CoinEx Research Institute | New generation privacy public chain project: represented by Oasis Network and Secret Network
Privacy is a label that has been surrounding the crypto industry since the birth of Bitcoin. One of the most important features of the current mainstream blockchain networks represented by Bitcoin and Ethereum is that all transaction records are completely open and verifiable. In addition, each user's address is independently generated through a random algorithm, and since this generation mechanism is completely random, all addresses are inherently anonymous. This anonymity is what we often talk about early on about privacy. In addition to the anonymity of addresses, some simple schemes have been constructed to make transactions more private. Early various privacy projects basically built solutions around the problem of anonymity, and they used complex cryptography to obfuscate transaction details to protect user privacy and improve security. Simply put, when an old address is exposed, users transfer assets to the new address. These privacy projects are only responsible for cutting off the direct connection between the old and new addresses through operations such as currency mixing during the transfer process.
However, when the blockchain technology gradually transitioned from the Bitcoin era to the smart contract era represented by Ethereum, the impact of the newly born various applications on the original anonymous account system is also increasing. Early addresses may have been used only to store purchased cryptocurrency. Today, encrypted users also need to use these addresses to buy NFT avatars, associate social accounts, hold function variable names, save game items, or publish articles in Mirror. These activities make it increasingly expensive to continue to maintain the anonymity of these addresses, and when one wants to be anonymous and then do transfers between addresses again, the process is becoming more and more complex to the point that it is almost no longer feasible. Therefore, it has become increasingly difficult for traditional coin mixing privacy solutions to meet the new needs of these users.
Therefore, the industry needs more advanced privacy solutions. Even if the user's address is already a public real-name address, they can hide the amount of assets they hold according to their needs. When interacting with the DeFi protocol, there is no need to worry about the information being disclosed. Or even if the purchased NFT is stored in the wallet address, you can choose whether to disclose it according to your own wishes.
For this demand, early privacy public chains such as Monero and Zcash cannot meet the needs of DeFi users because they currently do not support smart contracts. The market needs a new programmable privacy public chain to meet these new needs of users. At present, in the entire market, there are two representative public chains that can support smart contracts and can customize the privacy of transactions on the public chain - Oasis Network and Secret Network. This article will briefly analyze and introduce these two privacy public chain projects.
Data from CoinEx Research Institute
Secret Network
Secret Network is an L1 public chain that independently supports privacy computing based on Cosmos SDK and Tendermint BFT. Similar to other Tendermint-based chains, Secret Network has a block time of 6 seconds and can process thousands of transactions per second. The chain currently supports 50 active validators with an average of 167 delegators per node. As a member of the Cosmos ecosystem, Secret Network can also seamlessly integrate the IBC cross-chain protocol and can quickly interact with other public chains in the Cosmos ecosystem.
Traditional privacy public chains, such as ZCash and Monero, or Ethereum DApps such as Tornado Cash, can obfuscate the flow of encrypted assets to a certain extent, and are very suitable for private transactions or wealth storage, but such privacy technologies have been unable to meet the new requirements. A user's need for anonymity or security in a financial environment. For privacy networks to attract users in the DeFi era, their privacy functions must also be extended to the application layer, which is also the value that Secret Network can provide to existing privacy technologies. Through cross-chain bridges, DeFi and NFT facilities, Secret together forms the foundation of the on-chain application ecosystem.
1. Secret cross-chain bridge
For a nascent L1 ecosystem, liquidity is a key issue. One of Secret Network's main solutions is to link to other networks with existing user bases and liquidity pools through cross-chain bridges. With the right incentive structure, Secret Network can share the economic activities generated by other blockchains, and can build a new economic ecology from scratch without spending too much resources. The project launched the first cross-chain bridge on December 15, 2020, connecting with Ethereum. Since then, it has also deployed cross-chain bridges in BSC and Monero, and is developing a communication gateway to Astar Network and a cross-chain bridge to the fast-growing Terra ecosystem.
Interoperability is also one of the core reasons why Secret Network chose to build on the Cosmos SDK. The Cosmos SDK allows developers to add new functionality through plug-and-play modules, one of which implements the Inter-Blockchain Communication (IBC) protocol, allowing the network to communicate with other IBC-enabled chains.
2. Secret DeFi
Mere cross-chain bridge facilities are not enough to attract funds from other ecosystems to flow into the Secret ecosystem. As an L1 public chain, it also needs a DeFi ecosystem that provides high incentives to attract more initial users. Secret now supports SecretSwap, SEFI's governance token, and peer-to-peer auction marketplaces, which together form the foundation of DeFi facilities.
3. Secret NFT
The privacy properties of Secret Network can be extended to multiple token types, including NFTs. Secret NFTs share the same characteristics as Ethereum's ERC-721 tokens, while offering three new features:
1. Hide ownership of rare items;
2. Privatize metadata fields (how NFT signatures connect to off-chain data like artwork);
3. Control access to linked content.
The application project of Secret NFT is still relatively small. Secret Heroes is the first game in the Secret network. According to the latest roadmap of the project, the NFT market is in preparation. Although the current progress of NFT-related projects is slow, this is also an exploration of privacy-based NFTs.
