How to protect yourself against Pegasus, the most powerful Israeli spyware spreading around the world
The assumption that only extremely high-level sensitivities encountered the most expensive and terrifying spyware was overturned this summer by a stunning data breach; investigation reveals Israel’s most terrifying surveillance technology companies NSO's Pegasus spy tool penetrated the iPhones of journalists, lawyers, human rights defenders, activists, and business executives around the world by exploiting weaknesses in Apple software, including a no-interaction zero-day vulnerability in iMessage.
This is one of the hottest news in June this year, although, it is not news - our original website has an " Israel and NSO " column, and you can see a separate section summarizing this part in List-4 . But few people think about how to deal with such horrific attacks, which is what this article hopes to try to explain.
While NSO has defended itself by claiming that the spyware is "only used to fight criminals," a list of potential targets leaked in June showed that journalists, activists and politicians were all targeted by NSO's clients.
Amnesty International described the detailed attacks as lasting from 2014 to July 2021. Some attacks are considered "zero-click/no-interaction", meaning that the victim does not need to interact in any specific way to be successfully attacked.
The spyware also used multiple zero-day vulnerabilities, including on iPhone 12 running iOS 14.6.
📌 Governments around the world are hoarding zero-day vulnerabilities, which may be the most powerful political weapon of this century. This matter is very important. If you missed This Is How They Told Me About the End of the World .
In fact, the attacks listed in the Amnesty International report began as early as May 2018 – the same time the IYP first began reporting on the series of disasters.
📌 In case you missed the 2018 reports: “ Israeli Spyware Firm Sells Surveillance Technology and Knowledge to Target Journalists, Dissidents and LGBT People in 130 Countries ” and “ Pegasus Spyware Produced by Israeli NSO Is Used for Surveillance in 45 Countries” and attacks on dissidents and activists—Asia has Hong Kong .”
The disclosure threatens to plunge hacking experts into a state of "security nihilism," as Matthew Green, a cryptographer at Johns Hopkins University, fears.
Security nihilism holds that digital attacks have become so sophisticated that nothing can be done to prevent them or lessen their impact. Such a conclusion would be a mistake.
📌 When we explained why IYP adopts open source intelligence, we mentioned the security nihilism in Chinese society , and this phenomenon still clearly exists today, see " This is Not a Athletic Show ".
At any time, knowing is always better than not knowing. We need to calm down and carefully think about possible countermeasures. Although to be honest, unless a transnationally united revolution overthrows this global political weapon , pure technological compensation cannot be a long-term solution .
First, nihilism plays into the hands of malicious hackers, who want nothing more than for their targets to stop trying to protect themselves. And, this is also factually wrong. It's still possible to defend against NSO's spyware — for example, by following operational security rules , such as not clicking on unknown links, practicing device partitioning (such as using different devices for different applications), and installing on mobile devices Encrypted VPN and more. These techniques are effective against any number of digital attacks.
- If you are a sensitive person, please see a detailed summary of security measures in our List-5 "Shield" ;
- If you are an ordinary digital device user, the content in the "Technical Self-Defense" section in List-1 should be suitable for you;
- If you are looking to get rid of threats, you can try the Becoming Untraceable series;
- If you have become a target and are preparing to escape from control, the " Perfect Stealth " series should be familiar to you;
- If you are an activist who is unwilling to endure, the " Total Security " series of tutorials is the most scientific security training for you and your close team members.
As a classic adage in the security field goes, there is no such thing as 100% perfect security, but that is no excuse for slacking off. Well, here are some practical steps you can take to reduce your "attack surface" and protect yourself from spyware like NSO.
In addition, recently, Citizen Lab also made an investigative report with technical analysis, you can refer to " From Pearl to Pegasus ".

Let's first look at its attack methods.
1. Network injection
The first type of attack is web injection, where users are mysteriously redirected from one legitimate website to another. Safari's browsing history logs showed suspicious URLs that were visited, evidence of redirects that occurred within barely a second of opening the web page.
