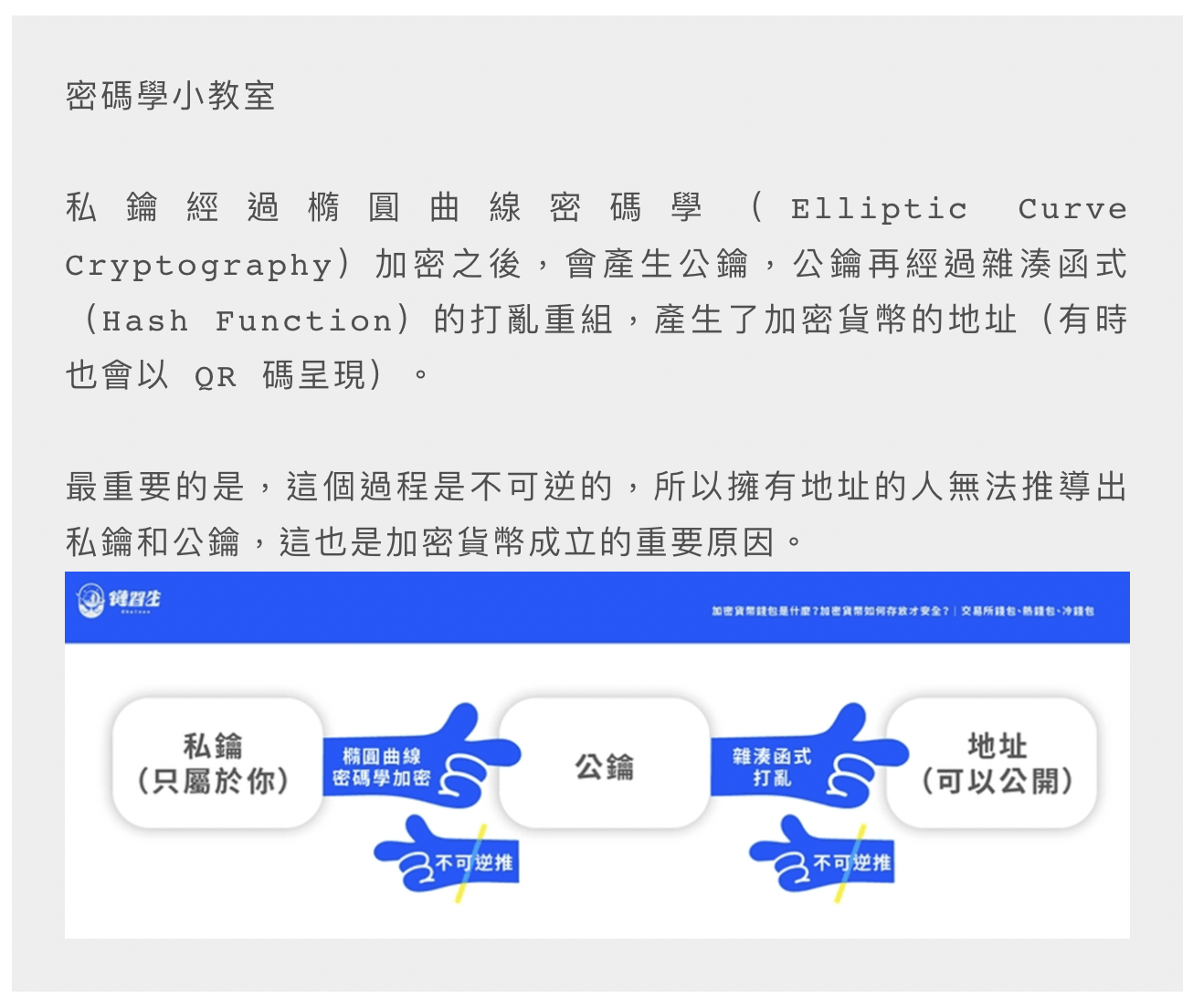
≣ Private key, public key, address
In the world of cryptocurrency, Private Key, Public Key and Address are indispensable elements. They are the beginning of everything and jointly establish the security and functionality of cryptocurrency wallets. cornerstone.
The relationship between the three is "private key → public key → address" and is one-way and irreversible.
Private keys and public keys, no matter what they are, have the dual purpose of encryption and decryption (explained later).
The address is the destination used to receive cryptocurrency when transferring money, similar to a bank account number.
Let us elaborate further.
≣ Relationship between private key and public key
Quoting an article titled " Public-key cryptography for non-geeks " by technology developer Panayotis Vryonis, let us further explain the "relationship between private keys and public keys".
Please imagine that Brother Nao has a safe with a "special lock" and the key can be turned in three positions. Among them, turning to position A and position C will lock the safe, and turning to position B will open the lock; this kind of safe has "two" different keys. The first private key can only be rotated clockwise (from A → B → C), and the second public key can only be rotated counterclockwise (from C → B → A).
