
目前是 LikeCoin Chain 验证人 Yoitsu 背后的家伙,以及 CDC/CFC 划水组成员(笑)。偶尔会变身成狐狸。( @foobarz )
原文:A little deeper into end-to-end encryption -- how do public key cryptosystems protect our information?
Wow, what's hidden in the station can't be canceled... (slippery without medicine)
From https://ssd.eff.org/en/module/deep-dive-end-end-encryption-how-do-public-key-encryption-systems-work
When used properly, end-to-end encryption can protect your messages, text, and even files from anyone other than your intended recipient. It also guarantees that the message you receive is indeed from the sender you know (and not someone else pretending to be him/her/it), yes~
Over the past few years, end-to-end encryption tools have sprung up in various fields (and are up to the mark of availability). For example, IM that supports text messaging, voice/video calls, and file transfers like Signal is one of them. These tools make it impossible for listeners to read the content of the message (including the service provider itself).
Do you find some implementations of end-to-end encryption difficult to understand? Before you start using these end-to-end encryption tools, we recommend that you take a moment to understand the basics of public key cryptography.
The public key cryptography discussed in this post is the very foundation on which end-to-end encryption rests. What, do you want to know about other encryption types? Go and read "What should you think of when you see encryption" that we wrote (translated) before~
Understanding the basic principles of public key cryptography will (probably) allow you to use those tools more correctly, such as what public key cryptography can and cannot do, and when and how to use it.
Too long to read the version summary
- In a symmetric cryptosystem, the same key is used for encryption and decryption.
- In the public key cryptosystem, both parties participating in the information exchange each have their own two pairs of keys, called the private key and the public key.
- The public key can be made public, and the private key needs to be protected.
- The sender encrypts the message with the recipient's public key, and the recipient decrypts the message with his own private key.
- The sender signs the message with his own private key, and the recipient verifies the message with the sender's public key.
- Likewise, public key cryptography protects the content of the message, not the metadata.
What does encryption do?
When you transmit some data in an encrypted way:
- Messages that can be clearly read directly (called "plaintext", eg "hello mum") are scrambled into easily incomprehensible forms (eg "OhsieW5ge+osh1aeehah6", called "ciphertext").
- The message, which looked a lot like garbled code, was being delivered online.
- The only recipient of the message can restore it to its original form ("hello mum") by some means, a process called "decryption".
Symmetric Encryption: The Story of Passing Private Information with One Key
Names are the hardest to come up with...and the usual Bob and Alice?
You don't know who Alice and Bob are?
Julia wanted to write a little note to tell her friend César "Meet me in the garden," but she certainly didn't want her classmates to know.
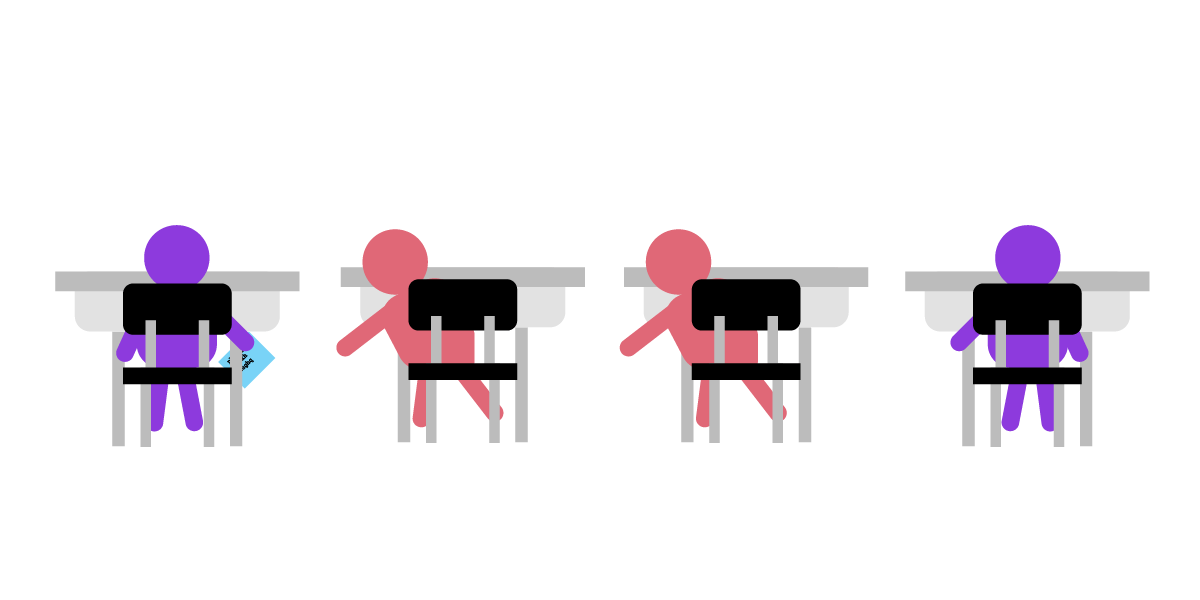
(Did you pass a small note to anyone during class?)
Julia's note will be passed around several times before it reaches César. It's not ruled out that someone in the middle will take a peek at it before passing it on, or make a copy of it and write down the time when Julia wrote the note. (Are you expecting that the classmates who passed the note to you would not mind their own business?)