The Favicon database also shows evidence of similar redirects, though not necessarily through active browsing. In one case, while previewing a link shared in a journalist's Twitter timeline, the Safari browser service used caused the web page to load and redirect to a suspicious URL, despite not opening a separate browser.
2.Bridgehead
Logs of process execution show that a process named "bh" is also associated with the Pegasus installation domain and typically appears after a successful network injection attempt.
"bh" is believed to be related to a 2016 vulnerability in the iOS JavaScriptCore binary that allowed code execution and persistence on the device across reboots. bh is thought to stand for "BridgeHead" and is the internal name of the component.
After "bh", the malware also uses other processes, including "roleaboutd" and "msgacntd", which are believed to be late-stage processes used after successful exploitation and privilege escalation. Other similar processes were also discovered, including "pcsd" and "fmId", which may serve the same purpose.
3. Photos
There is evidence that an Apple photo application process called "mobileslideshow" may have been used in the attack before the "bh" process was used.
It is suspected that the Photos application or Photostream service was used as part of an exploit chain that deployed the Pegasus spyware.
In every case where Photos is used, it seems that Photostream uses the same iCloud account address. Some interaction-free attacks apparently require specific iCloud accounts to work.
4. No interaction 0-day problem in iMessage
Since 2019, many vulnerabilities in iMessage and FaceTime have been discovered and patched, however, it seems that some can still be abused.
In one attack, the Pegasus spyware process was executed after suspicious iMessage account queries were discovered. Multiple Hungarian journalists were apparently targeted by the same operator, with similar addresses and processes used in each attack.
Attacks via iMessage are apparently back in 2021, this time involving a query to a suspicious iMessage account, followed by an HTTP request performed by a coretelephony process. This appears to be requesting a payload for a process named "gatekeeperd".
An attack in May 2021 showed a similar query being made to a mysterious iCloud account, with push notifications apparently being used as a way to apply the payload to the targeted iPhone before execution.
5. Apple Music
There is also evidence that Pegasus spyware may have been delivered through the Apple Music app in July 2020. During that infection, Apple Music's network traffic was recorded, and the music app's HTTP requests were again directed to the domain used to distribute Pegasus.
Amnesty International was unable to determine whether Apple Music itself was used for the initial infection, or if it was used for sandbox escape or privilege escalation.
6. Tools and Assistance
Following the investigation, Amnesty International released the Pegasus indicator via GitHub to assist other security researchers in discovering additional Pegasus infections. These indicators include domain names within the Pegasus infrastructure, email addresses recovered from iMessage account queries, and process names associated with the software.
A tool called the Mobile Verification Toolkit is also being released. As a modular tool, it is designed to simplify the process of acquiring and analyzing data from Android devices, as well as analyzing records from iOS backups and system dumps to find any further potential traces.

Pegasus provides "unrestricted access to target mobile devices"
The most recent disclosure involves a specific spyware product from NSO, known as Pegasus. This follows extensive research into the company's surveillance tools by Citizen Lab , Amnesty International , Article 19 , R3D and SocialTIC , among others. Here are some specific insights.
The spyware's capabilities were outlined in what appears to be NSO Group brochures from 2014 or earlier , and were provided when WikiLeaks published an email library linked to another spyware company , the Italian Hacking Team . The document aggressively promotes Pegasus, saying it provides "unlimited access to a target's mobile device" and allows customers to "remotely and covertly collect everything about your target's relationships, location, calls, plans and activities — no matter where they are. When and where”.
[Note: We have the "Israel and NSO" column, found in Listing-4 ; there is also the "Hacking Team" column in the same location. Also see an open-source intelligence analysis of the shocking data breach here (" Inside Hacking Team ")
The manual also states that Pegasus can:
- Real-time monitoring of voice and VoIP calls;
- Extract contacts, passwords, files, and encrypted content from your phone;
- Operates as an "ambient eavesdropper", listening through a microphone;
- Monitor communications via apps such as WhatsApp, Facebook, Skype, Blackberry Messenger and Viber;
- Track your phone’s location via GPS…
However, despite the hype, Pegasus is still just a glorified version of an older type of malware known as a remote access trojan, or RAT: a program that allows unauthorized parties complete access to a target device. In other words, while Pegasus may be powerful, in theory the security community should have a good idea of how to defend against this type of threat.
