Cosmos Eco-DVPN White Paper Full Version
Vision Introduction
The purpose of the Sentinel ecosystem is to authorize universal access to the Internet in a trusted and provable way. This will allow organizations and individuals around the world to leverage Sentinel's cosmos-based blockchain to build cost-effective, scalable, distributed and decentralized network solutions.
- Decentralized consensus
- Open Source Network Integration
- Distributed community node network
The internet has created an intertwined form of global awareness capable of enormous positive impact. However, the importance and power of the Internet's ability to spread information is under threat. The rapid increase in global internet censorship and massive data collection, as people become increasingly reliant on the internet in this day and age, violates fundamental human rights to information and privacy.
The initial focus of the Sentinel ecosystem is to provide a framework for the construction of decentralized virtual private networks (dvpns). VPN applications are used by individuals all over the world to access geo-restricted content by connecting to servers located in regions where the content they want is unrestricted, while ensuring the privacy of their interactions by establishing an encrypted connection . Whether the purpose is to access restricted content or to increase the security of the data they transmit over the Internet, individuals around the world demand secure, cheap and reliable VPN services.
With the release of the Cosmos IBC that allows for cross-chain interoperability, Sentinel will be able to provide a private network or dVPN layer within the Web 3.0 infrastructure stack. In the near future, it will be possible to build a fully decentralized DeFi application, namely:
- Hosted on the handshake network;
- Data is stored in ipfs;
- Utilize the computing resources of the Akash network;
- Integrate with dvpn built on Sentinel network to provide web-level privacy and security for applications and their users.
In its inception, VPN technology primarily focused on establishing a secure tunnel between an organization's servers and its members to ensure encrypted data transmission. Over the past decade, modern consumers have begun to associate VPNs not only with traditional enterprise-centric narratives, but with a whole new narrative that revolves around their concerns about privacy, Internet security and global data accessibility concerns. It is because of these concerns that we are witnessing a boom in the VPN industry, which is expected to grow by 15% annually to reach $75 billion by 2030.
Currently in the VPN field, VPN applications that consumers can use can neither prove the authenticity of their claims nor keep their promises to users while guaranteeing user "privacy" and "reliability". big contradiction. This paradox has been exposed almost quarterly in recent years, and VPN networks have been deliberately storing and collecting user data, while at the same time, there have been major security breaches. The VPN industry is currently a monopoly, with the vast majority of leading brands sharing the same owner. At the same time, consumers lack trust in the back-end functionality of these similar products.
In contrast to these mainstream "consumer-facing" VPN applications, a robust, holistic "dVPN" network (a term originally coined by Sentinel in 2017) has the following advantages:
- Provable Encryption: Establish end-to-end encrypted provability between the user and the server the user wants to access the data through an open source transparent and application integrity verification system
- Bandwidth Proof: There is a bandwidth provable system that allows server providers to provide bandwidth in a trustless and provable way in exchange for user-agreed compensation
- Proof of No Logs: Ability to provide evidence that application developers did not centrally store logs related to user browsing or data history
- Distributed "Exit Nodes": Have a network of "Exit Nodes" (dVPN servers) whose ownership is distributed among many participants who do not know the identity of the user
- Distributed Relay Network: Robust relay network with strong governance and participation to reduce the risk of bad actors, while ensuring that exit node hosts are unaware of users’ identities
Stakeholders participating in the sentinel network include:
- Validators: Consensus participants in the upcoming Cosmos Hub sentinel who are responsible for the security of the network and participate in the governance of the Sentinel ecosystem
- Users: End users want access to a dVPN built on the Sentinel framework for secure access to use the internet in a provable way
- dVPN Node Hosting: Community members intend to make money by hosting an exit node or a relay node (meeting certain required service level thresholds), providing unused bandwidth to dvpns built on the Sentinel network
- dVPN App Creator: Creators who build dVPNs on the Sentinel framework while using Sentinel dVPN zones as their infrastructure layer. App creators are responsible for user acquisition and marketing to generate revenue to be able to pay for dVPN node hosting
Decentralized VPN Industry
Sentinel is not a single dVPN application, but an independent network, and the dVPN application is built on Sentinel's dVPN protocol framework.
The goal of the Sentinel ecosystem is to decentralize the VPN industry and bring "dVPN" to mainstream consumers. However, this goal will not be achieved by publishing and maintaining a single consumer-facing application (Sentinel dVPN), but by first building and developing a framework that can be used to create an independently operating decentralized VPN network.