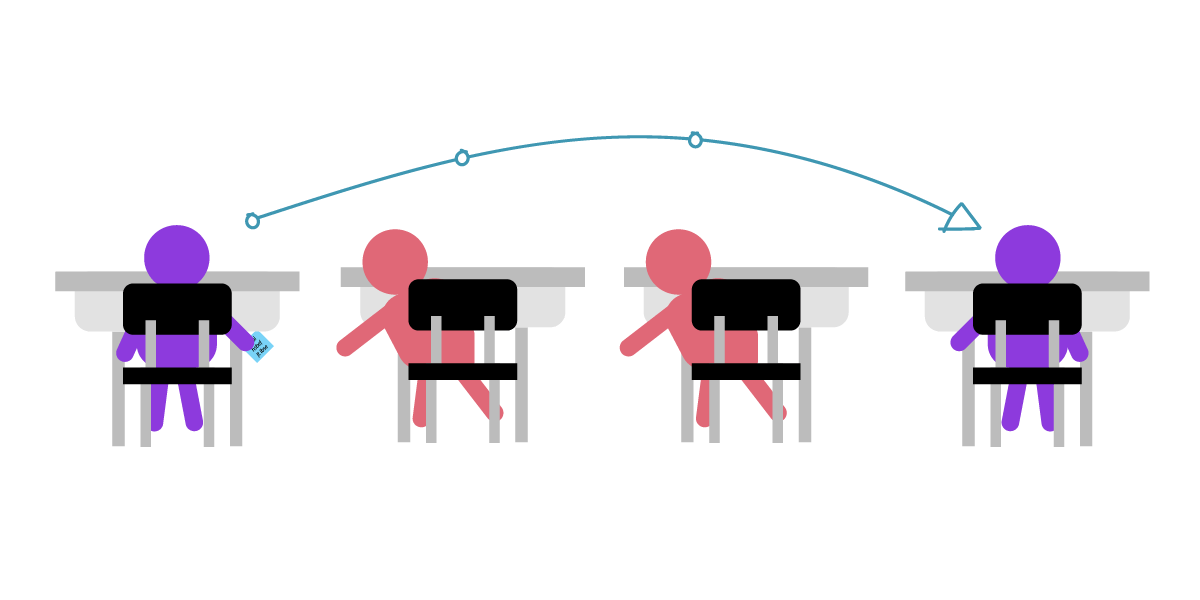
Julia decides to encrypt their message with the key "3", moving each letter back three places, eg A->D, B->E, etc. In fact, the message after this simple key encryption looks like nonsense, and someone with ulterior motives can still "brute force" by trying all the combinations. In other words, they can keep guessing to get the decrypted answer.
This method of shifting three letters is actually an ancient encryption method. According to legend, it was invented by Julius Caesar of the Roman Empire, so it is also called the Caesar cipher. In this example, the number of letter shifts (3) is used for both encryption and decryption, which is called symmetric encryption.
Caesar encryption is actually quite weak (in modern parlance, the key (the number of letter shifts) can be deciphered by means of frequency analysis and the like). But after so long, with the help of magical algorithms and computers, the encrypted keys can be generated longer and longer and harder to guess. Symmetric encryption is also used in more and more scenarios.
(Think about it
Symmetric encryption
any questions? )
However, there is still one problem with symmetric encryption. What if someone eavesdrops while Julia and César are exchanging keys, and then steals the keys? (After all, the key can't be sent encrypted anymore...) Or what if the two of them can't meet in reality? (e.g. quite far away?)
So let's skip the tedious learning process and pretend that they have mastered public key encryption (big boo). An eavesdropper is unlikely to get the keys to decrypt the messages between them - because they don't have to share it at all. In the process of public key encryption, the keys for encryption and decryption are different.
Public Key Cryptography: A Tale of Two Cities with Keys
Take the magnifying glass (what?) in your hand, let's get closer to the problem: how to send only the symmetric decryption key to the receiver under the premise that someone eavesdrops on the conversation, especially when the physical distance between the two parties is very long if?
Public key cryptography (sometimes you also see things like asymmetric encryption, it's the same thing) solves this problem. It allows everyone in the conversation to create two keys - usually called a public key and a private key. Two keys are associated with each other, usually very large numbers with some special mathematical properties. If you encoded a message with someone's public key, they can decode it with their private key.
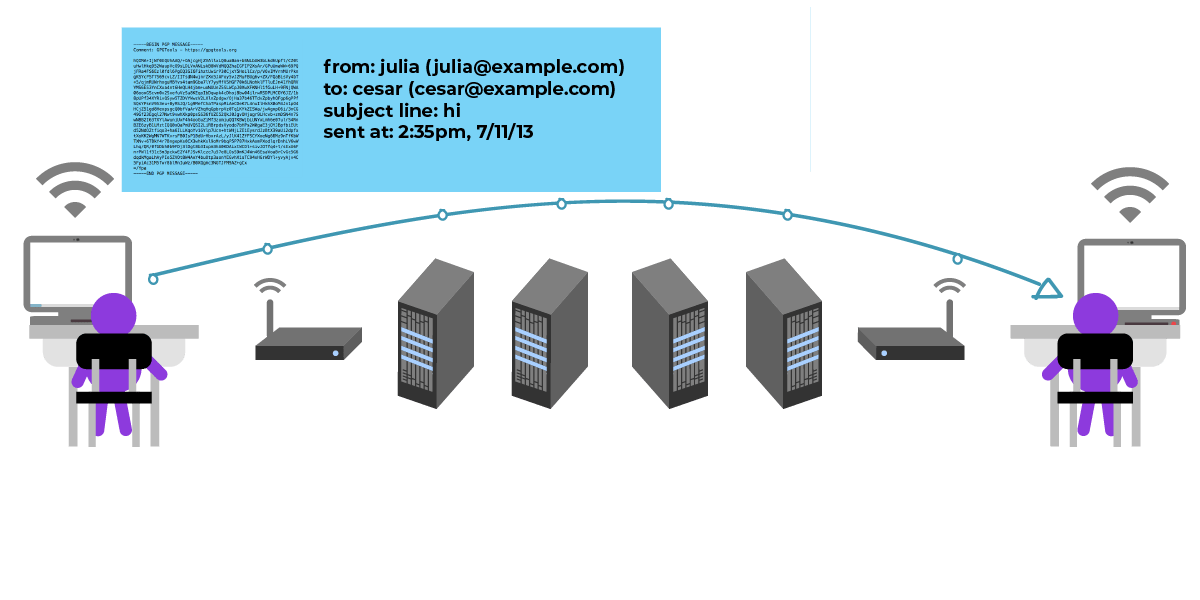
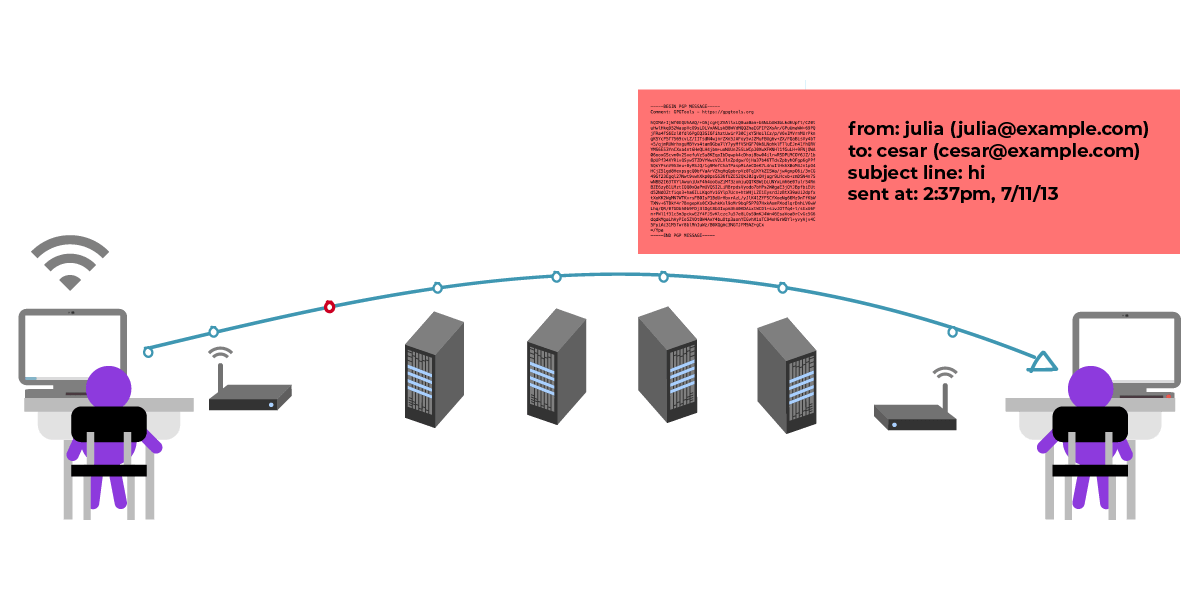
Julia and César now use public key cryptography to send encrypted messages, so the students who passed the small notes before were naturally replaced by one computer after another. They could be the computers between them, such as the Wi-Fi access point, the ISP, the server for the mailbox they use, etc. Naturally, they can also replicate the content of messages sent by both parties and record the time of message delivery.