Let's take a look at the different ways Pegasus can infect a phone—its various "agent installation vectors," in the parlance of the manual—and how to defend against each one.
1. Avoid social engineering bait
Social engineering methods have always been the focus of security threats and are the first step for attackers to use to break through. Social engineering is also a mainstay of interrogation psychology to help people who are arrested and teased avoid being bludgeoned by the police. It's important from a security perspective , which is why IYP has a "Social Engineering" column that analyzes from various angles how you might be tricked. You can see a summary of the content of the individual sections in List-3 and List-5 .
Reports of the Pegasus attack include reports that journalists and human rights defenders received SMS and WhatsApp bait messages that lured them to click on malicious links. These links download spyware that enters the device through browser and operating system security holes. Remember how Washington Post columnist Jamal Khashoggi was quartered — yes, because one of his close teammates ordered a can of protein powder online. See the story " When Malware Disguises Online Shopping " here.
In leaked spyware manuals, this attack vector is called "Enhanced Social Engineer Message" (ESEM). It states, "The chance that a target will click on a link depends entirely on the credibility level of the content. Pegasus solutions provide a wide range of tools to craft a message that is *tailored* to appear completely innocuous to lure the target into clicking" .
As CPJ detailed , ESEM decoy information related to Pegasus falls into different categories. Some claim to be from established organizations such as banks, embassies, news organizations, or package delivery services. Others relate to personal matters, such as work or alleged evidence of a partner's cheating, or claims the target is facing some immediate safety risk.
Future ESEM attacks may use different types of decoy messages, which is why you must be cautious about any messages and letters that try to convince you to perform digital actions!
📌 Here are some examples of what this means in practice:
A. If you receive a message with a link, especially if it contains a sense of urgency (that a package is about to arrive, or that your credit card will be charged), you *must* avoid the urge to click on it immediately.
B. If you trust the linked website, please *manually enter* the linked URL instead of clicking directly.
C. If you want to go to a website that you visit frequently, the website should be saved in a local bookmark folder, and you should only access the website from links in your own folder.
D. If you decide to click on a link rather than typing it into your browser or accessing the site via a bookmark, at least double-check the link to make sure it points to a site you are familiar with. Keep in mind that you can still get scammed: some phishing links use similar-looking letters in non-English character sets, known as homographs . For example, the Cyrillic letter "О" might be used to imitate the Latin letter "O" commonly seen in English.
E. If the link appears to be a shortened URL, use a URL expander service, such as URL Expander or ExpandURL , to display what the actual long link it points to is before clicking.
F. Before you click on a link that is obviously sent to you by someone you know, please confirm that this person is indeed the person you know and that this person did send you the link; because your friend's account may be hacked, or their phone number was spoofed. Confirm this with your friend using a different communication channel than when you received the message. For example, if the link was sent via text message or email, give the sender a call. This is called *out-of-band authentication/out-of-frequency authentication or authentication*.
G. Implement device isolation and use a *auxiliary device* without any sensitive information to open untrusted links. Remember, if an assistive device is infected, it can still be used to spy on you via the microphone or camera! So keep it in a Faraday bag when not in use — or at least away from where you're having sensitive conversations (keeping it in a Faraday bag is definitely a good idea).
H. Use *non-default browser*. According to a section of the leaked Pegasus manual titled "Installation Failed," the installation may fail if the target is running a browser that does not support the spyware, specifically one other than the "device's default browser." However, please note! This document is from several years ago, and today Pegasus probably supports all kinds of browsers.
