Get rid of trackers: your actions must be anonymous, otherwise there is no sustainability
- Here are some basics. It's the nature of the internet to be easily tracked and monitored, and if you want to do anything serious with it, you have to be able to achieve a sufficient level of anonymity

Unlike real-life investigations, open source intelligence investigations must be anonymous and leave as little digital footprints and breadcrumbs as possible, otherwise the target will track you back in the future, not only blocking your investigation, but even damaging your basic information. Personal safety is threatened.
Mastering the security protection skills to avoid tracking is the most basic step to become a citizen investigator .
I have introduced a lot of security protection knowledge before, but this article will introduce the basic knowledge - about the various online technologies that can be used to track you, and propose targeted protection countermeasures that should be taken when conducting open source intelligence collection operations.
Please note: All security knowledge is not just for investigators. It is for everyone, any citizen who respects his or her human rights interests and does not wish to be preyed upon.
There are many different actors interested in tracking Internet users, each with their own motivations.
At its most basic, for example, it's driven in part by advertisers increasingly monitoring people's online behavior to tailor ads to target them. This type of tracking is known as online behavioral advertising (OBA). The explosive growth of social networking sites , all of which are trying to track your every move - "Sign up for free, come and play~"
Most popular today are so-called web analytics services (such as Cambridge Analytica) tracking online users to collect information that can be used to manipulate people ; and government spy agencies tracking online users at scale to analyze the world's digital information and predict future Political, military and economic changes.
- See the investigative report " Secrets of Psychological Manipulation: "Behavioral Economics" + PR=?" here 》
- This report is extremely important! " How do they catch people telling the truth?" ⚠️Disasters and lessons 》
Most commonly, cyber police, police and intelligence agencies use public information available online to obtain intelligence about their targets. And, social engineers and hackers implement tracking and monitoring in order to develop the most targeted attack plan.
Information obtained from public sources is called open source intelligence (OSINT) , which refers to all publicly available information. OSINT sources differ from other forms of intelligence in that they must be obtained legally without violating any copyright or privacy laws.
- See the intelligence breakdown and breakdown here " Google Maps is a better spy than James Bond "
⚠️What if, as an investigator, your target finds out that you are searching for him/them? What if they could learn where you, the searcher, are coming from, the organization behind it, and the location or identity of the searcher? What will they do to you?
You have to be wary of this. Because hiding your identity on the Internet is not as simple as wearing sunglasses and a wig in real life.
⚠️If the identity of the searcher is exposed during an open source intelligence search, it may bring serious dangers and even legal consequences in many cases.
The same question applies to business. Consider a company seeking to enter a new market. What would happen if other competitors working in the same field discovered the company's search practices?
Protecting operational privacy security is key to successful OSINT investigations.
This article is divided into two parts. It first explores the concept of "online tracking" and introduces different technical methods used to track people online to propose corresponding countermeasures.
Many junior OSINT practitioners believe that using a VPN service is enough to hide their online tracking – this is simply wrong .
Using a reliable VPN only hides your IP address, leaving the rest of your digital footprint visible to any trackers following you.
Complete online anonymity is very difficult to achieve. To become completely anonymous online, you need to use a set of tools and strategies to hide any traces that could reveal your identity or even the type of hardware and connection you use to access the internet, and it takes some serious technical skills.
Such anonymity is required only for cases of that level related to foreign espionage, usually conducted by intelligence agencies that know very well how to conceal their collection activities. rather than citizen investigators.
However, for the purposes of regular OSINT gathering activities, you need to anonymize to an appropriate level so that the target cannot detect that you are trying to find information about them.
The second part of this article will look at various online tracking technologies, how to counter them using a number of tools and strategies, and will propose a solution that allows anyone online to use a virtual device to link their browsing activity to local networks and infrastructure Isolate .

What is online tracking?
Online tracking can be defined as the process of tracking an Internet user's Internet browsing history and sometimes online behavior across different websites.
In order to link the browsing history to the target user, an identifier is used to distinguish each online user as an individual who can be tracked.
This identifier is similar to a person’s fingerprint in that it distinguishes a specific user device among millions of connected users.
The next section demonstrates how online tracking technically works.