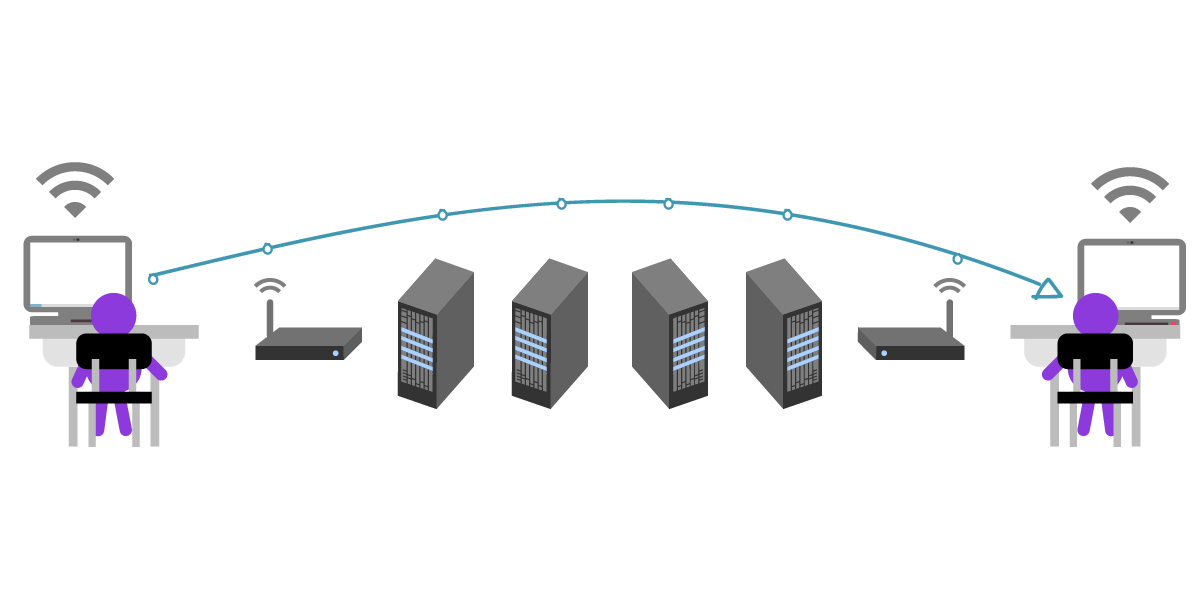
Although they don't mind that someone in the middle will see their news, they naturally don't want others to see the content of the news.
First, Julia needs César's public key, so César sends her public key to Julia (eg, by mail). She doesn't mind passing the public key over an insecure channel, because the public key is inherently something she can freely share.
It should be noted that there are some differences between public keys and real-life keys. Because César can split the public key into several parts and send them out through different channels.
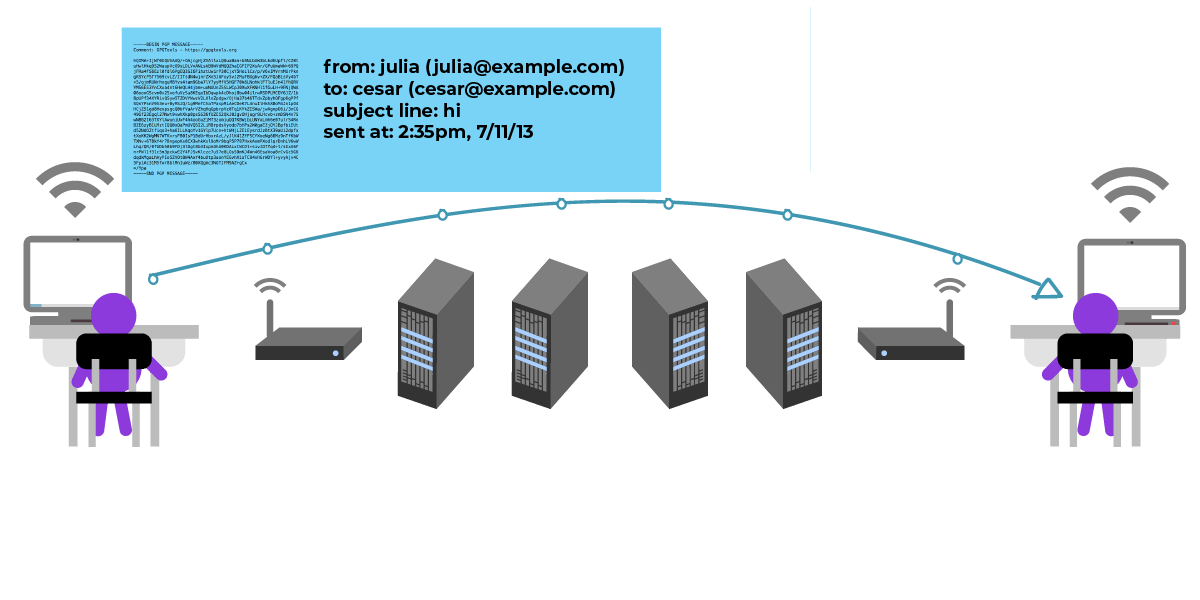
With the public key in hand, Julia can send her encrypted messages:
“Meet me in the garden.”