I. If you have any doubts about a link, the safest course of action is to avoid opening the link.
2. Defeat network injection attacks
In multiple cases, another way Pegasus infects devices is by intercepting the phone's network traffic, a so-called man-in-the-middle attack, or MITM, in which Pegasus intercepts unencrypted network traffic, such as HTTP network requests, and redirects it to Malicious payload.
To do this, the spyware would need to trick the phone into connecting to a rogue portable device that pretends to be a nearby cell tower — like a stingray; or, directly gain access to the target’s cell phone carrier (if the target is on a government-provided This is absolutely feasible in an oppressive regime with telecommunications services ). This attack works even if the phone is in mobile data-only mode and not connected to Wi-Fi.
[Note: In fact, this attack method is commonly used around the world, especially to arrest protesters in mass incidents. He was even tied to a plane and killed hundreds or thousands of people at once. In case you missed it , How to Deal with Massive Government Espionage on Citizens Using Stingrays . Don’t forget that IBM and Google have already helped China build an even more terrifying surveillance tool of the same kind . 】
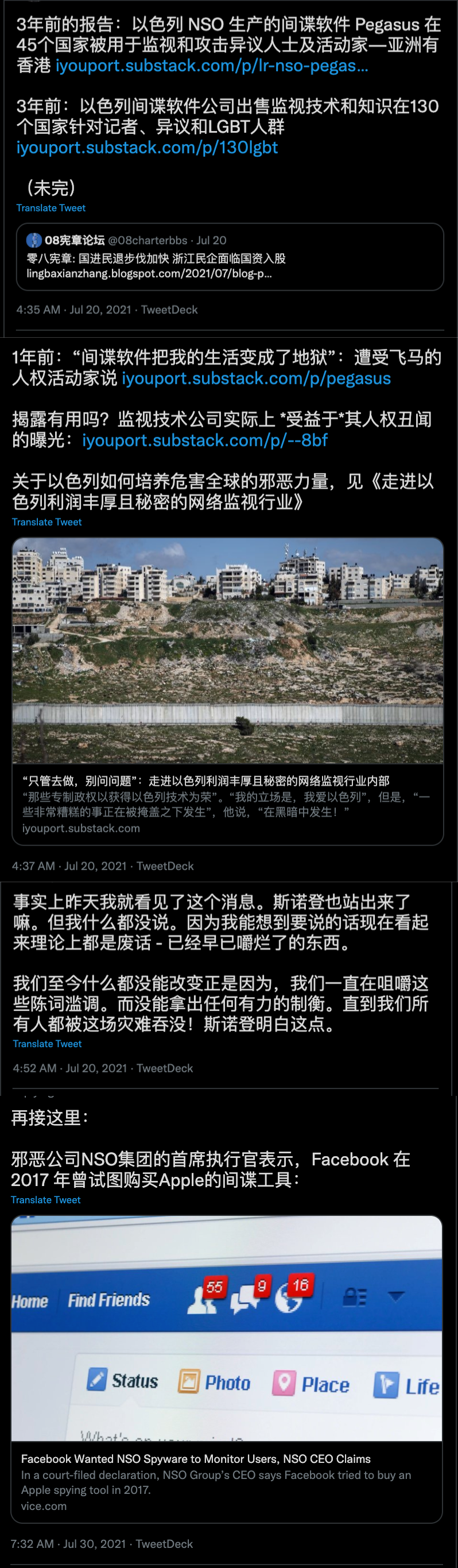
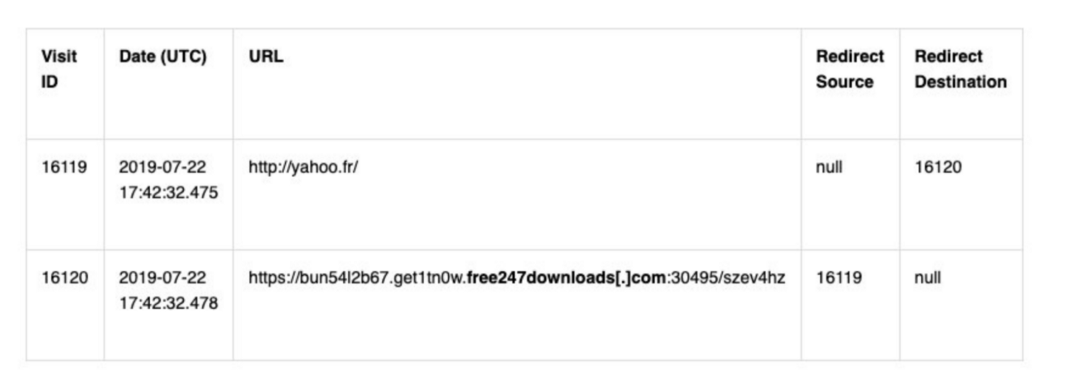
When Maati Monjib, co-founder of the NGO Freedom Now and the Moroccan Association for Investigative Journalism, opens the iPhone Safari browser and types in yahoo.fr, Safari first tries to go to http://yahoo.fr. Normally this will redirect to https://fr.yahoo.com, an encrypted connection. However, because Monjib's connection was intercepted, it instead redirected to a malicious third-party website and eventually compromised his phone.
If you only enter the website domain name (such as yahoo.fr) in the browser address bar without specifying the protocol (such as https://), this provides the possibility for a MITM attack because your browser will try to unencrypted by default. HTTP connection to the site! Normally, when you arrive at a real website, it immediately redirects you to a secure HTTPS connection; however, if someone tracks and hacks your device, the first HTTP connection can be enough of an entry point to hijack your connection. .
Some websites prevent this using a sophisticated security feature called HTTP Strict Transport Security , which prevents your browser from making unencrypted requests to them, however, this cannot always be counted on, even for The same goes for some sites that implement it correctly.