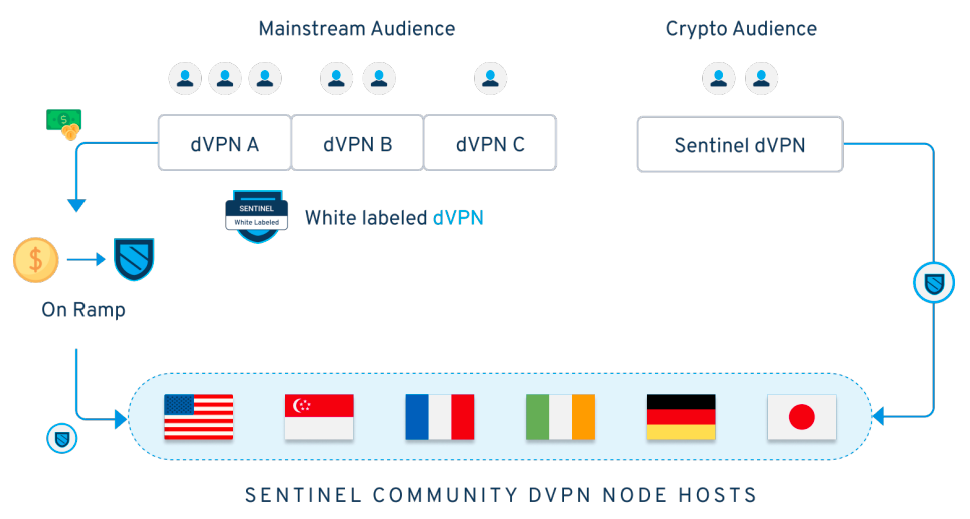
A dvpn built on the Sentinel framework can be operated by corporate entities or individuals. Sentinel also intends to work with existing centralized VPN providers to help them transition their backend architecture to a decentralized one; allowing these companies to further build trust with their existing customer base while also allowing them to further expand their service offerings .
You might find yourself wondering why an entrepreneur or existing organization would want to partner with sentinel to build a dVPN?
Sentinel's ecosystem eases three barriers to entry for new and existing VPN companies
- Cost and process of dVPN application development: Network protocols such as OpenVPN and Wireguard, although fully open source, need to be packaged into a scalable, secure set of "cross-platform" applications. Meanwhile, integrating subscription-based systems and payment gateways provides a tedious example of some of the more basic implementations needed to develop a dVPN network. The resource requirements needed to develop a high-end VPN/dVPN application from scratch are detailed for most people.
- Sentinel provides an open source, cross-platform dVPN client that is resilient, secure and highly scalable. This is because Sentinel adopts a cosmos-based architecture that provides a public-private key "account management" system in addition to on-chain node queries (more details to be announced in future publications). We make sure that building and customizing the architecture on top of Sentinel's framework is developer-friendly. The cost of the whole process is very competitive compared to developing your own VPN/dVPN app
- Node management and DMCA request handling: Leading cloud service providers will inevitably limit server access to exit node hosts, as streaming or downloading pirated content from that node will undoubtedly attract DMCA requests. Centralized VPN organizations often have to rely on "offshore hosting services" that may not offer the same level of reliability as more established providers in terms of uptime and live customer support.
- By integrating Sentinel's community-based node host, the Sentinel ecosystem removes exit-node management responsibilities for organizations building applications on the Sentinel framework.
- Owners of VPN applications will have the ability to create service contracts and establish certain quality standards with node hosts in the Sentinel ecosystem, without having to manage the ownership of those servers themselves
- Potential security threats and hacking-related risks: Code closed-source and centralized VPN solutions cannot be peer-reviewed and therefore cannot be evaluated by impartial security experts. This could lead to a potential vulnerability or security risk, with the ability to damage or severely damage the reputation of the company providing the service.
- The occurrence of security breaches not only puts users at risk that their data may be exploited, but also leads to a severe lack of trustworthiness in the VPN organization itself, which can significantly impact the organization's revenue and sustainability.
- This open source structure provided by Sentinel greatly reduces the chance of security breaches. An example of the advantages of open source software is that military organizations around the world use Linux as their operating system of choice for most of their systems. Linux is completely open source and is often scrutinized by third parties; unlike software suites like Windows, it is closed source and has a reputation for security issues.
While the Sentinel framework provides the tools and infrastructure to build and operate a robust dVPN service, it is the responsibility of the application owner to acquire customers and understand their specific target market in order to deploy an effective marketing strategy. It is important to note that product development and execution are only part of the many important factors. The other part revolves around the actual hands of the user and building a product that the market needs.
4 key principles for successful dVPN application
- Robust UI/UX: Apps built on the Sentinel framework should be indistinguishable from leading industry-provided VPN services in terms of user-friendliness and ease of access. Users may be reluctant to transition to a more decentralized solution unless their onboarding process is seamless, even amid the growing trend of demand for secure and transparent VPN services. The learning curve of using a dVPN app must be minimized by using smart design. To embody a strong brand image, there must be a strong focus on the specific aesthetic of the app.
- Effective Pricing Strategy: When trying to build a successful dVPN application, the implementation of a pricing model that is not only cost-effective but also profitable plays a crucial role. It is important for the application to be able to generate revenue which is then passed on to the node host. This enables them to monetize the bandwidth resources provided, creating a healthy and sustainable decentralized economy. The pricing model employed is entirely dependent on the target demographic and the type of service offered by the app. In the future, creators of dVPN apps in the Sentinel ecosystem will be able to offer premium services within their apps. These advanced services include a blockchain framework for building decentralized VPN applications, an upcoming relay network, and other enhanced privacy-related implementations. Additional services can be priced within a user's existing subscription or can be monetized based on the amount of data actually used. Regardless of the pricing strategy or revenue model employed by the dVPN owner/operator, it is the responsibility of the developer of the app to conduct proper due diligence and analysis to arrive at the best pricing model.
- Mainstream payment gateway integrations: Critically, Sentinel framework-based applications allow users to make purchases through fiat-based payment options, such as: Visa/Mastercard, Apple Pay, Google Pay, e-wallets (paypal, skrill, etc.). Only cryptocurrency-related payment options create a huge barrier to entry, preventing the average consumer from easily transitioning from a centralized VPN service provider elsewhere. While nodes hosted within the Sentinel ecosystem must be paid through the use of digital blockchain-based assets, dVPN application owners have the ability to monetize their applications through the use of fiat payment channels. The collected fiat currency can be converted into digital assets using an "inbound" service, which is then used to pay node hosts.