Julia sent a message encrypted only to César.
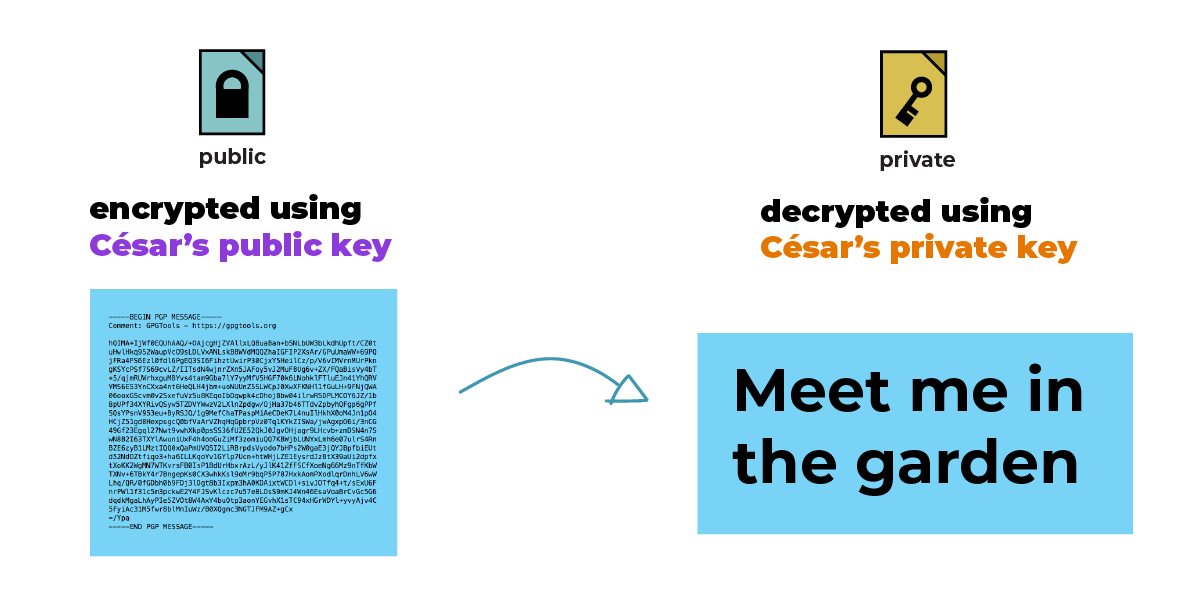
Although they can all understand the message, the rest of the people think the content of the message is gibberish, but the person (or computer) in the middle can still see the metadata, such as subject, time, sender and recipient.
Because the message is encrypted with César's public key, only César and Julia (because they are the sender) can read the message.
César decrypts the message with her private key:

Brief summary:
- Public key cryptography allows you (and others) to pass public keys over open and insecure channels.
- Once you have your friend's public key, you can send them encrypted messages.
- Your private key is used to decrypt encrypted messages sent to you.
- Man-in-the-middle - like service and network providers, can see some metadata in the process of message delivery, such as who wrote the message, who it was sent to, when it was received or sent, and the subject of the message, etc.
(Do you think you can sit back and relax now?)
One more thing...how to identify a counterfeit?
In the above example, the man-in-the-middle is able to see the metadata throughout the process.
So let's be a little nasty, some middleman wants to know what they're talking about, so he's listening in on them.
Bad guys can use some tricks to get Julia to get a fake public key. Julia didn't notice that this wasn't César's public key, but it was used to encrypt the message to be sent to César.
The bad guy then gets the message that was supposed to be encrypted to César, and it can see the original content of the message before sending it to César.
