Is it possible to reveal your identity from Telegram? —— A Chinese friend raised this question
Recently, a Chinese friend raised such a question: Is it possible to reveal the identity information of Telegram users? How difficult is it? The answer is, it's possible, and it's not difficult, and doesn't require a clever intrusion; so, that means in theory anyone could do it -- assuming the target isn't prepared enough .
The approach is, the "proactive" approach to open source intelligence.
This means an opportunity for direct contact with the identified target.
The easiest way to identify Telegram users in direct contact is the Contact Exchange feature. If the identified user accepts the stalker's contact details and adds them to the device's phonebook, the target's real phone number is automatically provided to the stalker.
Prevention ❗️: Do not use your real mobile phone number to register IMs like Telegram; do not accept friend invitations casually, even if the other party’s nickname is displayed as someone you are familiar with, you should contact this person in other ways in advance to confirm Telegram Check if the person with the same name is actually someone you know .
In the process of direct contact, intelligence investigation can also be conducted in a variety of other ways, allowing the tracker to obtain information about the connection and device (ip address, provider, region of location, computer model, version of the operating system, browser, etc. wait).
Records (logs) of user behavior have long been used in OSINT investigations. Logging an Internet user involves a direct interaction with the target, during which the target user will (in some form) access an external web resource, and the tracker has access to logs of that resource. It can be a specially created hyperlink or file that, when opened, launches a program that collects user data. There are a large number of services in the public domain that provide similar functionality.
The most easily adopted methods are as follows.
1. Use hyperlinks to get Telegram user data
Use the recorder to create a hyperlink to an external web resource, enticing the target user to click it, which will save the history of the visit. Similar loggers are: http://canarytokens.org/, https://grabify.link/ , https://iplogger.ru/ , http://ru.itsip.info/spy , https://iknowwhatyoudownload .com/ru/link/ . All clicks on created links, including logged results, are automatically saved in the selected logger tab.
To make it look less suspicious, trackers will often use link shortening services to cover it up. These services include: https://clck.ru/ , http://bit.do/ , https://bitly.com/ , https://www.lnnkin.com/ and many others.
There are other methods of masking.
Precautions ❗️ : Don't click on any shortened links, no matter what they are. IYP will never use shorteners. And, before you click on any hyperlink, hover over it and/or Copy Link to see what it actually is .
2. Use files to get Telegram user data
Using this type of logger involves logging when the target opens the file. Such loggers include: http://canarytokens.org/ (which allows you to generate various types of log files), as well as https://www.locklizard.com/track-pdf-monitoring/ and http://www. mailtracking.com/mailtracking/pmdoctrack.asp (generates PDF files only).
Precautions ❗️ : It is recommended to only open files from people you trust; once again, please make sure that the person is someone you know first - through other contact methods to confirm.
3. Use external network resources to obtain Telegram user data
Using a high-ranking domain that is considered legitimate to create content for tracking purposes is probably most efficient. This can be any website. In particular, use blogging sites such as https://telegra.ph/ , https://medium.com/ or https://teletype.in/ , create news on them, introducing recorders in the form of tracking pixels. There is little doubt about such links.
There can also be a more sinister method that allows you to quickly find the IP address, time zone, and browser settings of the person you are looking for. That is, use a file hosting service (such as http://anonymousfiles.io , http://anonfiles.com , http://filedropper.com , http://privatlab.com ), upload a file for the target user to download, Any file will do. After downloading, the tracker wrote to the service support department, saying that the file violated copyright due to misunderstanding, asking for the IP address of the downloader. Support will respond fairly within 2 hours to 5 days with detailed user logs. And, don't forget, files uploaded to file hosting services can also have a built-in logger.
Prevention ❗️ : As above.
4. Use functional robots to obtain Telegram user data
Creating a functional robot is a variation of the above approach. Even if the stalker doesn't know how to program themselves, it's easy to create a functional chatbot that mimics a popular online service or a way to gain access to a closed community. There are some ready-made tools for creating bots: https://t.me/LivegramBot , https://t.me/Manybot or https://t.me/FleepBot . Depending on the bot's declared "function," it can provide users with reports in the form of text messages, hyperlinks, or downloadable files. There are also open source builders for creating automated decoy bots, such as: https://github.com/lamer112311/Dnnme2 .
Precautions ❗️ : Do not use robots casually. Do not send any information about your identity in the course of interacting with a bot, for whatever reason the bot "claims". It is not difficult for people to be wary of a living person, but it is a serious mistake to be extra frank with robots (including robot voice calls)!
5. Log in to one-on-one call to get Telegram user data
Telegram also allows you to fix the IP address of the interlocutor when making private chat calls. This means that two people connect directly and reveal their real IP addresses. To determine the IP address, a network connection monitoring program such as https://www.wireshark.org/ or similar can be used.