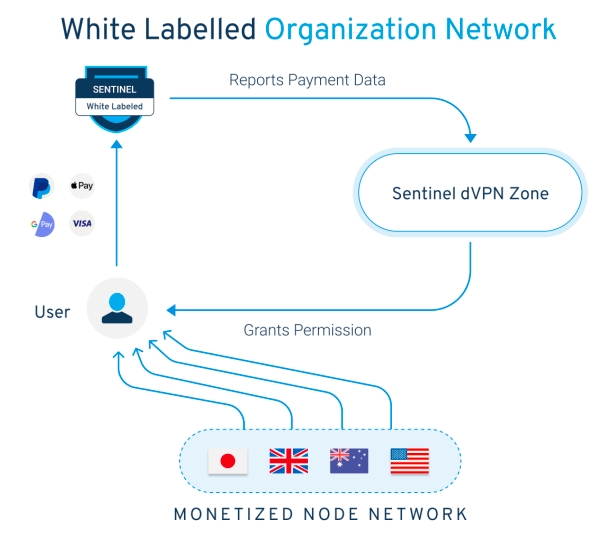
- Diversity of routing protocols: Different regions require specific routing protocols to seamlessly access data from the Internet while avoiding potential obstacles. In order to properly deploy optimal "user-specific" routing protocols in dVPN applications, the complexities and characteristics of various geographic locations must be fully understood. Network configuration performed seamlessly in one geographic location may be completely redundant in another, thus requiring a customized approach when selecting the appropriate routing protocol for a dVPN application. For example, the OpenVPN protocol cannot bypass the firewalls of several different countries, while it functions in other countries without any obstacles.
Overview of Sentinel based on cosmos block architecture
cosmos: the future of the decentralized cryptocurrency ecosystem
Interoperability solutions facilitate the exchange of assets and data between decentralized networks of various cryptocurrencies, reducing tribalism in the industry. under such circumstances,
“Tribalism” refers to the aggressive tendencies that decentralized networks exhibit when trying to establish or demonstrate their superiority over their opponents.
The truth is that some networks have unique service propositions, which are supported by their custom architecture and unique development focus. Interoperability enables participants in the ecosystem to leverage the benefits of these networks simultaneously without comparison, enabling horizontal scalability/specialization.
Cosmos aims to reduce this "tribalism" in the ecosystem by linking these competing chains together, effectively reducing the impact of significant fragmentation that would normally separate them. The Cosmos IBC module will allow these on-chain applications to expand their overall target market demographic by catering to a wider user base, helping to easily acquire new customers by enabling them to accept dynamic cross-chain payments.
Currently, the most important interoperability initiatives between Cosmos and other high-value and respected networks include the interoperability “bridges” being built from Cosmos to ZCash and Polkadot.
The Cosmos ecosystem enables Sentinel to build and manage its own native chain at the "hub" layer. Whereas dVPN applications built on Sentinel networks are either in a shared area or in their own local area, depending on the throughput needs of each application.
Chains built using Cosmos have the ability to maintain governance-related autonomy while also ensuring interoperability among other hubs and regions in the Cosmos network.
Unlike the ERC20 token model, chains built on Cosmos will not have to pay fees "ATOM" in Cosmos' native token, instead they will have the ability to pay in the chain's native token.
Hub and Zone Structure
Sentinel uses the Cosmos Hub/Zone architecture by exchanging all application-specific transactions and data on the "Sentinel dVPN Zone" (or sidechain), while abstracting token-related transactions and governance to the "Sentinel Hub" (or main On chain 0, to improve the scalability associated with dVPN dApps. Zone will communicate with Sentinel's main chain (hub) through Cosmos' Inter-Blockchain Communication (IBC). Zone can be loosely likened to a "state channel", It is deployed for efficient scaling.
The "dVPN" application-specific zone will have its own consensus governance, which is likely to be a subset of the Hub's consensus validator participants. While there is no monetary value exchange at the Zone level, the incentivization and de-incentivization of validators will take place at the Sentinel Hub level.
Using IBC, the hubs of the Sentinel network communicate with the Cosmos Hub and other hubs that are part of the Cosmos Network. Not only will this enable services in the Sentinel network to communicate with each other and accept the native token SENT or other whitelisted tokens, but it will also help them connect with other networks in the Cosmos network.
Sentinel - The Tendermint blockchain can host its own independently run dApps and/or service areas allowing its own set of validators to validate transactions through specific governance built on top of the Tendermint consensus.
Throughput
Tendermint uses the bPOS consensus system, where the blockchain can have a limited number of validators set up to achieve faster consensus while protecting the network from "Byzantine attacks."
Various P2P communication and privacy solutions will be built on the Sentinel network and will rely on high-volume, microtransaction-based revenue models. This makes the Tendermint blockchain perfect to support the Sentinel network, as it is able to achieve high TPS (transactions per second), especially with Ethereum's much lower "15 transactions per second".
Blockchains using Proof-of-Work (POW) consensus transactions per second (TPS) are slow relative to the blockchain frameworks used to build decentralized VPN applications, and many scaling solutions for such consensus networks require dedicated Hardware makes a high capital investment.