📌 Here are some things you can do to prevent these types of attacks:
A. When entering the website, be sure to type https://
B. Add the secure (HTTPS) URLs of your favorite websites to local bookmarks and use these URLs to access the website instead of entering the domain name directly.
C. Additionally, use an encrypted VPN on both your desktop and mobile devices. A VPN securely transmits all connections to a VPN server, which then accesses websites on your behalf and forwards them to you. This means that an attacker monitoring your network will most likely not be able to successfully conduct a MITM attack because your connection is encrypted to the VPN - even if you enter the domain name directly into the browser without the " https://" part .
However, if you use a VPN, always remember that your VPN provider has the ability to monitor your internet traffic, so it’s important to pick a trustworthy provider – see Here’s How a VPN Can Be Unreliable 5 signs if you don’t understand technology .
In addition, Wirecutter publishes regularly updated, comprehensive comparisons of VPN providers based on their history of third-party security audits, their privacy and terms of use policies, the security of the VPN technology used, and other factors. You can refer to it.
3. Zero-click vulnerability
Unlike infection attempts that require the target to perform some action, such as clicking a link or opening an attachment, zero-click vulnerabilities are called zero-click because they do not require any interaction from the target. All that is required is that the target has a specific vulnerable application or operating system installed. As previously noted, Amnesty International's forensic report on the recently disclosed Pegasus evidence noted that some infections were spread through zero-click attacks that exploited Apple Music and iMessage apps.
This is not the first time NSO Group’s tools have been linked to zero-click attacks. A 2017 complaint against former Panamanian President Ricardo Martinelli noted that journalists, politicians, trade unionists and civic association leaders had all been targeted by Pegasus spyware, and in 2019, WhatsApp and Facebook filed The complaint alleges that NSO Group developed malware capable of exploiting WhatsApp's zero-click vulnerability.
Since zero-click vulnerabilities/no-interaction vulnerabilities, as the name implies, do not require any user interaction, they are the most difficult to defend against. However, users can reduce their chances of being hit by these vulnerabilities by reducing the so-called "attack surface" and practicing device isolation .