Online tracking technology
Online tracking typically utilizes one or more of the following methods:
1. IP address tracking
Networking is impossible without an IP, an IP address is a unique identifier used to identify any network-capable device when connected to the Internet.
No two devices can have the same IP address on the same IP network, making IP addresses the first choice for tracking users online.
When connecting to the Internet, you either use the same IP address each time (a static IP) or a different number each time (called a dynamic IP).
A static IP address is an address assigned by your Internet Service Provider (ISP) that does not change over time; instead, your ISP assigns a dynamic IP address every time you connect to the Internet.
Every time you reboot your computing device or router, it assigns you a new IP address using something called Dynamic Host Configuration Protocol (DHCP). Some ISPs may assign the same IP address that was previously assigned to you multiple times, but this is not a rule of thumb.
Please note that it is possible to spoof (hide) an IP address when going online using different technologies such as VPNs and anonymity networks like the TOR network. Users can also use a NAT router, which enables all devices belonging to the same network to share a public IP address.
- About Tor " When shooting someone in the foot meets "sports death" - who will Onion make cry?" (1) 》
- " Those who pursue justice should strengthen their anti-investigation skills - Who will the onion make cry (2) "
- " Is it really safe? " So how do they arrest people? —— Who will Onion make cry (3) 》
- " Please close the door behind you, unless you want to hand the knife to the enemy - Who will the onion make cry (4) "
- " How to use the Tor network in your web browser?" 》
- " Don't Do These Nine Things When Using Tor to Protect Yourself!" 》
For these reasons, we cannot consider just one IP address sufficient to target an individual online user on the Internet today. However, it is still the top choice for tracking target people online.
To learn how to choose a VPN provider, you can see the " Security Manual "; to learn how to judge the security of a VPN, you can see here " How to verify whether your VPN connection is secure ?" 》.
2. Cookie tracking
Cookies are the most common technology used to track users online and are now a household name.
Cookies are small text files created when a user visits a specific website. They contain standard information including a unique ID that distinguishes the client device, an expiration date, and the name of the cookie website.
The cookie is used to determine the client device when returning to the same website again. Websites use cookies for two main purposes: to store login credentials and to track users' online behavior.
When most people talk about a Web cookie, they mean a basic cookie file (also called an HTTP cookie). An HTTP cookie is a simple text file used to track user visits to the website where it is deployed.
Expired HTTP cookies are automatically deleted when you close the browser. However, the expiration date may be many years in the future. In terms of cookie lifetime, there are two main types: session cookies and persistent cookies.
Session cookies are stored in temporary memory and are erased when the user closes the browser. Such cookies have no expiration date and do not store any information about the user's client device. It is commonly used to maintain shopping cart content in e-commerce websites.
Persistent cookies (such as Flash and evercookie cookies) raise serious privacy concerns.
Half of the cookie's content is first-party, belonging to the website you visit, and the other half is third-party, belonging to partners, services or advertisers that work with the website.
Third-party cookies are used to track activity (across multiple websites) and identify frequent and returning visitors in order to tailor content or optimize advertising or improve user experience based on cookie history. The two main types of persistent cookies are Flash and Evercookies.
Flash Cookies have higher persistence than traditional cookie files that have an expiration date and are stored in a specific folder on the client's hard drive. Merely deleting your web browser's cookie folder will not delete this type of cookie.
Flash cookies are used to store a user's browsing history on multiple websites and can be used to re-instantiate HTTP cookies deleted by the user.
To access all Flash cookies stored on your computer (under Windows), go to Control Panel ➤ Flash Player and select the "Prevent all sites from storing information on this computer" option (see image below).