Cosmos uses a unique bond-Proof-of-Stake consensus in which votes from a fixed number of validators, with a certain amount of entropy, are accepted by the network at a specified point in time. This increases the overall throughput of transactions on the network as there is a limited number of validators processing transactions.
Tendermint’s BFT consensus system allows the Sentinel network to achieve faster transaction speeds than any current existing PoW network; PoW networks are hindered by the lack of clear finality. In bpos-based systems (like Tendermint), by using a poll-based voting system, utilizing a limited number of validators, by allowing token holders to "bind" tokens to validators deemed trustworthy , achieving a near-instant end.
interoperability
The interoperability of Cosmos' IBC protocol allows the creation of a peg (backed by a stablecoin). This feature can be developed for chains that are not part of the Tendermint or Cosmos ecosystem.
The utility of these zones will be mainly used for cross-chain payments. With this technology, community-hosted nodes running on the Sentinel dVPN network can accept cryptocurrencies like Ethereum, BTC, PIVX, DASH, NEO, Dfinity, Cardano, and more in exchange for bandwidth.
Any cryptocurrency can be integrated, whether it is built on the Cosmos SDK or not. This is achieved by using "bridging", which requires an interoperable connection between the two networks. This “Sentinel Hub” will connect to Cosmos IBC, and dVPN users can pay in different currencies or stablecoins supported by Cosmos IBC.
Since the IBC protocol can be effectively used for communication between different networks with different consensus mechanisms and structural diagrams (such as ZCash/Cosmos), Sentinel believes that, by introducing the Hub/Zone model, the IBC protocol can be used in transaction scalability and dAPP related. Very effective in terms of efficiency.
The technology provided by the Cosmos network and Tendermint allows us to envision a true free market economy, driven by "perfect cross-chain payment integration" that has not been possible with any other platform/network so far. This is the first step in a long journey to create real-world blockchain applications.
Governance
On Sentinel’s cosmos-based mainnet, network governance will be in the hands of validators. These validators will be determined democratically on the cosmos-based Sentinel mainnet through delegation of holders. A validator’s “voting power” or weight is determined not only by historical performance, but also by the number of tokens that Sentinel supporters have delegated to them.
Network governance proposals are handled by a group of democratic validators, bypassing the requirement to fork to a "new chain". These suggestions can include:
- Accept new validators or reject existing malicious validators
- Accept new zones and bridges, or reject existing ones
- Change the supply or lock a malicious/hacked account
Sentinel dVPN Architecture Overview
A centralized VPN architecture consists of multiple intermediate servers that manage user permissions and establish user connections to VPN nodes. This centralized architecture requires a high reliance on these intermediate servers, which poses a risk to network resiliency due to multiple points of failure and multiple points of attack. Downtime in a centralized VPN network can be attributed to one or more of these components not functioning properly and can lead to a decrease in user experience and satisfaction.
Sentinel dVPN framework offers incredible resiliency and security compared to any consumer-grade VPN. The Sentinels architecture minimizes the number of intermediate servers and dependencies. In addition to the account management and creation system, which is entirely on-chain, the process of querying available servers also takes place on-chain. A blockchain hosted as an application will run 24/7 without disruption, and the validator infrastructure for the global community is decentralized (immune to 1, 2 or 3 data center failures) so that application uptime and User experience will be far superior to centralized competing products.
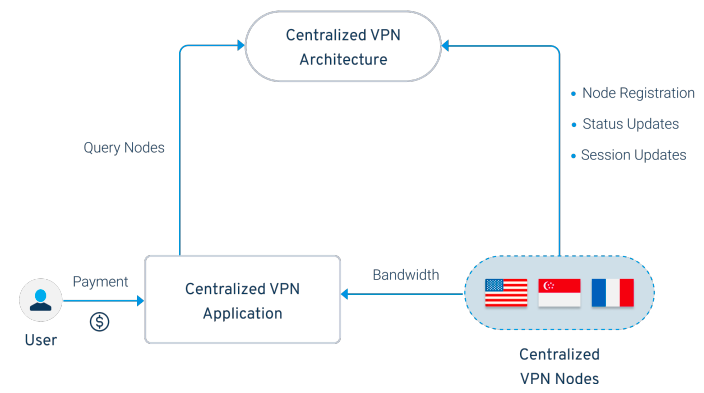
A major contributor to Sentinel's architectural resiliency is the decentralized distribution of computing power, which will be required to run Sentinel Hub and Sentinel Zone. The computing power required for the operation of the Sentinel dVPN ecosystem is not provided by any centralized organization, but is provided by expert "validated" organizations, distributed around the world, with highly redundant systems with significant bandwidth throughput and normal operation hours.
While Sentinel's architecture ensures that the user's anonymity is not compromised by the application itself, the use of Sentinel's upcoming relay network is necessary to ensure that the user is completely anonymous from the point of view of the exit node. The Sentinel Relay Network will allow users to connect to "relay nodes" through a series of tunnels, ensuring that users do not interact directly with exit nodes.
Sentinel's own "Proof of Bandwidth" protocol ensures a transparent and untrusted measure of bandwidth provided by service providers (community-based nodes) to end users. The “Bandwidth Provability” protocol integrated with the Sentinel blockchain provides a clear track record of the quality of bandwidth services provided and creates a certain level of trust among all participants. This data is later used to determine whether the node meets the required service level agreement to avoid penalties.
On-chain query
The implementation of Sentinel's "on-chain" query system is one of Sentinel's most important technical achievements and ensures a highly resilient and decentralized architecture.