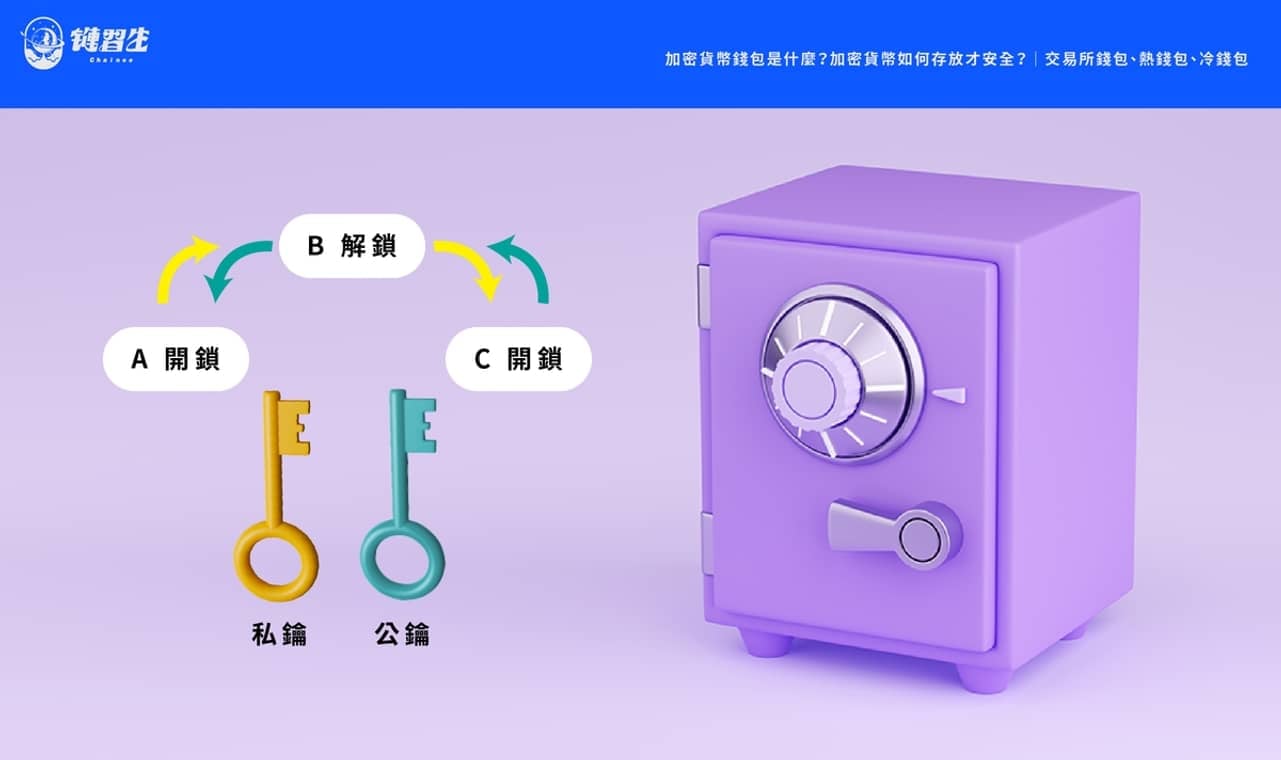
In the above metaphor, a safe and two different keys are mentioned. The corresponding concepts of these three items are as follows:
The safe <br class="smart">represents the use of "asymmetric cryptography" encryption technology (Asymmetric cryptography). In the practical application case explanation below, putting confidential files into the safe is like using encryption technology to target the file. encryption.
A key that can only be turned clockwise <br class="smart">Nao's "private key" is only owned by Nao and is not disclosed to the public.
A key that can only rotate counterclockwise <br class="smart">Nao Ge's "public key". Anyone can obtain Nao Ge's "public key" and it can be made public.
In other words, "Brother Nao's private key" can be transferred from A to B and then to C, while "Brother Nao's public key" can be transferred from C to B and then to A. Now we can see some interesting uses:
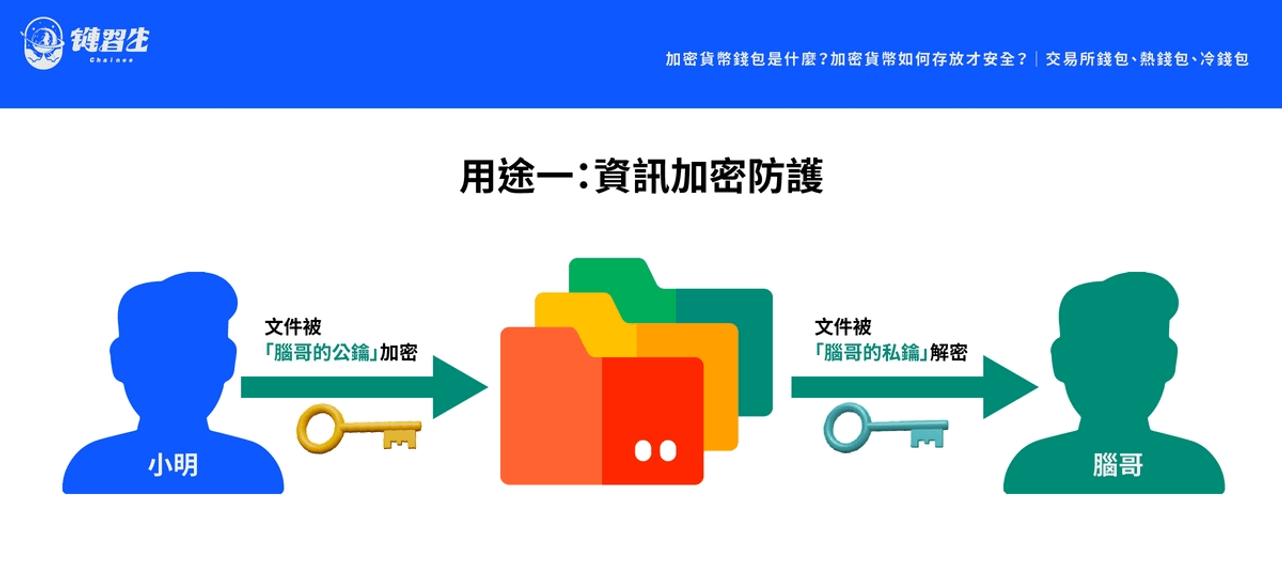
[Purpose 1: Information Encryption]
Ensure the data transmission process is safe and secure
Suppose Xiao Ming wants to send a confidential document to Brother Nao. Xiao Ming puts the file in a special safe and uses the "public key" disclosed by Brother Nao to lock the safe (from C to B and then to A).
At this time, only Brother Nao in the world can open the safe and use his own "private key" (from A to B) to unlock it, ensuring the security of the data transmission process.