Reducing your attack surface simply means minimizing the ways in which your devices can become infected. Device isolation means spreading your data and applications across multiple devices - Chinese users should easily understand this. We have heard many times that Chinese users isolate popular Chinese applications such as WeChat, Weibo, Alipay and so on to one device. On a standalone device, this is very nice.
📌 Specifically, users can do this:
A. Reduce the number of apps on your phone. The fewer unlocked doors in your home, the fewer opportunities a burglar has to gain entry; likewise, fewer apps means fewer virtual doors on your phone for adversaries to exploit. Your device should have the most basic apps you need to perform daily functions. There are some apps you can't delete, like iMessage; in those cases, you can usually disable them , although doing so will also make text messages no longer work on your iPhone.
B. Regularly check your installed applications ( and their permissions ) and delete any applications you no longer need. It's safer to delete a rarely used app and download it again when you really need it than to let it stay on your phone. Don't forget " less is more " .
If you missed Do You Really Understand What App Permissions Grant? Here’s what you need to know to keep you safe 》
C. Update the mobile operating system and individual applications in a timely manner, because updates can fill loopholes, sometimes even unintentional loopholes .
D. Sort your remaining applications into categories. If a phone only has WhatsApp installed and is compromised, the hacker will get the WhatsApp data, but not other sensitive information such as emails, calendars, photos or Signal encrypted information.
E. Please remember that even isolated mobile phones can still be used as eavesdropping and tracking devices, so keep the devices physically separated - that is, put them in a separate room, preferably Place in Faraday bag. If you've ever been to a confidential meeting or entered a secure facility, you know this, cell phones are not allowed in the room.
4. Physical access
The last way an attacker can infect a phone is through physical interaction with the target phone - a malicious maid . According to the manual, "When physical access to the device is an option, Pegasus agents can be manually injected and installed in five minutes" — though it's unclear whether the phone needs to be unlocked or whether an attacker would be able to infect even a password-protected phone. .
There appear to be no known cases of physically initiated Pegasus attacks, although such vulnerabilities may be difficult to detect and distinguish from online attacks.
📌 Here are some ways you can mitigate their effects:
A. Always keep your device within your sight. Any time your device is out of sight, physical damage can occur. We have emphasized this issue many times in the " Social Engineering " series and the " Hacktivism Power " series - whether it is to take a shower or use the toilet, as long as there is another person in the room, or anyone may enter this room, it's best to take all your electronic devices with you.
Obviously there's a difference between customs agents being able to take your phone at the airport and leaving your laptop in your bedroom while you go to the bathroom, but some of the same risks are involved and you're going to have to calibrate your risk tolerance.
B. Keep your device in a Faraday bag when it has to be left unattended, especially in riskier places like hotel rooms. This doesn't prevent the device from being manipulated, but it does at least serve as a reminder that the device has been taken out of the bag, may have been tampered with, and should no longer be used.
C. Use disposable phones and other barrier devices when entering potentially hostile environments, such as government buildings, including embassies and consulates, or passing through border checkpoints.
📌 Generally speaking:
A. If you suspect that your phone is infected with Pegasus, please use Amnesty International’s mobile verification toolkit .
B. Back up important files regularly.
C. There’s no harm in resetting your phone regularly.
Although Pegasus is an extremely dangerous and sophisticated piece of spyware, there are concrete steps you can take to minimize the chance of your device being infected. There's no foolproof way to completely eliminate risk, but there are certainly things you can do to reduce it, and security nihilism is a no-no.
About the Mobile Verification Toolkit launched by Amnesty International
Amnesty International has released a tool that can help you detect if your phone is affected.
Alongside the kit is a great set of instructions that should help you through some of the technical inspection process. Using the tool involves backing up your phone to a separate computer and running a check on that backup. Let’s make some introductions.
The first thing to note is that this tool is command line or terminal based, so it will require some technical ability or a bit of patience to run. But it’s really not difficult! Don't worry, just follow the instructions. What follows will attempt to cover a lot of what you need to know.