With Sentinel's dVPN architecture, connections between users and exit nodes can be established directly without the need to connect to an intermediate server (such as a discovery node's master node) controlled by application developers or third parties. This is achieved by utilizing the blockchain as a ledger of "node queries", with nodes having the ability to interface and store information related to node attributes and connection instructions. The user's Sentinel-based dVPN application will populate the list of available servers by simply querying all available dVPN nodes by reading data from transactions in Sentinel's dedicated dVPN zone. Since authentication and identity management already occurs on-chain, the only point of failure in the Sentinel dVPN dApp structure theoretically (other than cyber sybil attacks) becomes a potential consensus security failure at the chain level. The only way to compromise Sentinel dVPN adoption is to compromise validator-driven consensus.
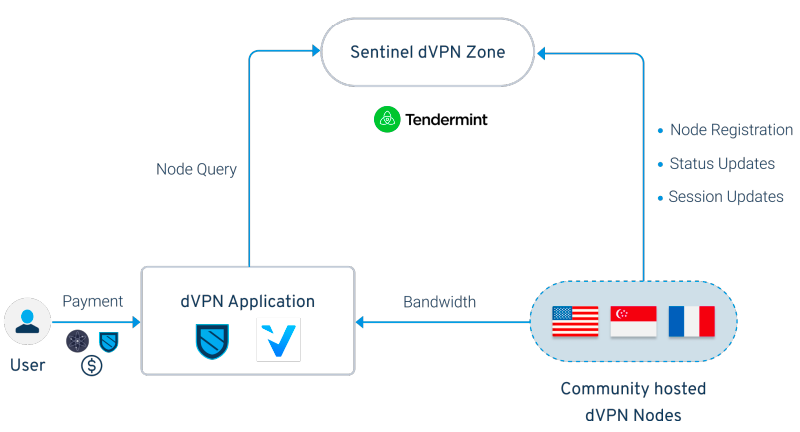
Mainstream VPN applications usually control the exit node, but also control and utilize intermediate query servers that exist between the exit node and the user, making the purpose of the relay network redundant since the original user's IP is easily visible.
However, the "on-chain query" architecture means that users only need to communicate directly with the chain, not any other centralized server that might record interactions.
relay network
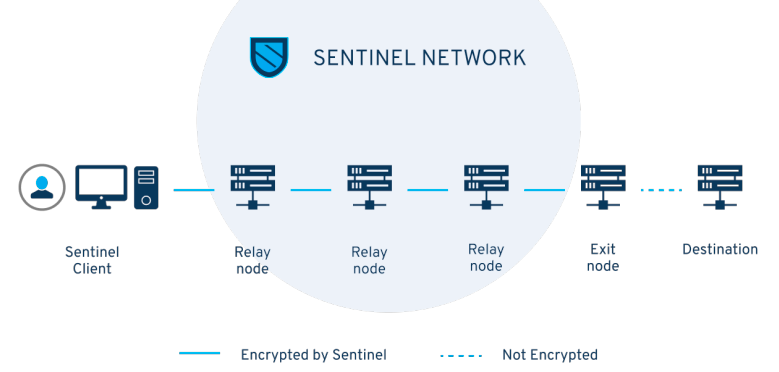
A robust network of relays is an important aspect of any end-to-end dVPN solution, which fully upholds user privacy. While neither the creator of a Sentinel-based dVPN application nor any Sentinel-based participant, the Sentinel blockchain can access any personal information associated with the user (such as IP addresses), without a relay network, hosted on An exit node in the Sentinel ecosystem has access to a user's IP address. While dVPN apps have the ability to provide relevant evidence, without logs user browsing and metadata collection/storage centralized to the app developer, it is currently impossible to prove that logs are not collected by exit nodes or stored locally on the host device.
To describe the relay network in simpler terms, the connection between a user and an exit node can be likened to a user making a cellular phone call to a third party. If the user's intent is to prevent third parties from seeing the user's number in Caller ID, the user will have to use their friend's device as a relay to block the user's phone number. The user would then have to call the friend who kept the user waiting and dial the third party's number before merging the two calls, thus connecting to the third party without exposing the user's data.
Similar to the cell phone intermediate caller example, the relay network consists of "relay nodes". A relay node is operationally different from an exit node because the exit node communicates directly with the user (in the absence of a relay network) and also communicates with the web-server on the internet. Relay nodes, on the other hand, only communicate with users, other relay nodes, or exit nodes.
A strong relay network includes:
- large number of participants
- strong governance
- Multiple network integration
The use of Sentinel-based relay systems will primarily target more privacy-conscious users who are willing to sacrifice internet speed to improve privacy.
The benefits of a relay network can only be realized when a large number of unique participants start hosting relay or exit nodes on the network. If, at any point in time, an entity controls a significant portion of the network, it becomes possible for that entity to de-anonymize users through a simple but effective "man in the middle" (MITM). One of the main goals of relay networks is to ensure that relay nodes cannot identify whether they are tunneling to a user or another relay node. If a user occurs routing traffic through the attacker's relay node as well as the exit node, the attacker is able to correlate the user's IP address and in turn determine the user's original request for information flow that is not simply another relay participant.
