How to quickly find any country’s covert critical networking infrastructure
- It allows you to see everything like a hacker. It can draw global maps of SCADA devices, webcams and printers, even more powerful than Shodan, known as the "most evil search engine"
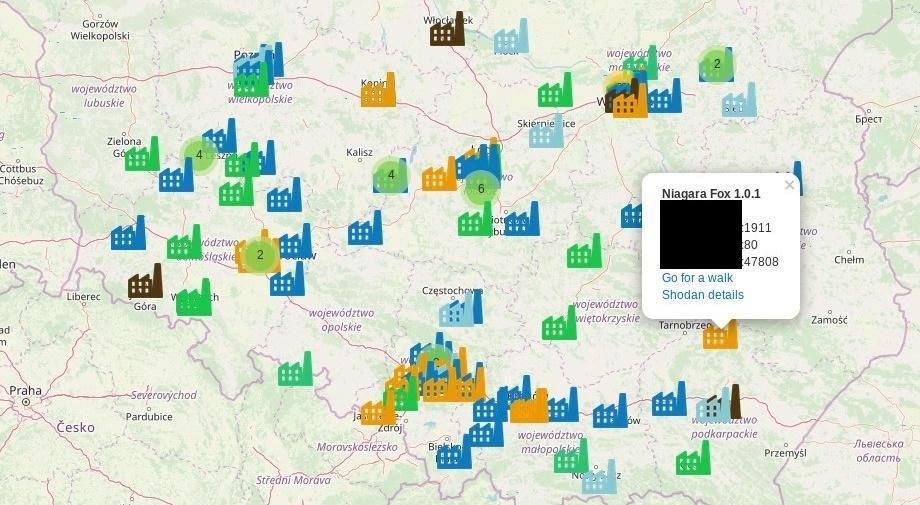
Polish security researchers have created an open-source intelligence gathering tool that indexes information about sensitive devices connected to the internet and plots their approximate locations on a map.
The researcher said he created the tool to allow organizations to scan networks and identify vulnerable devices, but the tool also has its drawbacks, as bad actors can use it to more easily carry out attacks.
KAMERKA
The tool was released last year and is called Kamerka (Polish for "camera"). The tool works on user-supplied search queries.
Kamerka takes these queries and searches for common brands of specific devices using search engines like Shodan and BinaryEdge, then plots the results on a Google Map.
- About Shodan " Super Shodan Search for Remote Desktops, Webcams, Printers, Home Devices... and Everything: A Horrible Guide "
In its initial release, Kamerka only scanned surveillance cameras, but the tool has been updated several times over the past year. The current version can scan and identify all of the following:
- Internet-connected surveillance cameras
- Networked printer
- ICS/SCADA Industrial Equipment
- Systems and sensors that work on top of the MQTT protocol
- A device that broadcasts real-time video streams based on the RTSP protocol
- Tweets, Instagram posts and Flicker images with geolocation details
Kamerka collects all this information, collects it in an Elasticsearch database, and then plots it on a Google Map.
For each device plotted on the map, users can click to view a tip with exposed ports and various other metadata .
Until late last year, you could only run Kamerka searches through a difficult-to-use Python command-line script. But that will soon change.
The tool's creator, a researcher named Wojciech, told ZDNet that the tool will get a fully functional web-based dashboard that will be very easy to use.
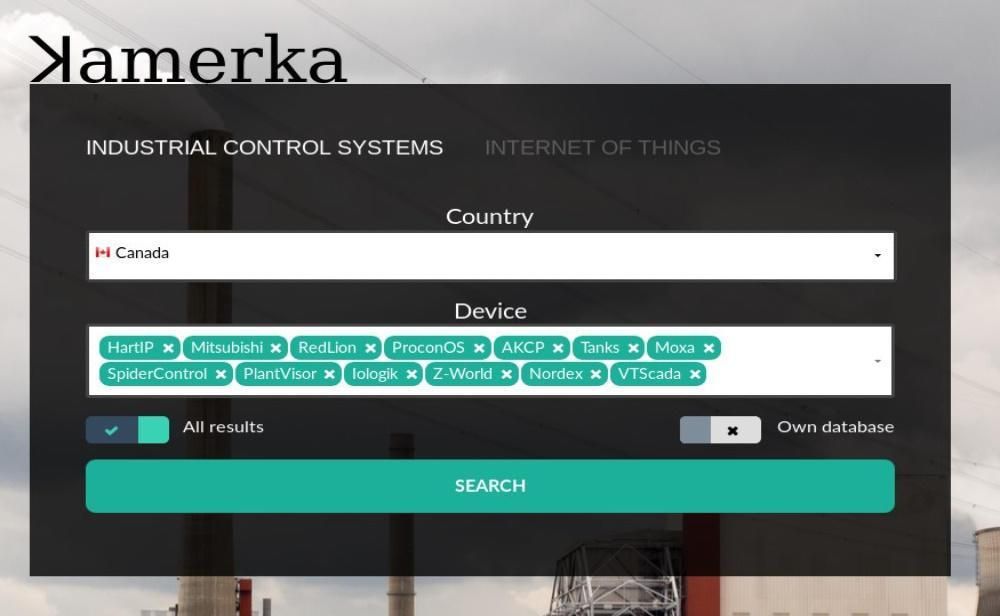
This new version will be particularly focused on improving the detection of industrial control systems, an area in which Wojciech has invested heavily over the past year.