This is the so-called "public key cryptography" technology, which protects the transmitted information itself through "public key encryption and private key decryption" so that only the owner of the private key can read it.
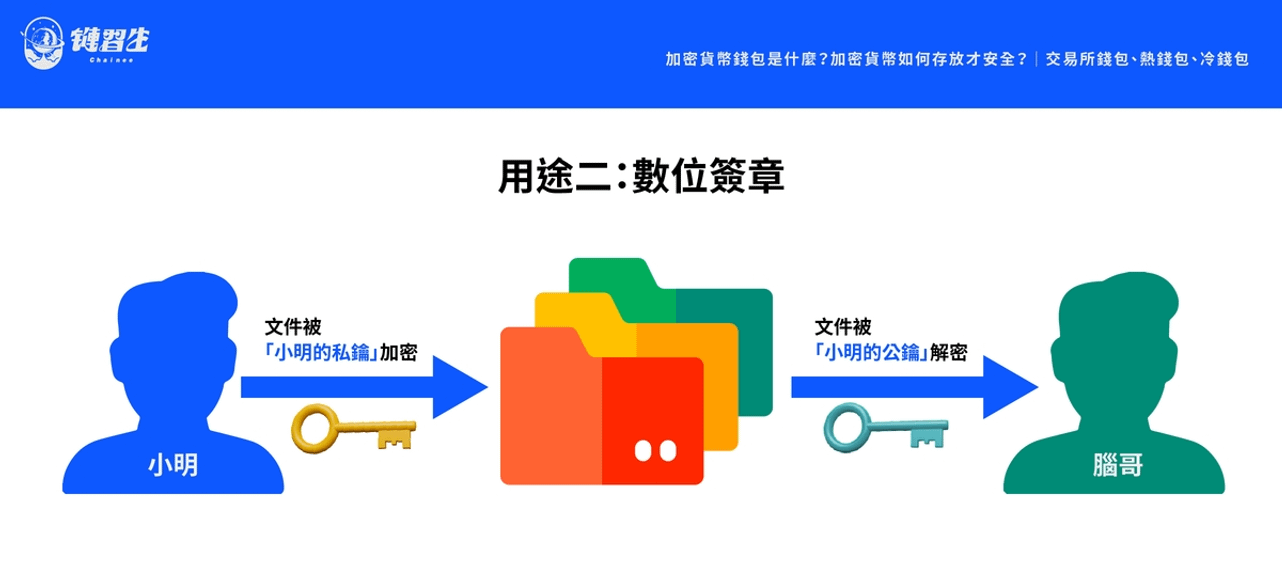
[Use 2: Digital signature]
This proves that this document was sent by Xiao Ming himself
Another point we are curious about, how can Brother Nao confirm that the confidential documents were really sent by Xiao Ming?
It's easy to prove that confidential documents were indeed sent by Xiao Ming! Just put the safe locked with Brother Nao's public key into another safe (box-in-box), and lock the outer safe with Xiao Ming's own "private key" (from A to B and then to C).
Since the safe locked with Xiao Ming's "private key" can only be opened by Xiao Ming's public key, when Brother Nao receives the safe, he only needs to use Xiao Ming's public "public key" first and turn the key to the left (from C → B), if the outer safe can be opened, it can be confirmed that this document was sent by Xiao Ming himself, because only Xiao Ming himself can lock the outer safe (private key).
Such an action is called "Digital Signature". This is another use case of "public key cryptography" technology. It uses "private key encryption and public key decryption" to prove the legitimacy of the message publisher and verify that the signer of the digital signature is the signer himself.
Reviewing the above concepts, in the blockchain world, using public key encryption is like putting funds into a safe. If you want to open the safe, this action is to decrypt the private key. Whoever holds the private key is the owner of the safe, and whoever is qualified to use it Money; on the other hand, using private key encryption means that the sender signs before the funds are transmitted to ensure the identity of the transaction initiator.
Private key (not public)
Private key encryption = Decryption of the private key digitally signed by the transaction initiator = Control of the cryptocurrency wallet is kept properly and must not be made publicPublic key (can be made public)
Public key decryption = confirms that the payer initiated the transaction. Public key encryption = ensures that only the recipient can use the funds.Address
Just like a bank account number, it can be made public if it is used to receive transfers from others.