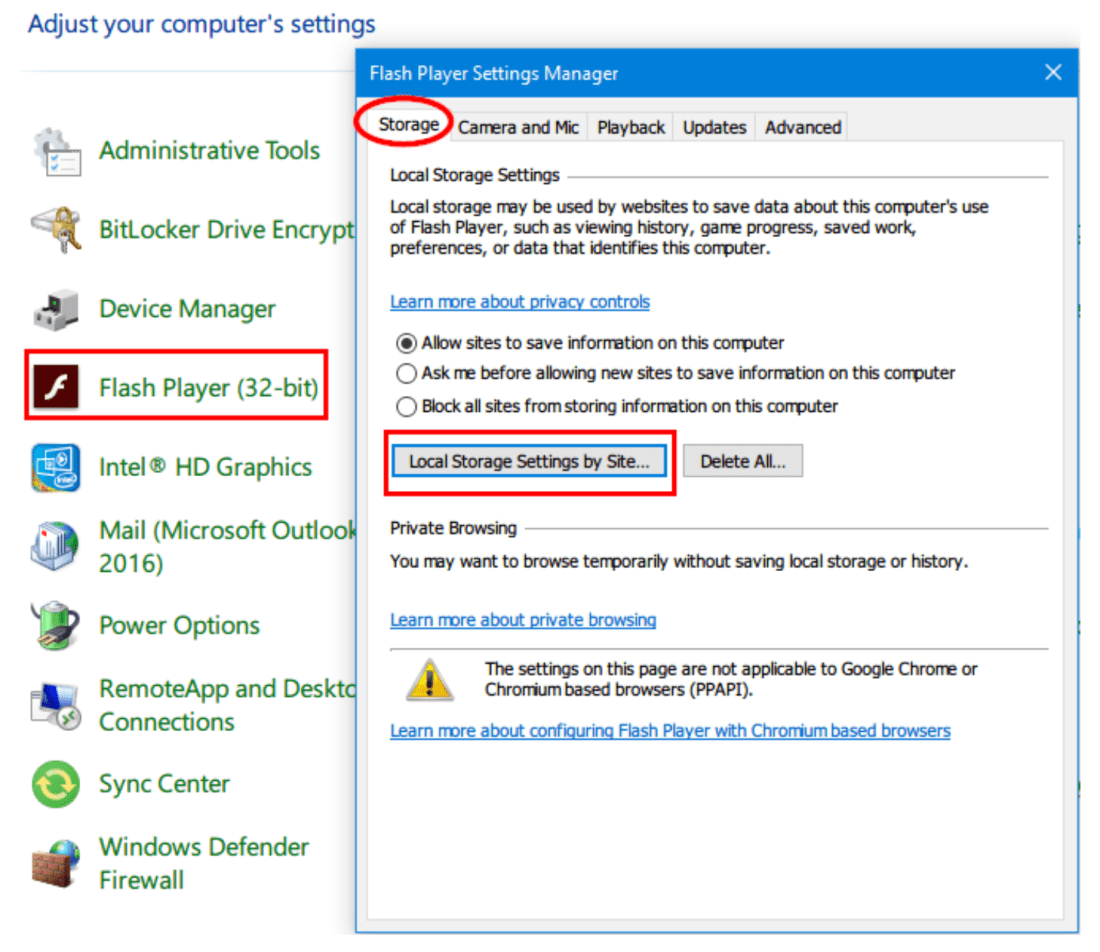
A tool can also be used to display the list of Flash cookies present in the system and delete them, FlashCookiesView is a portable tool created for this purpose .
Evercookies Cookies: According to developer Samy Kamkar, evercookies are JavaScript-based cookies that can persist even after users delete HTTP and Flash cookies from their computers.
It achieves its persistence by storing data in multiple locations on the client browser/computer (e.g., HTTP cookies, Flash cookies, HTML5 local storage, web history, Silverlight).
For example, if one of these locations is deleted by the user, evercookie will detect the location and regenerate it itself. Fortunately, modern web browsers are able to block or detect evercookies.
3. ETag tracking
ETags are another way to track users without using cookies (HTTP and Flash), JavaScript, HTML storage, or IP addresses.
ETags, or entity tags, are part of the Hypertext Transfer Protocol (HTTP) mechanism that provides web cache verification and is used to control how long specific files are cached on the client side.
ETags help web browsers avoid loading the same web resource twice, for example when a user visits a website that plays music in the background, changing it based on the user's local time.
If the ETag is different, the client browser will download a new version of the audio file.
ETags can be leveraged to track users in a manner similar to persistent cookies , and the tracking server can continuously send ETags to the client browser even if the content on the server does not change. This way, the tracking server can maintain an indefinitely persistent session with the client computer.
To get rid of ETags, you must clear your browser cache.
4. Digital fingerprint tracking
A browser fingerprint is a set of technical information about a user's system and browser that can differentiate their machine online.
This information includes the following: browser type, operating system (OS) version, installed add-ons, user agent, installed fonts, language settings, time zone, screen size and color depth, etc.