Previous Kamerka versions can detect ICS/SCADA systems such as: Modbus, Siemens S7, Tridium, General Electric, BACnet, HART IP, Omron, Mitsubishi Electric, DNP3, EtherNet/IP, PCWorx, Red Lion, Codesys, IEC 60870–5 –104, and ProConOS.
The new version will also be able to detect Pl@ntVisor, Iologik, Moxa Devices, SpiderControl, IQ3, VTScada, Z-World, Nordex and various storage tanks .
"This will be a new intelligence platform that can collect information on exposed devices within a specific area based on coordinates that you specify or a scan of the entire country," Wojciech said.
If this sounds scary, that's because it is. Kamerka effectively enables users to see what a hacker would see when searching for or researching a target.
Companies can use the tool as network self-diagnostics, but apparently, it's also something hackers love and will likely abuse to plan future attacks.
Over the past few months, Wojciech has demonstrated the terrifying capabilities of Kamerka in two blog posts, using the tools to identify connected industrial equipment in Poland, Switzerland , and the United States .
Starting with a simple search query (such as Niagara Fox devices in the United States), Wojciech showed how attackers can use Kamerka to track down the devices they want to compromise.
Some locations displayed by Kamerka may be slightly different from the actual location, but the metadata provided by Kamerka can help an attacker pinpoint the target's true location with a few Google searches .
For example, an attacker could click on a device icon, obtain metadata information about the device, and then search for various keywords (such as factory names or street names) to find the target's true location, complete with Google Maps itinerary interpretation, or even Street View. image.
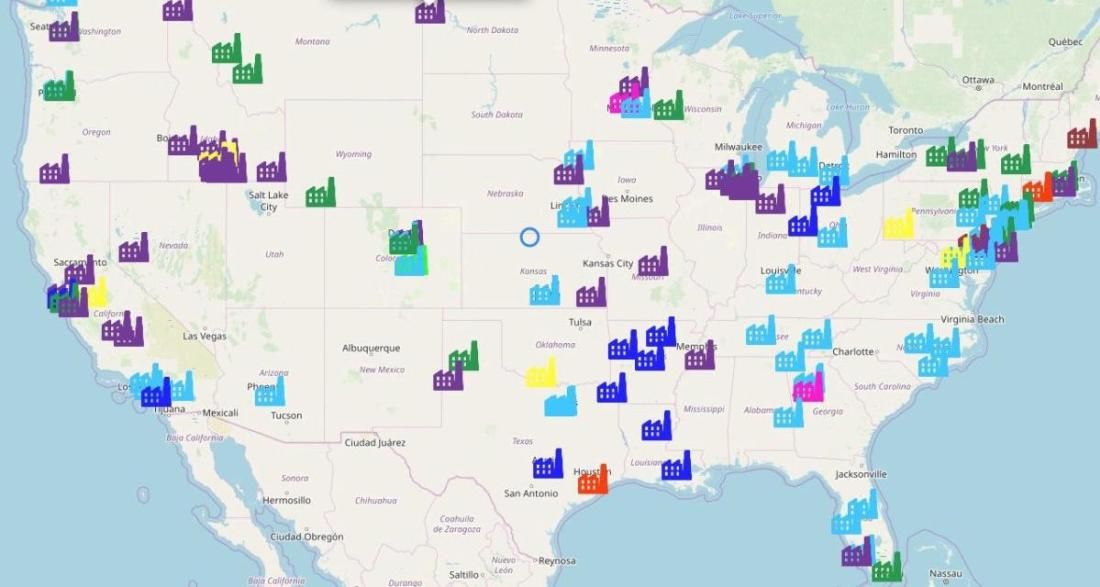
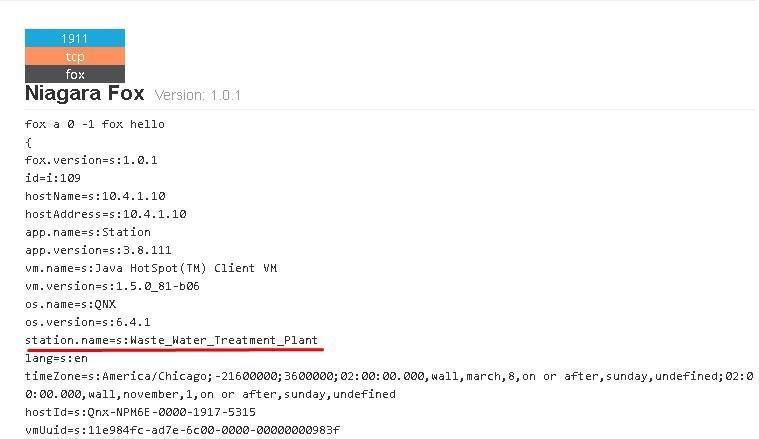
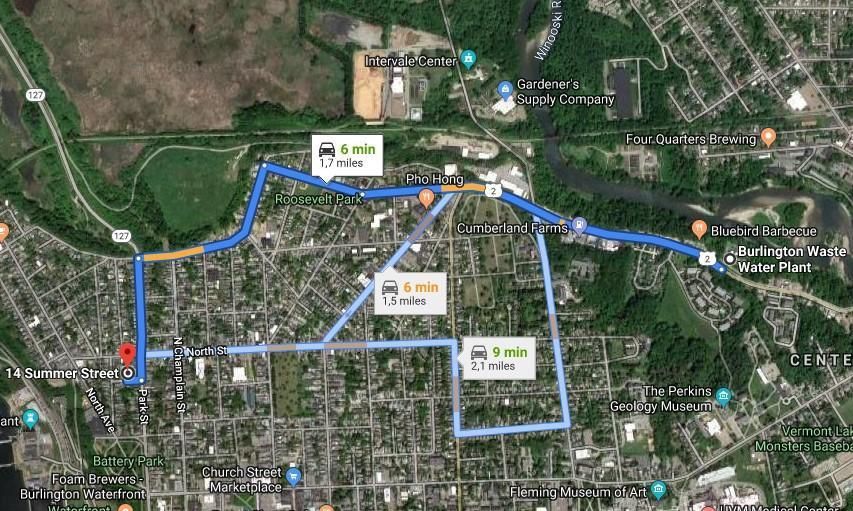