Cryptocurrency wallet transfer example: one transfer, two encryptions
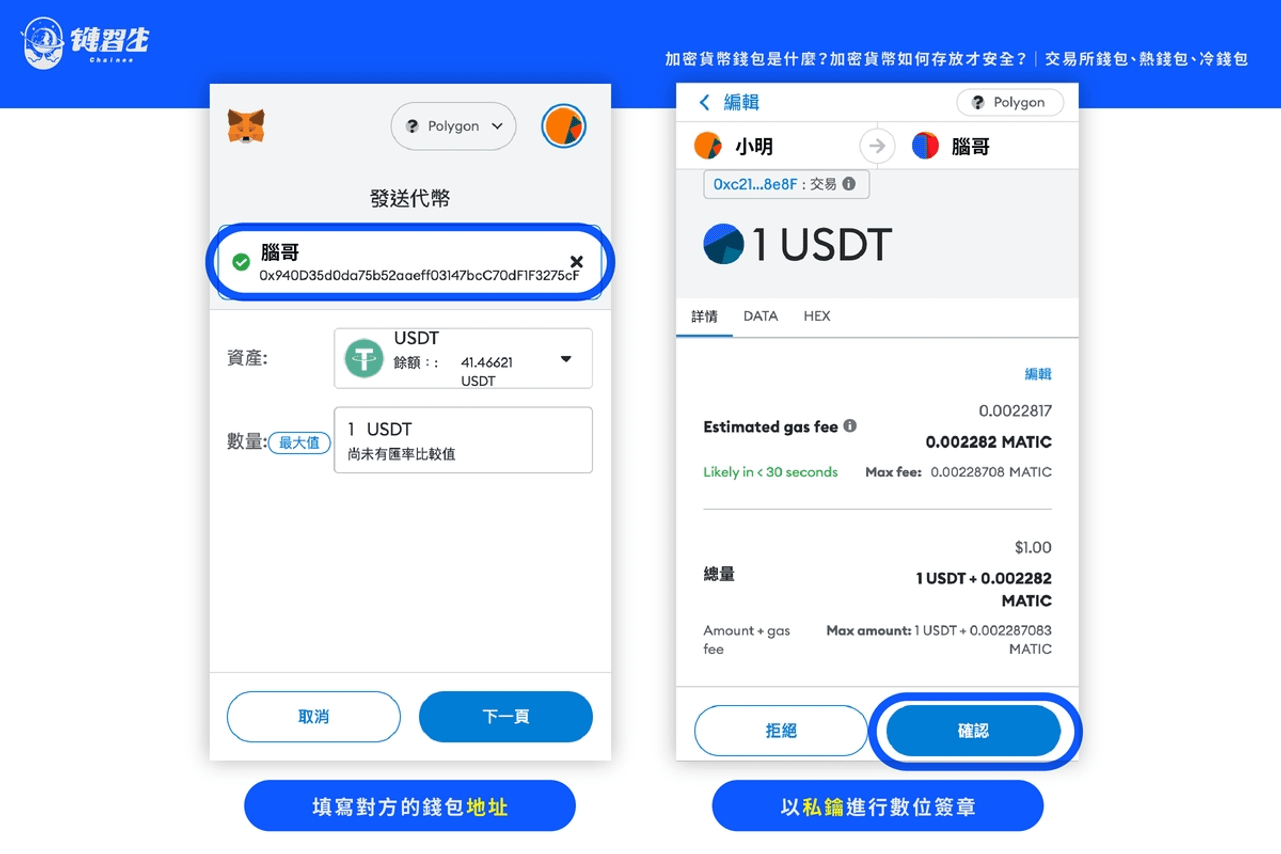
We use "Xiao Ming sends 1 stable currency to Brother Nao" to illustrate the cryptocurrency wallet transfer.
First, Xiao Ming must fill in Brother Nao’s wallet address . The wallet address is generated by Brother Nao’s public key, so sending funds to Brother Nao’s wallet address is equivalent to using the “Brother Nao’s public key” to encrypt the transaction to ensure that the funds are delivered. , because only Brother Nao has the "Brother Nao private key", which ensures that only Brother Nao has the right to use the money.
At the same time, Xiao Ming also used the "Xiao Ming private key" for digital signature (encryption) confirmation, conveying that the transfer was sent by Xiao Ming. Next, the miners on the blockchain will verify the transaction and use "Xiao Ming's public key" to check whether the transaction was initiated by Xiao Ming and whether it was signed by Xiao Ming using a digital signature. The authenticity and legitimacy of the transaction. If the verification is correct, the transaction will be established and written into the block.
In other words, Xiao Ming first encrypts the funds to be transferred with Xiao Ming's private key (digital signature), and then encrypts them once with Nao Ge's public key (information encryption). After these two encryptions, the funds are transferred to Brain brother.
Cryptocurrency Wallet Seeds and Mnemonic Phrases
If you have experience using a wallet like MetaMask , you may have some confusion at this moment: "Why haven't we introduced the mnemonic yet?" "What is the mnemonic? Is it the same thing as the private key?" "Why MetaMask can generate a large number of wallet addresses from just one wallet"... The following will be explained in order.
Next, let us further extend the discussion from "private keys" to complete the review of the development of cryptocurrency wallets.
≣ What are seeds?
Seed is a randomly generated string sequence used to generate public and private key pairs (Keypairs) for cryptocurrency wallets. One seed can generate many private keys .

In the process of using cryptocurrency, you may want to use different wallet addresses in different situations due to dedicated funds, security considerations, etc. However, if each address needs to correspond to a different private key, this will cause trouble in managing private keys.
As a result, Proposal No. 32 of the Bitcoin community appeared, which defined the "Hierarchical Deterministic Wallets (HD Wallet)" architecture currently adopted by the mainstream, allowing a single seed to generate a tree structure to store a series of public and private key pairs, and then Further generate a series of wallet addresses.