The importance of having a distributed network in the relay network to prevent man-in-the-middle attacks is shared by the Bitcoin ecosystem, mining is designed to prevent 51% attacks. If an entity controls 51% of the Bitcoin network mining hash rate, then that entity has the ability to disrupt the network, attacking the integrity of the network by performing a double spend. Bitcoin attempts to combat these monopoly risks in the mining ecosystem through its incentives. This incentive mechanism rewards miners based on their participation in helping discover and validate newly created blocks on the network. If Bitcoin is a voluntary network with no economic design, its security is likely to be compromised. A powerful entity with access to important hardware infrastructure can easily gain majority control of a mining network, an example of a volunteer-driven network is the TOR network. In the TOR network, the participation of relay nodes and exit nodes is not incentivized. Instead, they are encouraged to serve simply out of mutual respect for the spirit behind decentralization. Industry experts are concerned that the TOR network has been compromised by entities that control a large number of TOR relays and exit nodes. At this time, there are approximately 6,000 TOR relay nodes on the network, with an average of 6 million daily active users. This clearly shows the limitations and risks of volunteer-based networks.
The success of the Sentinel relay network is entirely dependent on the number of unique participants. Attracting these participants requires some level of incentive through mechanisms on the network.
Bandwidth-Based Proof
In a truly decentralized network, the allocation of bandwidth shares a common problem with hash generation by miners in a proof-of-work (PoW) network. The issue revolves around the ability of service providers (or miners in PoW cases) to abuse or falsify actual workloads. One of the main responsibilities of miners on the Bitcoin blockchain is to confirm the actual work (or hashes generated) of other miners and ensure that no one is blocking rewards by exploiting the system. Likewise, in the case of bandwidth allocation on a decentralized P2P network, a robust architecture is needed to prevent bad actors who intend to "spoof" the amount of bandwidth provided.
The need for a provable solution for bandwidth allocation networks can be illustrated by an analogy, the frustrating experience that many mobile phone users have with their network operators regarding their international roaming charges. Most roaming plans offered by network operators have limits on the amount of bandwidth that can be used, and sometimes even bill the user for the total amount of bandwidth used. It's common to hear people say they don't trust their carrier at all because they think they've been overcharged and don't understand how bandwidth consumption for roaming charges is calculated.
Provability of bandwidth distribution is important not only for network-centric use cases, but also for storage and compute-centric use cases, as there is a lot of bandwidth utilization involved. One of the key goals of the Sentinel ecosystem is to develop and implement the first bandwidth provable protocol, or "Proof of Bandwidth," to allow trustless bandwidth sharing. A blockchain framework for building decentralized VPN applications, the scope of the protocol goes beyond decentralized VPN applications built on Sentinel, with the ability to integrate with other distributed p2p resource sharing networks and even mainstream applications.
The first prototype implementation of Sentinel’s proof-of-bandwidth protocol took place on the Ethereum chain, backed by an external network of distributed masternodes. These masternodes will observe and measure the allocation of bandwidth between service providers and users, and then write certain properties of the session, such as duration and bandwidth consumed, to the Ethereum blockchain. This data is then retrieved by the dVPN app's billing mechanism to generate an invoice that the user must pay. This prototype architecture works as planned, but cannot be called truly decentralized due to the need for an additional network of masternodes.
The implementation of the bandwidth provable protocol currently being built on Sentinel is based on the Cosmos/tendermint network and involves generating "bandwidth signatures" from both the service provider and the user. These bandwidth signatures are essentially messages consisting of the bandwidth transmitted by the P2P connection over a preconfigured period of time. Service providers and users each generate their own signatures, each signed with their own private key, and these signatures are then stored on-chain for retrospective use. If there is a discrepancy (within a preconfigured time) between bandwidth exchange requests from the user and the service provider, the connection will be terminated due to the presence of at least one malicious actor in the exchange.
Bandwidth signature variables determined by dVPN application developers:
- The time period during which each bandwidth signature was generated
- Threshold Percentage for User and Service Provider Signature Differences
Example: Sentinel "Proof of Bandwidth" protocol integrated with "XYZ" dVPN built on Sentinel framework. The time frame for signature generation is 10 minutes, and the difference threshold is 10%. During the first 10 minutes of dVPN usage, the service provider enters an on-chain signature representing 1.05 GB of bandwidth provided, and the user enters a signature representing 1 GB of bandwidth used. The difference between the two signatures falls within the 10% threshold, allowing established connections to continue without interruption.
In the next session, the service provider's signature represents the 2 GB provided and the user's signature represents the 1.5 GB used, and the major difference between the two signatures exceeds a threshold, causing the connection to be terminated.
Payment Models and Escrow
The monetization of peer-to-peer bandwidth allocation allows for the use of a more dynamic payment model than is typically seen in the traditional VPN industry. In addition to the usual "prepaid" systems (where users buy subscription services for a fixed period of time), bandwidth providers (node hosts) also have the ability to set their own pricing per unit (GB) of bandwidth consumed.
dvpns running on the Sentinel ecosystem will be able to pay cosmos IBC through traditional fiat-based options such as credit cards as well as a number of cryptocurrencies supported by Sentinel. However, bandwidth pricing through both models will be primarily denominated in fiat.
It is important to note that while payment for bandwidth can be made in cryptocurrencies or fiat, the fees paid by the bandwidth provider (node host) for the infrastructure hosting the node are almost always denominated in fiat. Infrastructure-related costs include cloud computing costs as well as power costs (if node hosts use a self-hosted physical setup) and hardware costs.