The second note is that the analysis Amnesty International is running seems to work best on iOS devices. Amnesty International said in its filing that the analysis its tool can run on Android phone backups is limited, but that the tool can still check for potentially malicious text messages and APKs . Again, it is recommended to follow its instructions .
To check your iPhone, the easiest way is to make an encrypted backup using iTunes or Finder on your Mac or PC. You'll then need to find the location of that backup, and Apple provides instructions for that . Linux users can create backups using the libimobiledevice command-line tool by following Amnesty International's instructions .
After obtaining a backup of your mobile phone, you need to download and install Amnesty International's mvt program. Amnesty International also provides relevant instructions .
If you are using a Mac to run the check, you will first need to install Xcode (which can be downloaded from the App Store) and Python3 before you can install and run mvt. The easiest way to get Python3 is to use a program called Homebrew , which can be installed and run from the terminal. Once these are installed, you can run Amnesty International's iOS instructions .
If you're having trouble trying to decrypt your backup, that's okay. The tool also gave an error when I tried to point it to my backup, which was in the default folder. To fix this, I copied the backup folder from the default location to a folder on my desktop and pointed mvt to it. The command ends up looking like this:
mvt-ios decrypt-backup -p PASSWORD -d decrypt ~/Desktop/bkp/orig
[Note: Please note that this is for illustrative purposes only. Please use the commands given by Amnesty International as the program may have been updated ]
When running the actual scan, you point to a "Compromise" file, which Amnesty International provides as a file called pegasus.stix2. Those new to using Terminal may be confused by how to actually point to a file, but it's relatively simple as long as you know where the file is. For beginners, it is recommended to download the stix2 file to your Mac's Downloads folder. Then, when you get to the step of actually running the check-backtrace command, add:
-i ~/Downloads/pegasus.stix2
Go to the options section. For reference, the command here ends up looking like this. (Again, this is just to illustrate the problem. If you just copy these commands and run them it will result in an error ):
mvt-ios check-backup -o logs — iocs ~/Downloads/pegasus.stix2 ~/Desktop/bkp/decrypt
(For reference, ~/ more or less acts as a shortcut to your user folder, so you don't have to add anything to a place like /Users/mitchell)
Once again, it is recommended that you follow Amnesty International's instructions and use its commands, as there is always a chance that the tool will be updated. Security researcher @RayRedacted also posted a good thread on Twitter about some issues you might encounter when running the tool and how to deal with them.
Finally, Amnesty International only provides instructions for installing the detection kit on MacOS and Linux systems. For those looking to run it on Windows, The Verge has confirmed that the tool can be used by installing and using Windows Subsystem for Linux (WSL) and following Amnesty International’s Linux instructions. Using WSL will require downloading and installing a Linux distribution such as Ubuntu , which will take some time. However, it can be done while you wait for your phone to back up.
After running mvt, you will see a warning list of suspicious files or behavior. It's worth noting that a warning does not necessarily mean you are infected. For me, some perfectly normal redirects appear in the part where it checks my Safari history (sheet.google.com redirects to docs.google.com, reut.rs redirects to reuters.com, etc.). Again, I get some errors, but only because the program is checking for apps that are not installed on my phone.
The story surrounding Pegasus may make many people a little more skeptical than usual about phones, whether or not you're potentially being targeted by a nation-state.
As you've seen, it's possible that the government doesn't need to hack into your phone's microphone and camera to gain access to your private information— even if your phone isn't infected with Pegasus, the pervasive data intermediary industry most likely already is. Your location history is for sale. Here's a concrete note, you really need to read " Behind the One-Way Mirror: What the Alliance of Surveillance Capitalists and Government Has Been Doing to You?" 》 . ⚪️
HOW TO DEFEND YOURSELF AGAINST THE POWERFUL NEW NSO SPYWARE ATTACKS DISCOVERED AROUND THE WORLD
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More