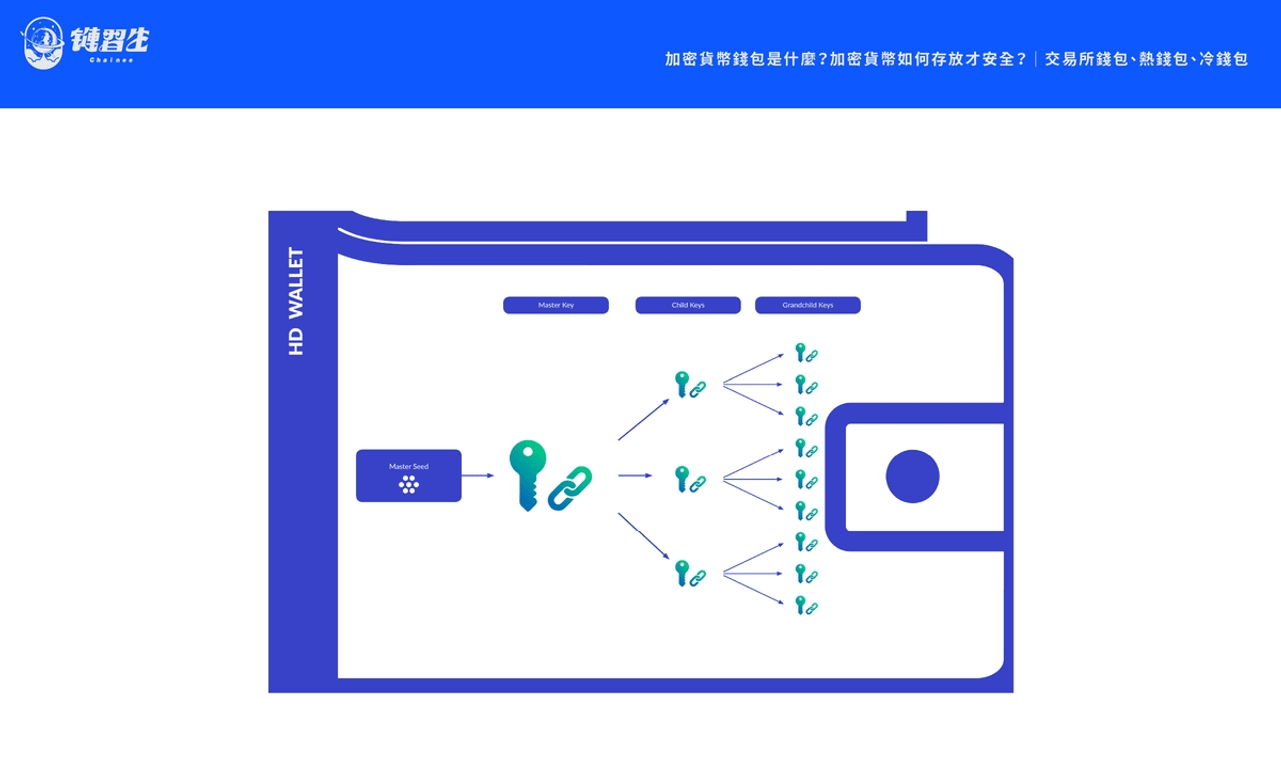
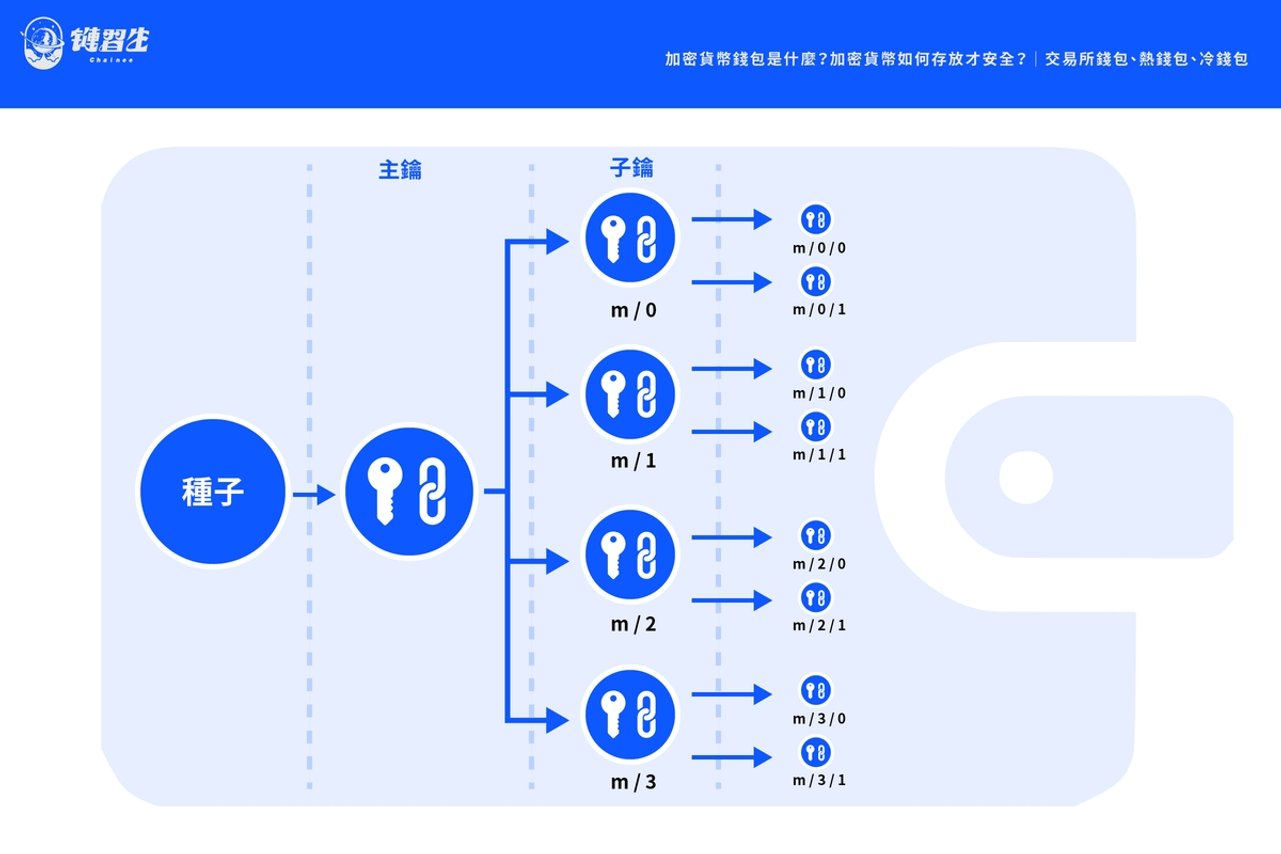
The advantage of this is that users only need to back up a set of mnemonic seeds and can easily restore the entire wallet without having to back up each private key individually.
≣ What is the mnemonic phrase?
The mnemonic phrase is another representation of the private key.
The most original appearance of the private key just mentioned is 256 bits (256 0s or 1s), which takes up a lot of space. If expressed in hexadecimal, it can be shortened to 64 strings, each of which It is randomly generated from the group words 0-9 and the uppercase and lowercase English letters AF.