Oasis Network (ROSE)
Oasis is also an underlying blockchain built on the Cosmos SDK with both privacy protection and high performance. Among them, privacy protection is native to Oasis, that is, the Oasis blockchain has its own privacy protection feature, which is also an important feature of Oasis currently different from other blockchains. Its upcoming ParaTime Cipher will support privacy smart contracts. In private ParaTime, nodes need to use a secure computing technology called "Trusted Execution Environment". A Trusted Execution Environment (TEE) is similar to a black box for smart contract execution. By using key management, encrypted data enters the black box (Secure Enclave) together with the smart contract. Here the data is decrypted, processed by the smart contract, and then the decrypted data is encrypted before being sent out of the black box.
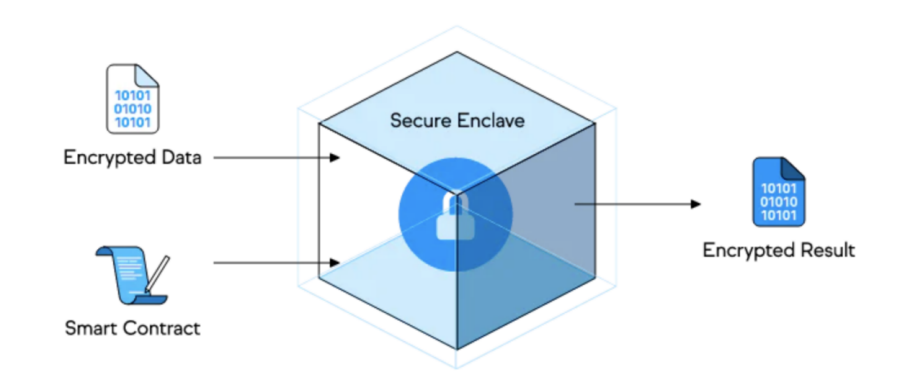
The black box only needs to output the result of "yes" or "no" to the outside world through the smart contract, that is, to verify whether the privacy information uploaded by the user is true, without displaying the user's own privacy information, which solves the problem of "needing private data but not showing data" itself” dilemma, which is similar to zero-knowledge proofs. TEE is related to hardware. It can be an area on the CPU of a computing device (such as a mobile phone, computer, etc.), used to store private information, and can ensure that even if the mobile phone or computer system is compromised, this area cannot be accessed. information.
In addition to the privacy protection features, another feature of Oasis is high performance. The way to achieve high performance is to separate consensus and smart contract execution into the consensus layer and ParaTimes layer, respectively. Both layers are integrated to provide the same functionality as a single network. The computing layer of Oasis is currently divided into 3 Paratimes that can be executed independently of each other. Each Paratime can perform different types of calculations, and then the consensus layer can reach a consensus on the result state of the calculation, without the need for the consensus layer to participate in the transaction calculation itself. With this flexibility, workloads and upgrades processed on one ParaTime will work together by consensus to ensure network security and finality independently, without affecting other ParaTimes.
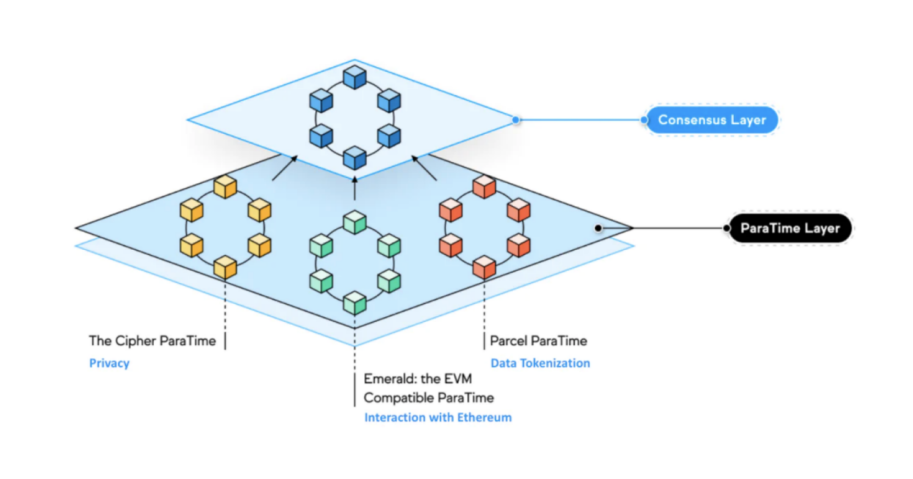
Outside the computing layer, the consensus mechanism adopted by Oasis in the consensus layer is PoS. Each verification node joins the network in a decentralized manner and verifies the transactions that occur in the network. This hierarchical partition design is a highlight of Oasis. In comparison with other public chains, although Oasis has no absolute advantages in some aspects (such as TPS), it has the characteristics of parallel transaction processing and privacy protection, making It is relatively comprehensive in function.
Summarize
In summary, privacy issues will become an increasingly important topic in the future, and there is a huge rigid demand, so the chance of Alpha in the privacy track in the future is very high. The biggest problem in the current privacy track is not privacy, but the high cost, inefficiency and poor user experience brought about by protecting privacy. Therefore, many privacy technologies are still not popular. Compared with privacy, users will be more inclined to choose applications with high efficiency and low cost. Therefore, for the privacy public chain, it is necessary to pay more attention to the ecological development of the public chain, the technical development route (whether it is compatible with EVM, etc.), performance issues (TPS, etc.), gas fees, etc. It is believed that with the development of the privacy public chain ecology and the improvement of user experience in the future, several leading projects with high applicability will emerge on the privacy public chain track. Privacy public chain, the future can be expected, let's wait and see!
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More