Preparedness ❗️ : Proxies, use proxies, and get into the habit of using proxies is the best .
Then, of course, there's the notorious clickjacking. This involves specialized software, usually not for civilian use. As you know, governments can do all of the above.
Finally, regular readers will remember that IYP never recommends Telegram. The only valuable thing about Telegram is its channels feature - the feature we're using. In particular, don't use it to form sensitive groups! But I don't know why it has so many Chinese users. So, please help spread the word and remind your friends about the "preparation" part above.
**
P.S. How to easily know what is behind a shortened link? ——
Before you click on a link, do you have the habit of hovering your cursor over it to see exactly where it leads? You better get into the habit already because it's very important. But in general, a shortened link doesn't tell you anything about it. Meanwhile, on social media, short links lead into the clutches of attackers twice as often as normal links. see above.
🔗 Unshorten.link - is a service that decrypts short links into full addresses. The tool not only shows the actual destination address, but also provides an analysis of URL security.
An extension is available for Chromium-based browsers. Once it's installed, every time you accidentally or deliberately click on a shortened link, you'll be automatically redirected to a link extension page. This is very important to avoid slipping and misoperation.
🧬 https://chrome.google.com/webstore/detail/unshortenlink/gbobdaaeaihkghbokihkofcbndhmbdpd/related
🧬 More related knowledge: https://t.me/iyouport/10429
Attention -
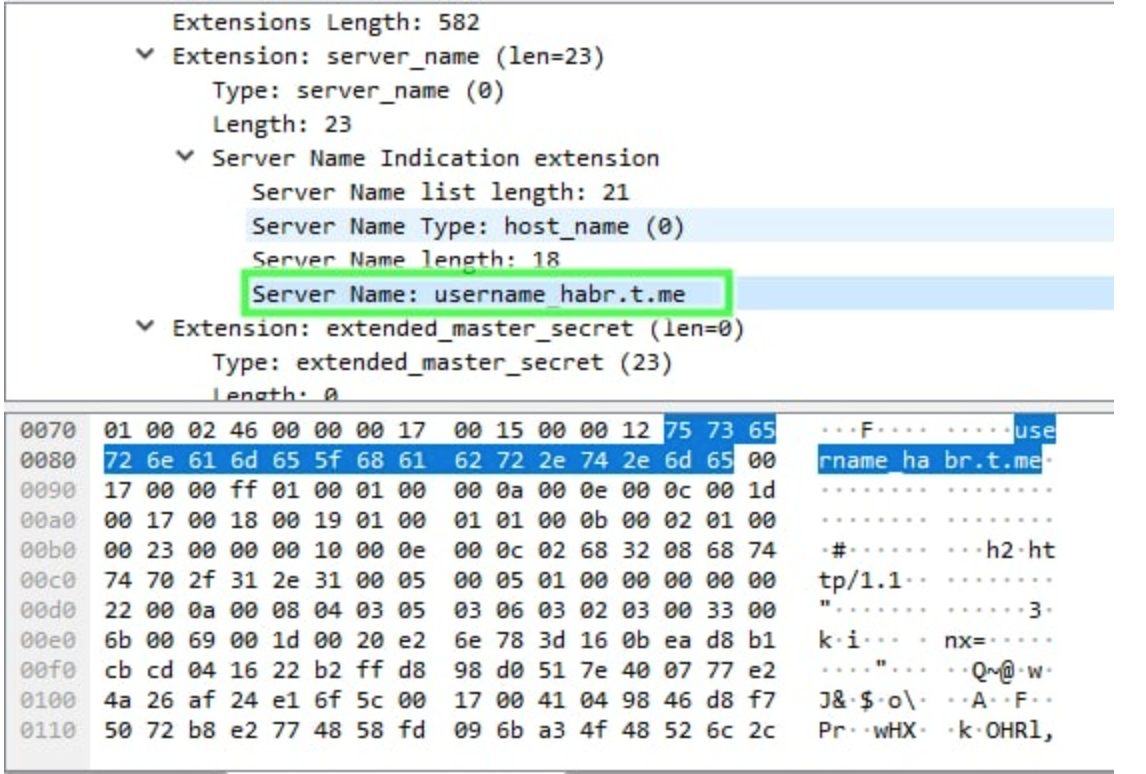
Telegram founder Durov recently revealed that the IM has started supporting a second type of link — with the username first. That is username.t.me .
But as the research found, such linking poses a threat to users' privacy .
Once the link in the form of t.me/username , no one can guess which username you are visiting, the link is hidden in the TLS 1.2 traffic.
But now when you log in to username.t.me , the username is displayed in the TLS Server_Name_Indication extension. Can anyone verify this with WireShark as pictured above.
If you click on a link in the new format and forget to use a VPN, you're revealing your actions to your ISP -- associating an IP address with a username.
The researchers who discovered these risks advise against clicking on links in the new format. ⭕️
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More