It is very difficult to remember this long and irregular list of private keys. Therefore, some people began to explore more convenient ways to back up and remember private keys. Later, someone proposed to use the "protocol-defined word list" to derive the private key. In this way, we only need to write down a few groups of simple English words, which is equivalent to writing down a string of irregular private keys. This is the mnemonic word (mnemonic phrase). phrase, recovery phrase, seed phrase).
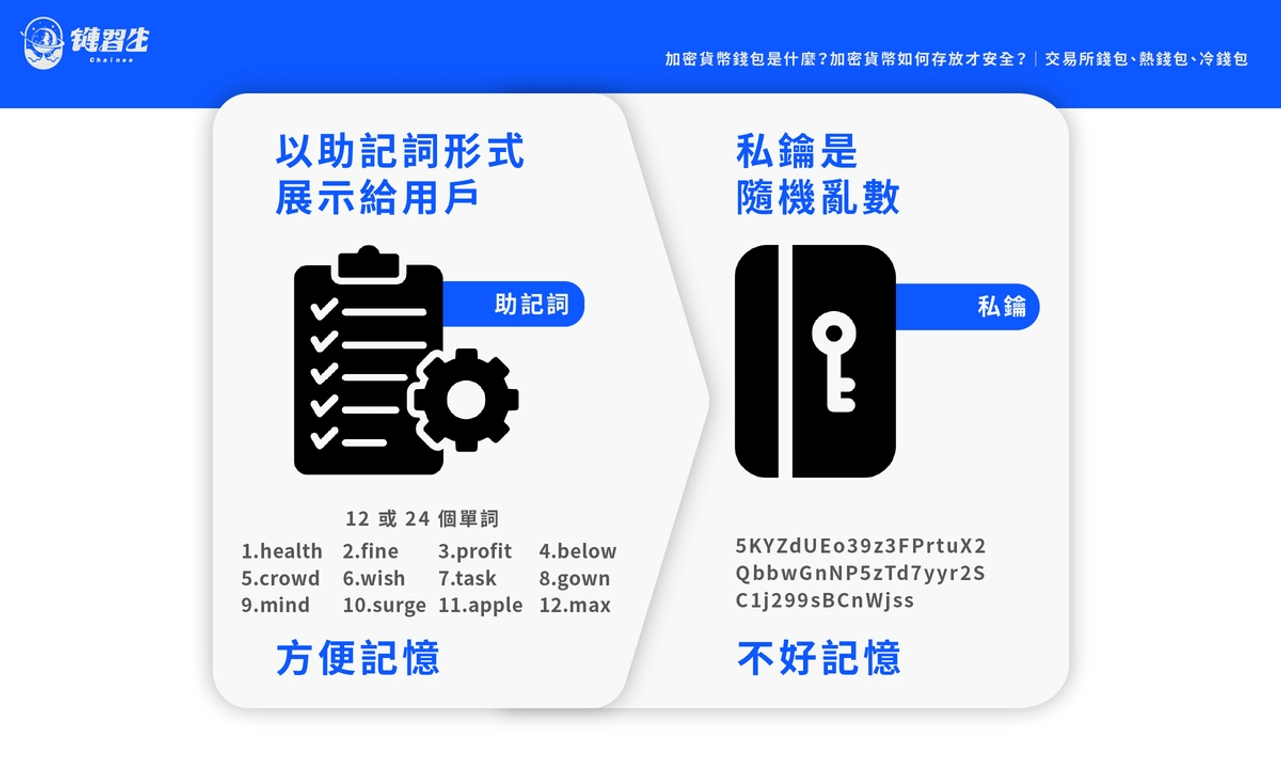
Cryptocurrency wallets will provide a backup mnemonic phrase, usually 12 or 24 words. Please handwrite it on paper in order (it is recommended not to take screenshots, take photos or store it in the cloud to avoid leakage) and keep it properly. When the device is lost or malfunctions, the mnemonic phrase can help you recover your wallet and digital assets.
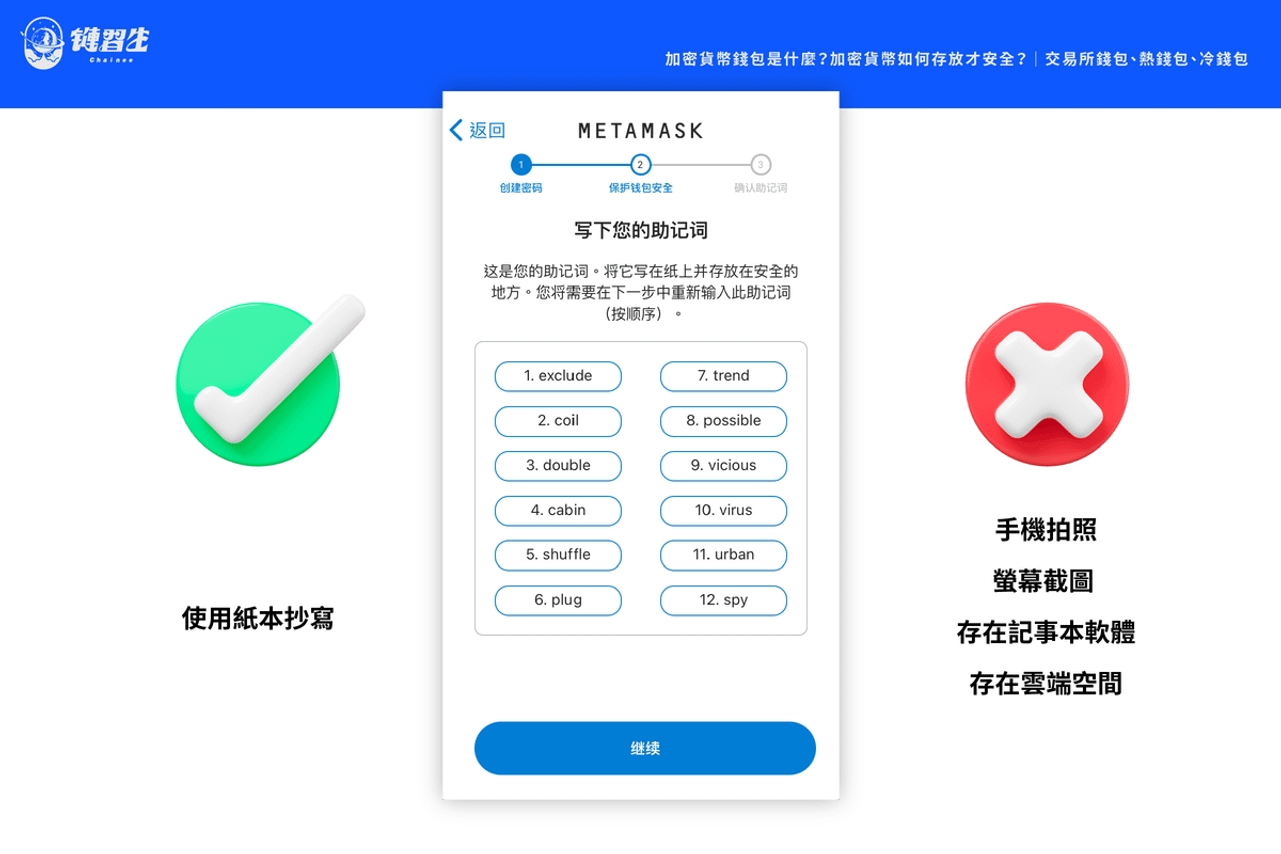
Reviewing the above discussion, we can clarify an important concept: although mnemonics, seeds and private keys are expressed in similar ways, strictly speaking, they cannot be equal to each other, which means:
Mnemonic phrase ≠ seed ≠ private key mnemonic phrase → seed → private key → public key → address

In general, based on the Bitcoin community's Proposal No. 39, we can use "mnemonic words" to generate "seeds", and then through Proposal No. 32, we can derive a large number of "public-private key pairs" and "wallet addresses".
Note: In addition to the above, there is also Proposal 44 , which allows addresses derived from the same seed to support "multi-currency, multi-account" and other functions, further optimizing the development of cryptocurrency wallets. This article only briefly mentions it, and interested readers can delve into it on their own.
With the above background knowledge, we can experience this process on the " Mnemonic Code Converter " mnemonic phrase generation website. It can be clearly observed that the mnemonic phrases not only help "mnemonic" the private key, in fact they are derived The "source" of the private key.
Cryptocurrency Wallet Classification
After understanding the background knowledge of cryptocurrency wallets—private keys (mnemonic words generate seeds, and seeds generate private keys), public keys, and addresses—we followed the context of “ private key control ” and made plans for cryptocurrency wallets. The following categories:
≣ Exchange wallet
The private key (mnemonic phrase) of the exchange wallet is controlled by a centralized organization.
When newbies join the cryptocurrency community, they usually register an account at a "centralized" cryptocurrency exchange such as Binance and OKX. In this case, although the exchange will generate a cryptocurrency wallet for you and provide the wallet address, you do not hold the private key to the wallet because the private key is kept by the exchange .
Extended reading: Binance exchange registration tutorial