Fingerprinting allows trackers to distinguish a user's machine even if cookies and JavaScript are disabled .
Browser fingerprinting is stateless and transparent to both the user and the computer.
The information gathered from digital fingerprints may seem general and insufficient to identify a single computer online among millions of connected devices; however, when combined, the information can paint a comprehensive and unique picture about each user's computer. , thereafter, if combined with other personally identifiable information (PII), the information can be traced to the real identity .
This should effectively allow different external parties to easily profile targeted individuals without the use of traditional tracking technologies such as computer IP addresses and cookies.
- For more information, see Opsec Operational Security: What pitfalls should you be aware of during counter-reconnaissance? 》
It was concluded that most internet users can be profiled and tracked online using only a small amount of technical information in their browser.
There are two main types of device fingerprinting: script-based and canvas-based.
Script-based fingerprinting -
Script fingerprinting works by loading a script (usually JavaScript) into the user's browser. Once the script is successfully loaded, it executes to extract a wealth of technical information about the current browser and system configuration.
The extracted information includes user agent, installed add-ons/extensions, installed fonts, screen resolution, time zone, operating system type and version, CPU and GPU type, and many other details about the target system.
It is then hashed based on the information collected by the script. This hash can identify and track your device, just like an IP address.
The tracker uses Flash, Silverlight, or Java applets instead of JavaScript to perform fingerprinting. They will all return the same result.
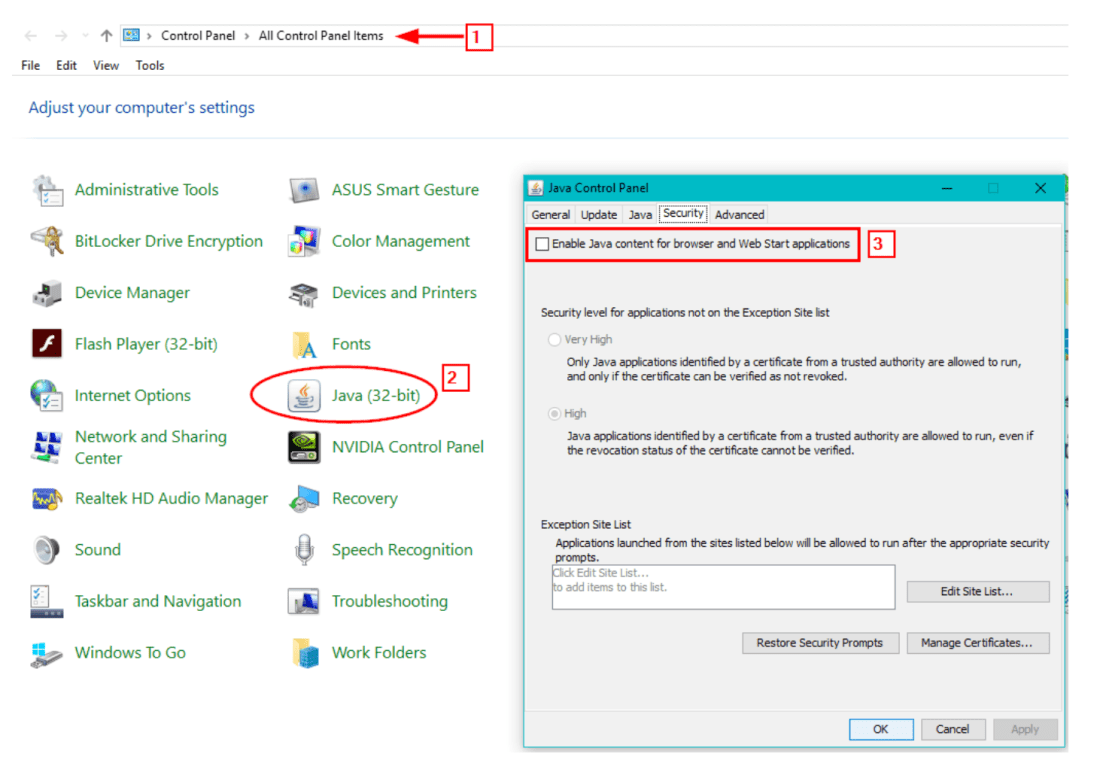
The main way to counteract this technology is to disable JavaScript in your browser. However, this approach is impractical and can lead to breaking a large number of websites (most web design frameworks are now based on JavaScript to provide functionality).