Kamerka is so effective because many system administrators often have to manage large numbers of devices. They often use the building name or full address to provide the most accurate description possible, rather than using numerical values to identify the device.
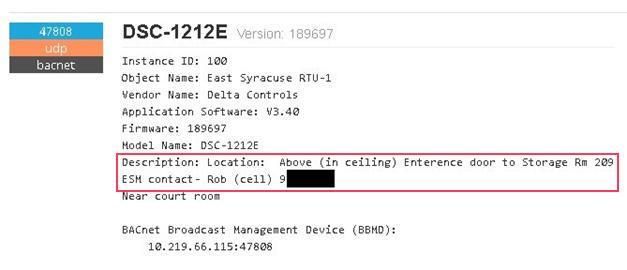
Such information was also previously available on Shodan or BinaryEdge, but only when searching for very specific IP addresses. With Kamerka, all this information is available directly on the map.
Over the past few years, factories, power plants, and other critical infrastructure entities have been increasingly exposed to online attack surfaces.
Attackers have compromised nuclear power plants, power grids, dams, hospitals, government agencies, and military targets, just to name a few.
In many cases in the past, an effective attack took days or weeks to plan. But with tools like Kamerka, planning an attack only takes a few minutes .
With a few searches, an attacker can find a target in a specific area, identify unpatched devices (Shodan has listed exposed ports and unpatched vulnerabilities), and launch an attack to take over the target device.
Such attack strategies are no longer theoretical.
Last August, Microsoft said it had seen Russian state-sponsored hackers using IoT devices such as printers and video monitors as entry points for attacks .
But nation-state hacking shouldn’t be organizations’ only concern.
Wojciech warned that ransomware groups may have begun targeting smart devices exposed on the internet in a similar way - using them as entry points into key targets .
With Kamerka, their job has certainly become much easier.
"I don't think it's going to be easy to take over an entire power plant, but small misconfigurations are obvious entry points, such as exposing the device to the internet, using default credentials or running other vulnerable software," Wojciech said.
Kamerka is already available on GitHub . You can even give it a try and see how scary it is (or, to be precise, how scary an unsecured IoT is). ⚪️
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More