Therefore, your assets are actually hosted on the exchange. You only have the permission to "log in and view" the wallet balance, but do not actually obtain ownership of the wallet . This is similar to the concept that when buying and selling stocks in the traditional financial circle, funds are held in custody at the securities delivery account.
Putting assets under custody in a third-party "centralized" institution makes daily operation and management convenient, and the experience is similar to placing orders and buying and selling stocks online. However, it also exposes assets to the risk of "something goes wrong on the platform," which can cause the funds to be temporarily A permanent freeze, or even permanent closure of the exchange, such as the recent thunder storm on the FTX exchange at the end of 2022, and the earlier Mt. Gox exchange hack in 2014... Remember, Not Your Keys, Not Your Coins.
≣ Hot Wallet
Hot wallets allow you to keep your private keys (mnemonic phrases) by yourself. The private keys are stored in online software and require an Internet connection to use them.
When you have accumulated some experience in the currency circle and are out of the novice stage, you may have heard of hot wallets like Metamask. A hot wallet is a cryptocurrency wallet that runs on "computers, mobile phones and other Internet-connected devices". It can be a plug-in for a computer browser or an app on a mobile phone.
After the hot wallet is installed, we can use it to transfer, receive money, and connect and interact with various decentralized applications (dApps). The current situation is that the private key is stored in your software, and you can check it at any time and copy it down for backup, so that the private key is kept by you; in this way, we have complete control over our own wallet and keep our own. assets.
However, it should be noted that since the private key generation, storage and use of hot wallets are all connected to the Internet, the risk of being attacked by network hackers is high and it is not an absolutely safe solution.
For example, MetaMask, Phantom Wallet, OKX Web3 Wallet, Trust Wallet, and Coinbase Wallet are all common and popular hot wallets in the cryptocurrency field.
≣ Cold Wallets
Cold wallets allow you to keep your private keys (mnemonic phrases) by yourself. The private keys are stored in physical hardware and will not be connected to the Internet when used.
More advanced users are beginning to seriously consider buying a cold wallet, which looks like a flash drive, a credit card or even a piece of paper. The biggest difference between a cold wallet and a hot wallet is that the generation, storage, and use of private keys are not connected to the Internet. Instead, they are stored in a physical hardware that is "isolated from the Internet" and are kept by you . Naturally, no private keys will be hacked. It's possible to go.
In actual use of cold wallets, when authorization is required to perform any transaction, we need to "take out" the physical cold wallet to operate. This feels like transforming the private key into a real physical key, and it has a real "feel" in operation. .