Disabling Java (see image below) does not cause problems such as disabling JavaScript.
Canvas fingerprint——
Canvas is an HTML5 element originally developed by Apple; it is used to draw graphics (lines, shapes, text, images) and animations (such as games and banner ads) on web pages using the JavaScript API. Advertisers can use canvas functionality to identify and track users.
Canvas fingerprint tracking is a new way to track users’ online activities. Just draw the invisible image on the user's client browser.
This image is different for each user and once drawn on the client's browser, it collects different technical information about the user's browser and computer. It is then hashed based on the information that has been collected.
This hash will be consistent across all sites the user visits (the hash is generated from the canvas data); this will effectively record the user's browsing history .
Although the information gathered from a canvas fingerprint cannot be used alone to identify a user, this fingerprint can be used in conjunction with other sources to completely identify you .
Countermeasures for Browser Fingerprint Tracking
Currently, fingerprinting is considered the biggest risk users face when surfing online.
To understand how we can stop this intrusion to protect our privacy, let's first take a look at what your current digital fingerprint is telling trackers. Below are popular websites that offer such services for free.
- Panopticlick ( https://panopticlick.eff.org )
- DeviceInfo ( https://www.deviceinfo.me )
- Browserleaks ( https://browserleaks.com )
- AmIUnique ( https://amiunique.org )
Configure your web browser for improved security
Major web browsers can be configured to be more privacy-friendly (e.g., automatically deleting browsing history and cookies) and have comprehensive privacy configurations to achieve this goal.
Users can also use private browsing mode to automatically delete browsing history, saved passwords and cookies.
In Firefox it's called "Private Browsing" and can be accessed by pressing the following button combination (Ctrl + Shift + A), while in Chrome it's called "Incognito Mode".
See more explanation here Opsec Operational Security: What pitfalls should you be aware of during counter-reconnaissance? 》.
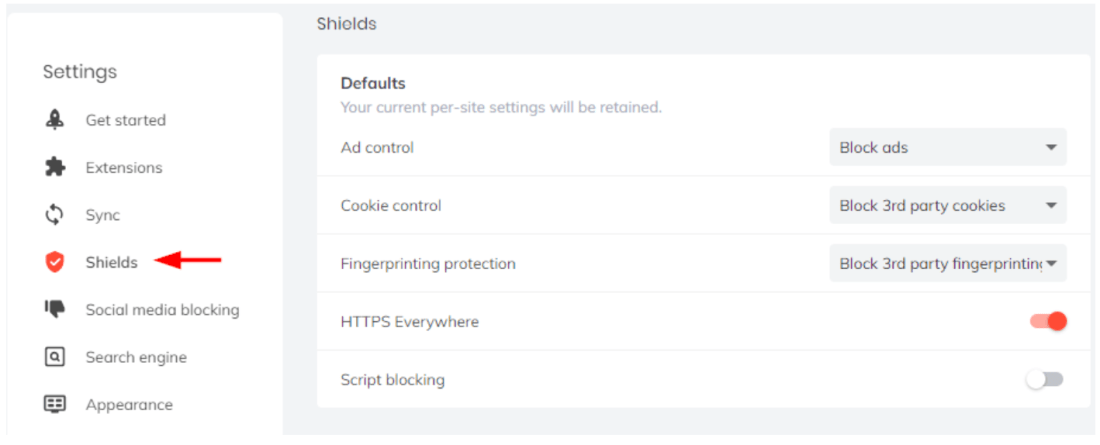
Brave browser is a privacy-focused web browser based on the Chromium project that accepts Chrome extensions.
Brave blocks other online tracking mechanisms by default, and you can enable fingerprint protection by going to Settings and clicking Shields (see image below).
