
盡情生活,在浩瀚間留下存在的證明。 來自臺灣.臺北|音訊科技與聲響|社會論題與資訊科學|區塊鏈 / 去中心化未來|存在指南選物商店 https://www.waytoexist.com/
The Specific Practice of Decentralized Network — Deeper Network Creates an Evolutionary VPN | Existence Guide Way To Exist

For those of us who are traveling on the Internet, few people have never been in contact with VPN (Virtual Private Network), even if it is not used frequently, it may be due to the cross-server requirement of playing online games and watching the cross-region of streaming platforms. Need to use VPN to work.
Of course, this well-established technology faces various controversies and challenges. For example, the most common one is that the server side of the VPN captures the data (Server Log User Data) that the user sends and fills in when connecting through the Tunnel.
With the rise of information security awareness and the need to ensure more privacy in response to remote work, a new technology is bound to emerge—
A technology that inherits the original advantages of VPN and adds some new technical improvements, a technology that is more in line with the convenience and security of contemporary people in using the Internet.
What is a VPN?
In this article, I mainly focus on introducing the new technology DPN, so I will only briefly present the use of VPN here. For detailed information on technology orientation, please refer to the writings of experts on major forums.
VPN (Virtual Private Network), Taiwan is translated as virtual private network, virtual private network, which allows users to make exclusive connections on the public network through network connections encrypted by various protocols. The technology of extending the road to the public network, combined with various encryption protocols, can allow users to browse, store and transmit data in the Internet more securely.
This technology enables network users to convert the public network into a private network by connecting to the VPN provided by the exclusive provider even at the remote end, improving the security and management effectiveness of the original network. The "various agreements" mentioned here are the most common ones based on various protocols derived from the Tunnel Protocol (channel, tunnel agreement), with encryption (VPN can also be classified according to the level of encryption) or various "imitation" methods. To achieve a higher level of anonymity (it is common to display a network protocol address different from the user's native access point through the Server, commonly known as switching IP location), so that only authenticated users can access and use it.
VPNs seem to be quite practical and powerful, and they can also provide services such as financial encryption, but it is clear that human development does not stop there.
Looking at the application and technical layout of virtual private networks, we can find the following defects:
- Server-side access and sales of information
Many paid VPN companies (the reason for not mentioning free VPNs here is that the use of free VPNs is usually only used for cross-regional games, streaming platform video appreciation, etc., and less sensitive information transmission) The services provided all emphasize encryption and information security, but the server itself is likely to be an enemy that people cannot guard against. For example, unscrupulous manufacturers directly access user information for sale or VPN service providers in China have to follow government requirements. , to disclose user information to government agencies.
Example: Facebook Research VPN event
- not so safe
Many people believe in the anonymity of paid VPN IP migration, but if there is no special setting, in fact, backtracking the address is something that many information security experts can do. Moreover, the server provided by the current VPN technology is centralized management, intercepting and decrypting information. Hacking techniques are also following in the wake of the growing sophistication of encryption.
- Less intelligent in how it works
On the existing VPN technology (mostly), once you connect to the server provided in a certain area and change the IP, you can use the specific services in that area, and at the same time, the device cannot (mostly) browse and access at the same time that has not been used before. Regional content during VPN, such as overturning the wall into a certain country, will be blocked from accessing the original foreign website.
so? A more secure and smart VPN?
At the beginning of this year (2022), the author discovered a technology company located in Silicon Valley in the United States, trying to use the characteristics and technology of blockchain to improve the long-standing VPN problem. The solution they proposed is named:
DPN (Decentralization Virtual Private Network), which is the decentralized virtual private network.
This technology is quite interesting, and I briefly explain it here:
There is a physical device (Hardware), connected to your own Router or even directly connected to your computer, you can turn the device network you are currently using into a node (Node), and this node is also another Deeper Network Hardware user's Server.
That is to say, by using the physical device launched by Deeper Network, many nodes can be created all over the world, and these nodes can be connected by another node (user) as a Tunnel. In this way, a decentralized A virtual private network managed by (individual Nodes).
Deeper Network has put a lot of effort into the advantages brought by physical devices. For example, the newly launched Pico advertises that it can block advertisements, enterprise-level information security protection, super easy connection to use, and even can be used for mining. Mine, (for example, by sharing bandwidth) to earn the exclusive cryptocurrency $DPR.
Source of the above image: Deeper Network official website / Medium
In addition, among the above-mentioned shortcomings of VPN, the operation is less intelligent. Deeper proposed that a single node can choose to operate with multiple tunnels.
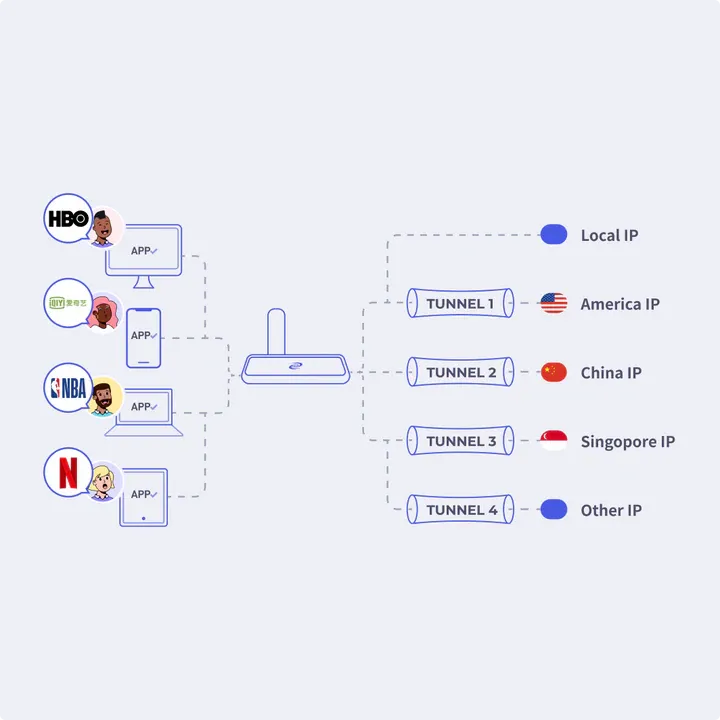
The above picture is from Deeper Network 's official Medium , which says that the device can select multiple nodes in different regions at the same time (just like selecting multiple Different Region Nodes On Private Network), and when browsing, accessing and switching APPs, Smart Route The function will automatically switch to the corresponding node, and there will be no problem of not being able to switch regions freely and smoothly.

Epilogue
Of course, whether it is really so magical and easy to use remains to be commented on by Pico users. However, the author is looking forward to this pioneering effort to truly apply decentralized network and blockchain technology to daily life. Yes, this may be an epoch-making breakthrough in Internet applications (I think so, but still need to continue research and opinions.), even comparable to the sensation caused by Bit Torrent when it was launched.
live to the fullest,
Leaving a proof of existence in the vastness. |Existence Guide Way To Exist
Like my work?
Don't forget to support or like, so I know you are with me..
Comment…