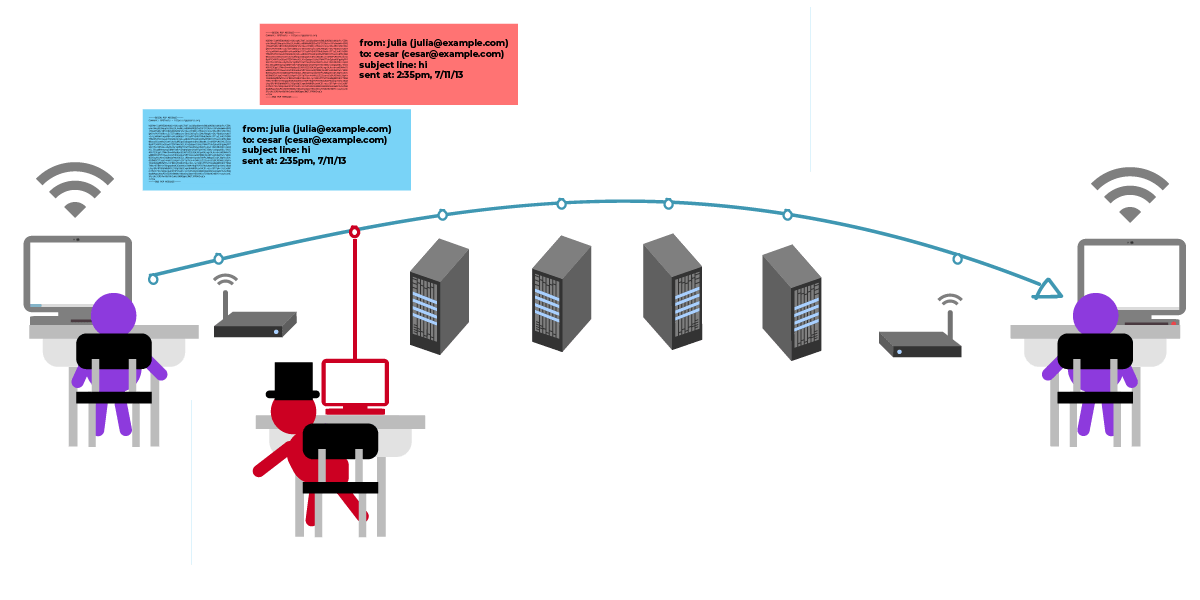
It is even possible to tamper with the content of the message:
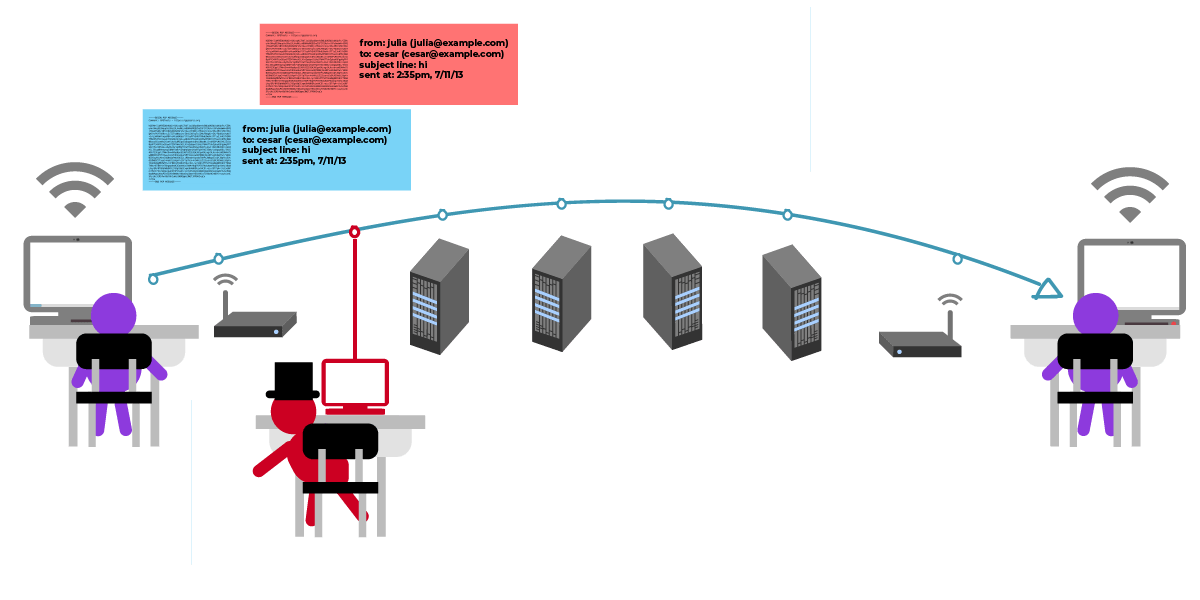
So Julia and César met in the garden as scheduled, but I didn't expect that someone had been waiting here for a long time...
This is the so-called "man-in-the-middle attack", in fact, the attacking guy is not necessarily a human... Fortunately, public key cryptography has the means to defend against this kind of attack.
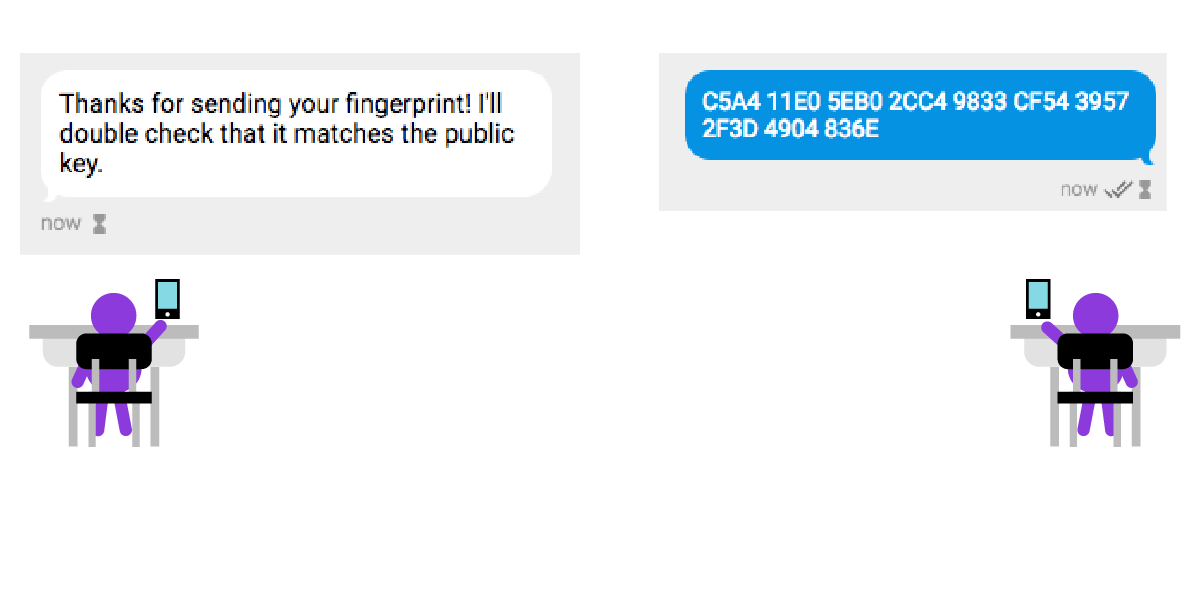
Public key cryptography allows you to confirm that a key really belongs to someone you know through a method called "fingerprint verification" ("fingerprint" refers to a public key calculated by a digest algorithm. string of letters, usually much shorter than the public key) This process is best done in real life. If you can meet someone face to face, you can check whether each letter of the fingerprint of the public key that both parties have is the same. Although it's boring to read one by one, in order to ensure that the private key in your hand really belongs to someone you know, please bear with it...
Other end-to-end encryption applications have similar fingerprint authentication mechanisms, although the methods may vary. Some methods are more traditional, and you should be careful to compare the content displayed on the two screens to see if they are the same. Some methods are relatively "fresh", such as using the device in your hand to scan the QR code displayed by the other party to "verify" a certain device.