Browser extensions protect privacy
There are many privacy add-ons available to block or mislead online trackers, the following are the most well-known ones:
- Privacy Badger — block invisible trackers ( https://www.eff.org/privacybadger )
- Disconnect — Block invisible websites ( https://addons.mozilla.org/en-US/firefox/addon/disconnect )
- uBlock Origin — another efficient blocker ( https://addons.mozilla.org/en-US/firefox/addon/ublock-origin )
- HTTPS Everywhere — encrypts your communications with many major websites, making your browsing more secure ( https://www.eff.org/HTTPS-EVERYWHERE )
- CanvasBlocker — Alters some JS APIs to prevent fingerprinting ( https://addons.mozilla.org/en-US/firefox/addon/canvasblocker )
- Cookie AutoDelete — Automatically delete cookies upon tab closes ( https://addons.mozilla.org/en-US/firefox/addon/cookie-autodelete )
- Decentraleyes — Block Content Delivery Networks ( https://decentraleyes.org )
- uMatrix — A point-and-click matrix-based firewall, with many privacy-enhancing tools ( https://addons.mozilla.org/en-US/firefox/addon/umatrix )
- User-Agent Switcher — switch between popular user-agent strings ( https://addons.mozilla.org/en-US/firefox/addon/user-agent-switcher-revived )
search engine tracking
Typical search engines track their users' searches to target tailored ads and customize the search results returned.
For example, most Google search engine users have a Gmail account (Google's free email service), and when a user performs an online search, the user's online activities are recorded and linked to his/her Gmail account (usually the user true identity).
Even if the user is not logged into a Gmail account, Google can still use any of the previous tracking technologies mentioned to link the user's browsing history to their real identity.
When searching for OSINT sources, it is recommended to use a privacy-oriented search engine that does not log your search history and does not return results based on criteria determined by the search provider.
There are many anonymous search engines that fail to track their users' activities, which you can find here: If You're Good at Search, You Can Find Everything: A Powerful Search World *Without Google* .
social network tracking
Social networking sites like Facebook and Twitter can track users across sites (they can actually track the browsing history of most Internet users), even if those users are not currently logged into Facebook or Twitter!
You must have noticed that most websites have Facebook "Like" and "Share" buttons that help share content on the user's Facebook news feed. However, you should know that whenever you visit a web page that has a Facebook Like or Share button, Facebook will log the visit even if you don't click the button!
Facebook tracking doesn't stop at this point, as they can track **non-Facebook** users across different websites without their knowledge using hidden code embedded in the Like and Share buttons. Been doing this!
Twitter's "Follow" button also plays the same role in tracking users online as Facebook's "Like" and "Share" buttons.
- See more detailed introductions in the column: " About Facebook: It's more than just a company "
- " About Apple, Microsoft and Twitter "

Escape online tracking
As we've highlighted throughout our security knowledge, different techniques can be used to track users online, and combating these techniques requires different tools and strategies to be implemented correctly.
To prevent online tracking, users need to take three basic steps :
- Hide your IP address with a reliable VPN service.
- After closing the browser, delete (or reject) cookies and web browser cache.
- Prevent digital fingerprinting techniques from profiling computers.
This requires serious technical skills and a clear sense of defense. Combating tracking and fingerprinting is difficult, and there are no 100% guaranteed technical solutions to this problem.
Be aware that even after configuring your web browser for better privacy and installing many add-ons, a skilled adversary can still identify your digital fingerprint to a great extent.
The best technical solution to combat browser fingerprinting is to make your browser look like the fingerprints of most browsers.
For this purpose, it is recommended to use a newly installed copy web browser that is manually configured with enhanced privacy settings without installing any add-ons. The browser should be run from a virtual machine (such as Virtual Box) that is also freshly installed.
- Review the virtual machine configuration tutorial for open source investigation here " Building your custom OSINT machine (Part 1) " " Part 2 ", " Part 3 ", " Part 4 ", " Part 5 "
By using this technology, your browser will look like the majority of running browsers, effectively hiding your true digital footprint.
Of course, you still need to use a VPN to encrypt your connection and hide your real IP address.
The anonymous tool Whonix is especially recommended, and you can see the installation and usage tutorial here . ⚪️
The new list of IYP is as follows——
Self-defense: https://start.me/p/xbYXdR/iyp-1
Cognitive: https://start.me/p/RMQrDD/iyp-2
Fighting wits: https://start.me/p/nRBzO9/iyp-3
Visionary: https://start.me/p/aL8RrM/iyp-4
You know: https://start.me/p/1kod2L/iyp-direct-action5
Continuously updating!

Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More