Two key payment models available to dVPN users in the Sentinel ecosystem include:
- Live - dVPN Node Hosting on Sentinel uses a live payment model that allows users to pay per GB of bandwidth consumed. In this payment model, node hosts also have the ability to set their own prices for their services.
- Prepaid - The prepaid model is a more traditional payment model, similar to the one common in the mainstream VPN industry, where users buy access for a specific period of time. In prepaid mode there is no limit on bandwidth consumption and usage is usually unlimited.
Sentinel dVPN hosting system
An escrow system is used in a real-time payment model between users and service providers to ensure that neither party can fraudulently influence transactions. Before a connection can be established, the user is required to lock a certain amount of tokens in escrow, and the tokens will be deducted from this locked amount periodically based on the bandwidth consumed by the user. The precise measurement of bandwidth provided to users is made through the Sentinel "Proof of Bandwidth" protocol, which communicates with escrow agencies to establish a fully decentralized method for releasing tokens from custodians.
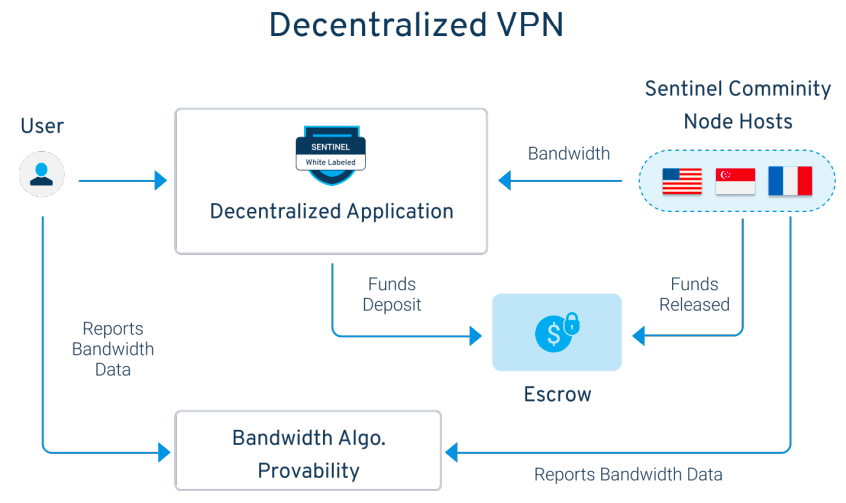
Token function
The core token utility of Sentinel Token revolves around it as:
- Governance and staking
- Payment methods for dVPN subscriptions
- Payment medium for premium dVPN services
- work token
Governance and staking
- The Sentinel token is essential for network security as it is the staking token for Sentinel's Cosmos-based Hub. Sentinel tokens will participate in governance-related decisions as a form of “voting power,” where the size of users’ voting power is directly related to the number of tokens they hold.
- Users can earn rewards by "delegating" their Sentinel tokens to validators as part of governance.
- Users can host validators and earn commissions from tokens delegated to validators. This can be considered compliant with the active validator set by requesting delegation or by accumulating enough tokens.
Sentinel hub is built on the Cosmos SDK and follows the same dpos-based governance protocol and framework as the Cosmos hub. The maximum number of validators at Genesis is set to 50. Validators on Sentinel Central have no minimum requirements for self-delegation.
While there is no minimum "self-binding" requirement for a validator, only validators are delegated to their own validators for tokens (whether from themselves or from external holders) that authorize the least number of validators (the last validator) validators, such as the 50th validator), a validator is eligible to enter the active validator set. On Cosmos and other Cosmos-based networks, the criteria for determining validator eligibility are also enforced by default.
Token holders have the ability to earn rewards by securing the network.
The Hub is set at 5% to ensure fair participation and no immediate maximum commission rate.
Stakeholders in Sentinel tokens will also have the ability to create governance proposals, or vote on proposals posted by other community members. These governance proposals provide the ability to edit various elements or variables of the chain without the need for a “hard fork” or manual shutdown of the chain based on maintenance.
Payment methods for dVPN subscriptions
- Sentinel tokens can be used to pay for dVPN subscriptions, but payment for these subscriptions is not limited to Sentinel tokens.
Subscriptions to dVPN services are similar to the subscription system of the vast majority of popular VPN services in the real world. In the traditional VPN industry and VPN services, it is rare to see billing based on bandwidth metering, and VPN services that provide metering usually provide advanced security services and deeper routing protocols. Subscribing to a dVPN service built on the Sentinel dVPN framework requires upfront payment for unlimited dVPN usage via one or more devices.
Sentinel tokens will be available as an option for subscription payments. However, users will not be limited to Sentinel tokens, as dVPN applications built on the Sentinel framework will be able to add real-world fiat-based payment gateways or payment gateways that support other types of decentralized currencies.
Through payments interoperability, dvpns built on Sentinel will be able to reach a wider audience by facilitating transactions from mainstream marketplaces (eg Google Pay, Apple Pay). If payment for subscriptions is limited to Sentinel tokens, the customer acquisition process will not be easily scalable and the target market will be very limited.
Payment medium for premium dVPN services
Premium services will require users to hold tokens in an escrow system, which will be used for real-time payments and governed by Sentinel’s bandwidth-provable protocol. This structure is inherent to the Sentinel Hub ecosystem, so transactions will be limited to native tokens.
More advanced services built on Sentinel will provide users with enhanced privacy and a greater degree of trustlessness through the use of managed services, as well as security-focused network integrations. These services include applications such as relay networks to highly unique and population-specific network protocols. Premium service providers (not dVPN app owners) can offer subscription services, as well as the ability to offer real-time bandwidth billing (pay by gigabyte).