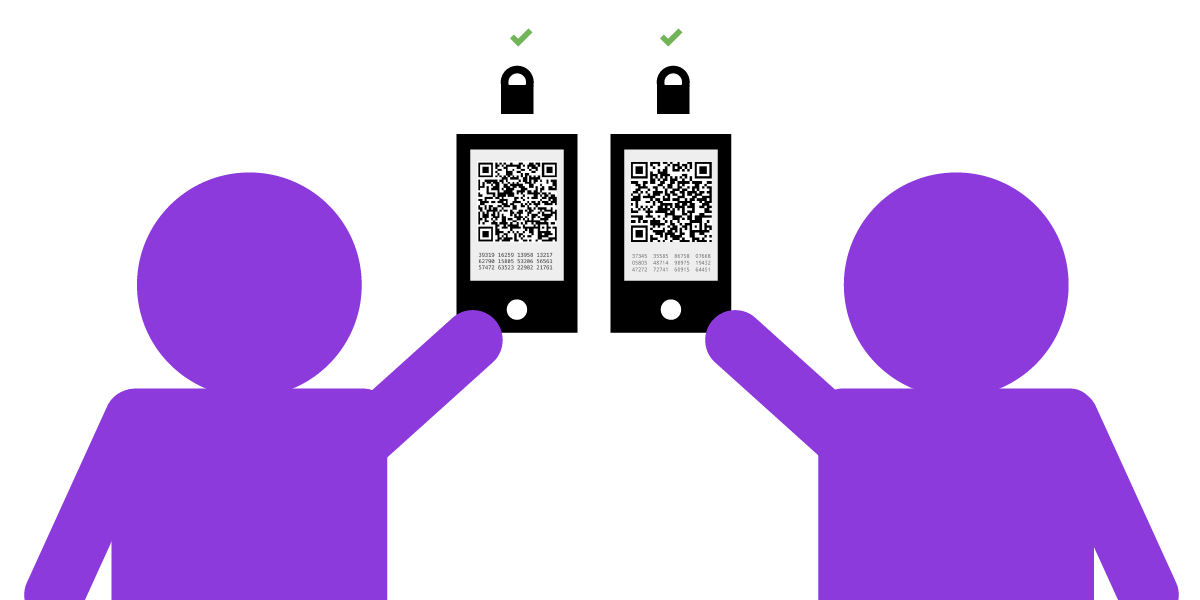
If you can't meet the other person (worried about going back or not...) , you can exchange fingerprints in other known safe places, such as end-to-end encrypted chat software, or an HTTPS website.
in conclusion:
- A man-in-the-middle attack is when someone intercepts a message passing between two parties, and the attacker can modify the message or simply listen.
- Public key cryptography allows you to defend against man-in-the-middle attacks by verifying the identities of the sender and receiver, a method known as "fingerprint authentication".
- Your (or your friend's) public key also contains some information called a "fingerprint" by which you can verify the identity of the public key holder.
- The private key is used to decrypt messages sent to you and to sign messages in your name.
Signature era
Public key cryptography saves you from risking sending the decryption key to the recipients of your private messages, because they already have it, their private key. Because the public key is only used for encryption and cannot be decrypted, you (and the recipient of your message) can share the public key, and all you need to send private information is the recipient's public key.
But that's all... We already know that messages encrypted with a specific public key can only be decrypted with the private key corresponding to the public key. In fact, the reverse is also true, a message encrypted with a specific private key can only be decrypted with the public key corresponding to the private key.
What, what's the use of this? You encrypt a message with your own private key and let anyone decrypt it with your public key... Don't worry, think again, for example, you wrote a sentence and then encrypted it with your private key. Everyone can decrypt your message, but only the person who holds your private key can write it. If you can carefully protect your private key, most likely only you have your own private key, and only you can send this message~
By encrypting the message with your private key, you ensured that the message was only written by you. Does it sound familiar? That's right, you've done the same with your digital messages just as you signed your own name somewhere in real life.
Signatures are also tamper-proof. After all, most of the time, someone else can't re-sign with your private key... So a signed message ensures that it came from a certain source and doesn't get messed up in transit.
Review: About Public Key Cryptography
Public key cryptography allows you to securely send messages to someone who knows the other party's public key.
If anyone knows your public key:
- They can send private messages that can only be decrypted with your private key.
- You can sign messages with your private key, and they can verify that the signature is valid with your public key.
If you know someone else's public key:
- You can decrypt the message from him/her/it, and you can verify that the message really came from that one.
So obviously, the more widely your (or anyone else's) public key is spread, the more useful this encryption method will be. Since the public key can be shared, you can also compare it with something in reality, such as the address book or the phone yellow pages: it is public, people know where to find it, and you can share it widely.
As for the private key, you'd better compare it with something in reality, such as the keys to open doors or various locks. Your private key is used to encrypt and decrypt messages, so be sure to treat it like your real key.
Why is your private key apparently (so) important? If you lose the key, you may not be able to open somewhere. The same goes for the private key in public key encryption, if you lose the private key, you cannot decrypt the message sent to you. If anyone gets your keys, he can open certain places in your name. If someone else gets your private key (eg physical access to your computer, via malware, or just because you handed it out like a big donkey, etc.), he can read your Encrypted information, or impersonating you to do something.
I've also heard of some governments trying to steal someone's private key (such as forcibly confiscating computers, phishing attacks, or trying to install malware, etc.). This is of course a compromise of the security of public key cryptography. Since you don't encounter such a coercive situation most of the time, let's change the chestnut: a pickpocket stole your key when you stopped to rest, and then went to get a new one, and put the original key quietly. Put it back in your pocket. You may feel like nothing happened, and then find out that someone has visited your house...
So it's time for the clichéd threat modelling: estimating the risks you might encounter and designing countermeasures accordingly. For example, since you're worried about who is poaching your private key, you probably won't use the end-to-end encryption scheme in some browsers, and you'll try to make sure that your private key stays only on your own computer and not on your computer. Not elsewhere (like someone else's server or the so-called cloud).
Summary and typical examples of public key cryptography: PGP
Although we demonstrate symmetric encryption and public key confidentiality separately, there is also an opportunity to use symmetric encryption in the process of public key encryption. For example, remember that in operation, public key encryption encrypts the key that decrypts the symmetric encrypted message. PGP is a typical example of combining symmetric encryption and public key encryption.
(You sometimes see guys like openPGP or GnuPG, because PGP itself is private, so many people have developed similar software, and they all support the openPGP specification. The most commonly used one is the one developed by GNU GnuPG a little...)
So what exactly are those keys and how do they come together?