Another concept that needs to be clarified is that the cold wallet does not store tokens, but keeps your private keys. Your cryptocurrency assets are always recorded on the blockchain ; when you want to use these funds, digitally sign them. (Digital Signature) operations are performed on a cold wallet that is "isolated from the network." Your authorization is sent via USB or Bluetooth - not connected to the Internet - to the blockchain to complete the transaction.
Common cold wallet brands in the currency circle include CoolWallet, Ledger, SafePal S1, Trezor and ELLIPAL, etc. Lian Xisheng has a dedicated article to analyze and recommend these cold wallets from the perspectives of CP value, international popularity, and affordable price.
How to store cryptocurrency safely?
Having said this, you may be curious about the main differences between the three wallets and what are the risks associated with each?
We have compiled a table for you to review what was discussed in this article, comparing the characteristics of the three cryptocurrency storage methods of exchange wallets vs. hot wallets vs. cold wallets, and the sources of risks faced by each other:
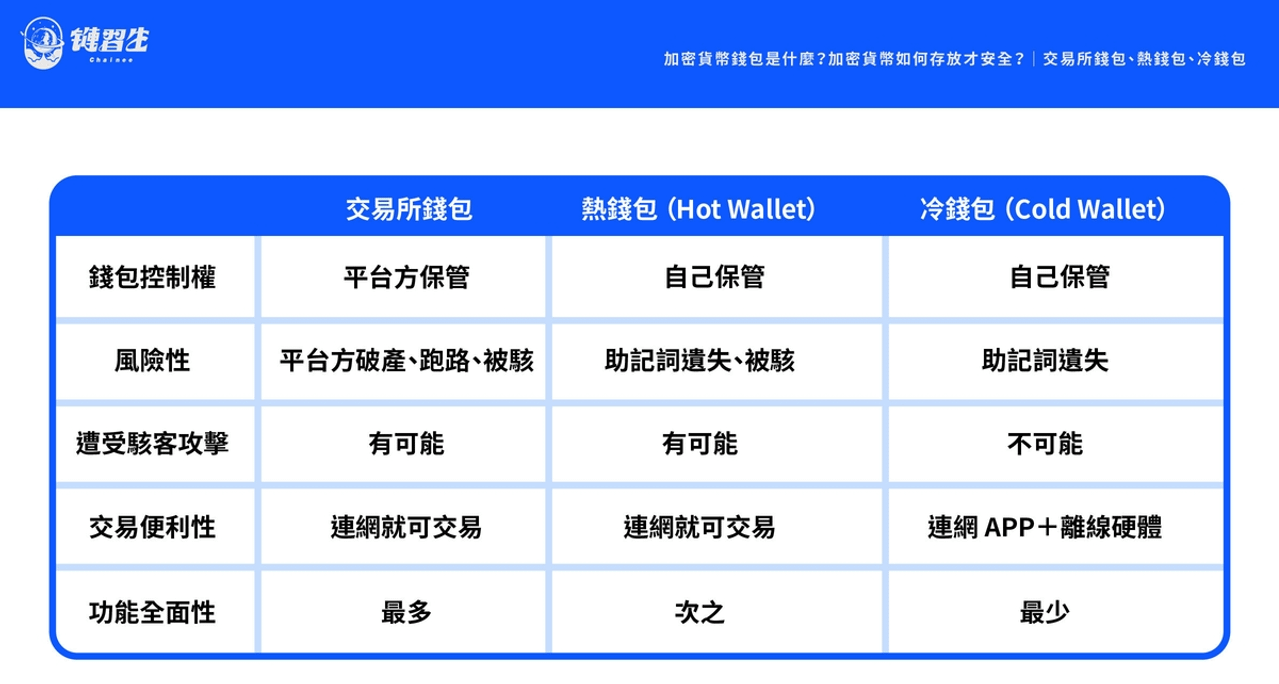
Following the previous discussion, we have understood that the so-called "keeping your own assets" means "keeping your own private keys".
To be honest, although the use of hot wallets/cold wallets to store cryptocurrency can avoid the risk of the platform going bankrupt (due to bankruptcy, running away, or being hacked), this does not mean that there is no risk in the future, but the risk has changed. Form exists . The risk is transferred from the platform to itself, from "bankruptcy" to the risk of "mnemonic loss or hacking".
However, this change has made risks from uncontrollable to controllable , which is already very valuable.
Which cryptocurrency wallet is right for me?
In fact, we can classify our funds:
Cryptocurrencies that are used for "frequent transactions" on a daily basis can be stored in exchange wallets that have multiple functions and are more convenient to use.
For other cryptocurrencies that are used for "long-term holding" and are not used frequently, it is recommended to store them in your own hot wallet/cold wallet, which is more secure.
I once heard someone suggest a pragmatic approach: rent a safe with a bank and lock your mnemonic phrase in it to prevent loss. But looking back, didn’t you say you should “keep your own assets by yourself”? Why did you turn to a third-party agency for help?
Perhaps as Changpeng Zhao (CZ), the founder of the world’s largest cryptocurrency exchange, commented:
Centralization and decentralization are not binary oppositions. Freedom and security go hand in hand .
🌱 Subscribe to the [ Creator Economy IMO ] newsletter for free.
🌱 Join [ Zhongshu Nervous System ] around the stove, and the special topics #Reflections on Writing and#热内真情are being serialized.
🌱 I appear on other platforms【 Meta | X | Liker Social | Matters | Medium | vocus 】
Cooperation contact: penfarming.writer@gmail.com
🌱 My instructional text and invitation link to register on Binance | Binance account opening + real-name authentication tutorial .
Register Presearch | Search to earn three birds with one stone. User experience .
Register Potato| Learn three things from Potato Media .
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!








- Author
- More