Public key cryptography is based on the premise that there are two keys, one for encryption and one for decryption. Basically, you can pass one of these keys over an insecure channel like the Internet, which is called a public key. You can publish the public key anywhere without compromising the security of the encrypted information.
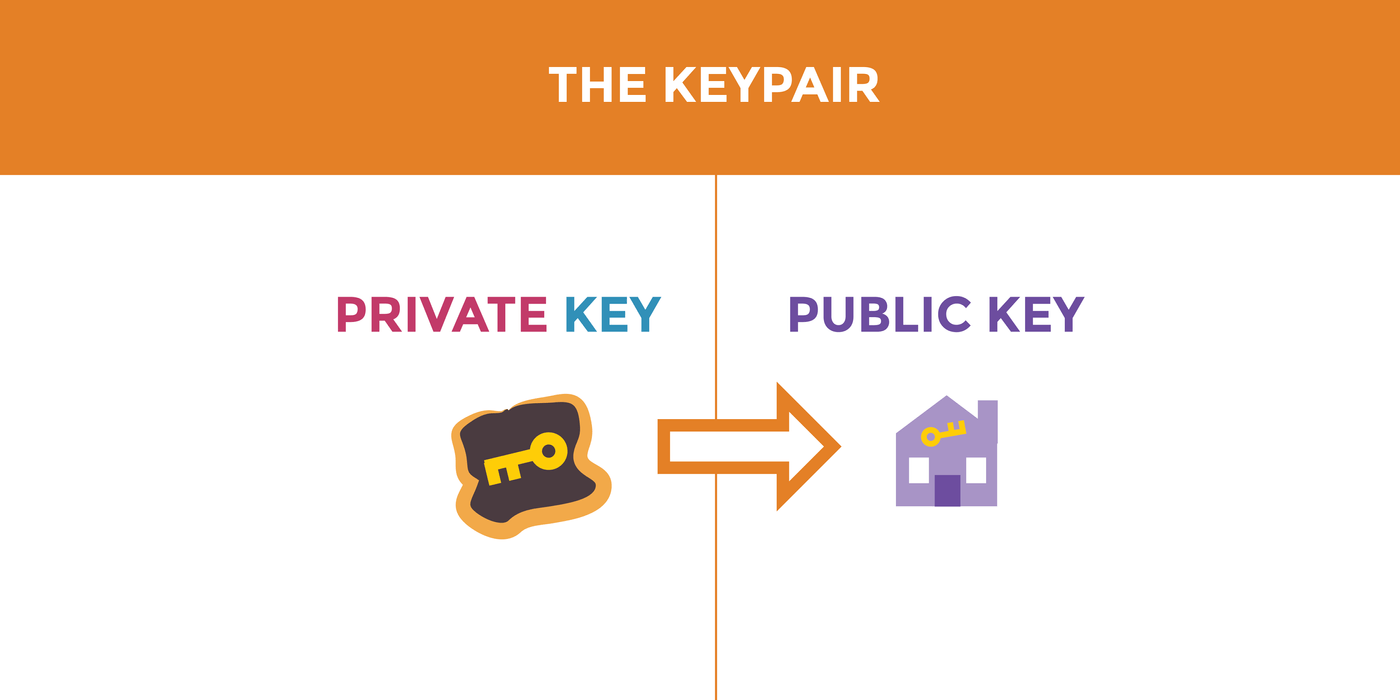
Since the public key can be shared, you can also compare it with something in reality, such as the address book or the phone yellow pages: it is public, people know where to find it, and you can share it widely.
As for the private key, you'd better compare it with something in reality, such as the keys to open doors or various locks. Your private key is used to encrypt and decrypt messages, so be sure to treat it like your real key.
Let's take a look at an algorithm that is often used in public key cryptography to generate keys, called RSA (after the three scientists who invented it, Ron Rivest, Adi Summer (named after Adi Shamir and Leonard Adleman).
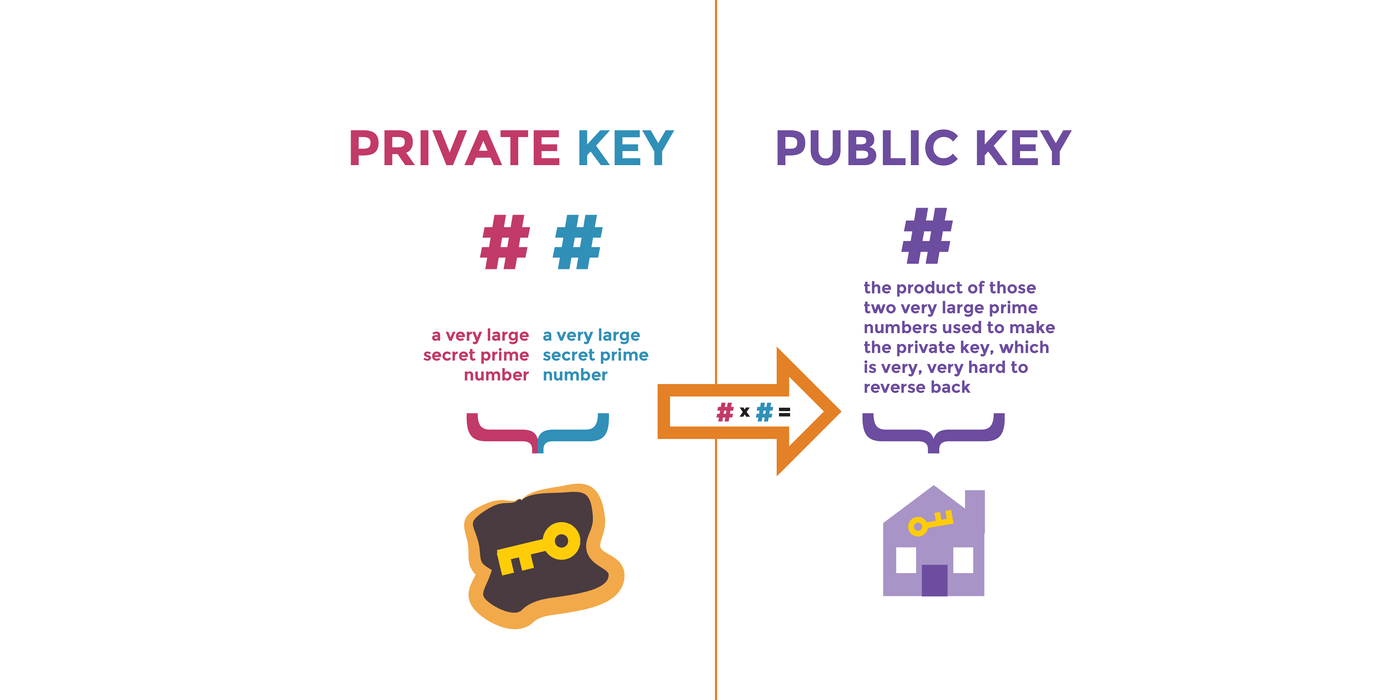
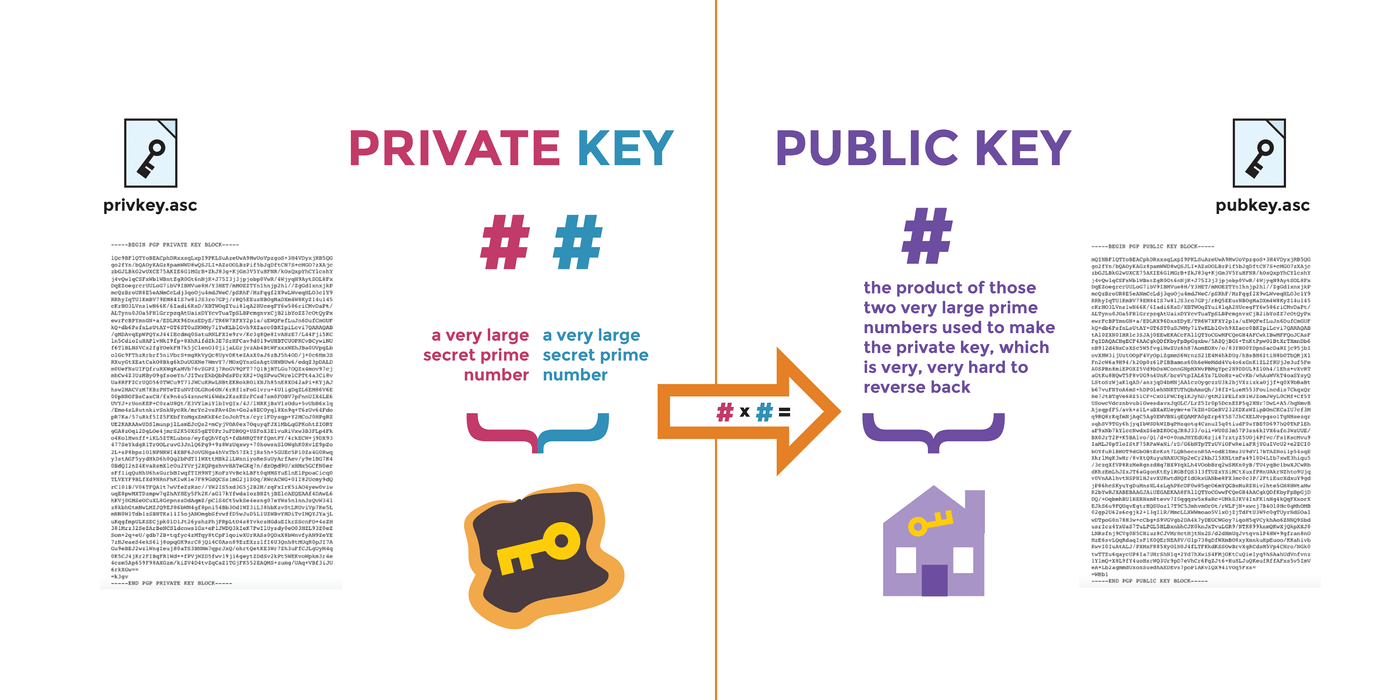
The public key and the private key live and die together (? Just generated together...), and both depend on a very large secret prime number. The private key consists of two sets of very large prime numbers, and the public key is their product. Attempts to deduce the two prime numbers of the private key from the public key are very difficult.
why? Because there is still no fast and stable algorithm for factoring prime factors... As time goes on, modern cipher suites also allow users to generate larger and harder to guess prime numbers as keys.
(And over time, more modern encryption algorithms were invented, like Elliptic Curve Cryptography (ECC) and ElGamal, among others.)
This is the power of public key encryption. The information exchanged by the two parties participating in the encrypted information exchange in the insecure channel is only the public key of both parties! Since private keys do not need to be exchanged, (ideally) private keys are naturally not leaked.
Remember: public keys of both parties are required for public key cryptography to work.
In other words: the public and private keys are generated together, intertwined like yin and yang.

The public key can be searched and shared, and you can send it wherever you want. If you don't mind revealing your email address, you can put it on social media or on your own website.
The private key needs to be securely protected. Because the more it is, the more difficult it is to keep it safe and secret, so you definitely just want to keep a handful (and don't lose it) rather than share it or have copies all over the place. (?)
How PGP works
So with all that said, how exactly does PGP work? Suppose you want to send some private messages to Aarav:
- Aarav has a pair of keys, and like a good user of public key cryptography, he puts his public key on his website with HTTPS.
- You download his public key and use it to encrypt some messages to send to him.
- Since only he has his own private key, only he can decrypt messages sent to him.
PGP (Pretty Good Privacy) is a combination of details that focus on creating and using public and private keys. You can create a pair of keys, protect the private key with a password, and encrypt and sign text with the private and public keys.
If you must sum it up: Protect your private key with a strong enough passphrase, and keep it in a safe place.
Metadata: Public key encryption is not a silver bullet
Everything about public key cryptography (secret, consistent, tamper-proof) is protecting the content of the message. But this is definitely not your only privacy concern, as mentioned earlier, information about a message (sometimes referred to as "metadata") can also reveal the content of the message.
In some cases, simply exchanging encrypted information may put you at risk. Such as dissidents in certain regimes, or simply refusing to declassify messages.
It can be quite difficult to fake the fact that you are communicating with someone. In the preceding PGP, one possible approach is for both parties to use anonymous mailboxes accessed through an anonymous network such as Tor. In this case, PGP is still very useful, whether it is to protect the private messages of both parties among other people, or to prove that the author of the message and the delivery process have not been tampered with.
Having said all that, try out some end-to-end encrypted apps for yourself, such as Signal available for iOS and Android .
Like my work?
Don't forget to support or like, so I know you are with me..
Comment…