These advanced services will use Sentinel's "Bandwidth Provable Protocol" for a decentralized governance system focused on the metering of real-time p2p bandwidth exchanges. This provability protocol ensures that there are no mischaracterizations of bandwidth provision or consumption, without requiring a third-party masternode system to monitor connections.
For subscriptions and real-time billing for these premium services, users will have to pay their own cost to host Sentinel tokens in the system. When using a subscription-based service, payment for the total duration of the subscription will be deducted from the locked token amount in installments. For example: a monthly subscription to a premium service may require 1/30 of the total subscription payment to be deducted from Sentinel Tokens in escrow on a daily basis. For real-time billing, payments are periodically deducted from escrow, directly related to the amount of bandwidth used by the user, providing a trustless and secure transaction processing environment.
work token
- Sentinel cosmos-based tokens act as work tokens, thus allowing token holders to staking tokens for rewards. These rewards are generated by node hosts that provide bandwidth for dVPN applications built on the Sentinel framework.
The decentralized power of Sentinel's blockchain consensus primarily relies on staking participation in Sentinel Hub's validator governance. Token holders stake their tokens to trusted validators to earn staking rewards, while effectively increasing the "attack cost" of malicious attacks. The exchange of digital assets (cryptocurrency and stablecoins) as a dVPN service takes place at Sentinel Hub, and holders of Sentinel tokens will be rewarded from the revenue generated by node hosts on the Sentinel network as a transaction security for the ecosystem. exchange of contributions.
A percentage of the revenue generated by the node host will be accumulated in the pool and then paid to token holders on a regular basis. The value that token holders derive from revenue sharing will be directly related to the total demand for dVPN services from Sentinel framework-based applications. The increase in the total number of users and subscription revenue generated by dVPN applications built on Sentinel will result in an increase in the number of dVPN nodes required to meet the growing user bandwidth demands.
hardware fusion
The Sentinel dVPN protocol integrates with network routers based on Open-WRT (the popular open source router firmware) and will allow router owners to become node masters by easily monetizing their bandwidth. Additionally, Sentinel aims to support and integrate any open source router capable of applying dVPN connections across the wi-fi network. A router-based dVPN would allow users to avoid installing a VPN app on each of their devices, and users might create a secondary home network just for access via dVPN.
easy to monetize
One of the benefits of an ecosystem like Sentinel focused on "bandwidth monetization" is that there is a lower "cost-based" barrier to entry for participants, since in advanced economies, almost everyone has a stable and reliable internet connection. This low "cost" threshold of "bandwidth monetization" can be compared to the high "cost" threshold of mining Bitcoin, which requires users to purchase specific hardware to mine and earn Bitcoin.
Sentinel enables anyone anywhere in the world to earn passive income by contributing bandwidth resources to Sentinel-based dVPN applications, while hosting Sentinel dVPN nodes on virtual machines requires some technical experience. This "technical" barrier to entry reduces the potential of the Sentinel node hosting community because it prevents less tech-savvy users from participating. To address the technical hurdles of operating a node, it not only needed to make Sentinel dVPN very easy for regular users to use, but it had to be as simple as possible to host a node and offer bandwidth in exchange for tokens.
Those concerned about exposing their residential IP when hosting exit nodes will have the ability to host relay nodes. By hosting relay nodes, owners of Sentinel dVPN-enabled routers will be able to remain anonymous to their internet service providers, while also being able to make money from users who pay for this premium service.
What are routers and why they matter
A router is a device that is critical to our reliance on the Internet because a router creates a gateway to connect two or more networks. In addition, routers enable the network to facilitate multiple devices because routers ensure load balancing and distribution of bandwidth throughput.
General features of routers:
- 1. The ability to build a wireless network
- 2. Ability to apply encryption standards for data routing through wireless networks
- 3. Allow the wireless network the ability to handle multiple devices/load balancing
- 4. Expand network coverage
- 5. Dual-band capability to prevent lag
What's wrong with industry standard routers?
1. The standard is completely closed source and does not provide the public with the ability to conduct fair code reviews
2. Standard routers do not provide users with the ability to tunnel bandwidth through a verifiable dVPN network, which provides the assurance of security and encryption
3. Standard routers do not provide users with the ability to make money from excess unused bandwidth
what does that mean
1. Standard routers can be hacked and manipulated, it can take months or even longer to find and fix vulnerabilities because the codebase is not public (eg Linux and Microsoft)
2. Standard routers do not currently provide users with the ability to securely use a decentralized and distributed VPN application that transparently certifies the integrity of its backend operations
3. Standard routers do not allow users to monetize excess unused bandwidth, resulting in a waste of paid resources
Organization
The "Sentinel" organizational structure is mainly composed of the "Secure Network Technology" Foundation and Exidio, a for-profit organization focused on dVPN implementation and development. As of this writing, both the SNT Foundation and Exidio are fully registered and structured.
The SNT Foundation is focused on bringing an organizational and governance approach to the Sentinel distributed ecosystem, while Exidio is responsible for the technical development of the Sentinel dVPN framework, as well as the onboarding of dVPN application creators.
"Secure Network Technology" Foundation
- Provides financial and non-financial support to designated ecosystem projects - Responsible for providing non-financial and financial support to projects and organizations that exist in the Sentinel Ecosystem and that aim to build on and add to the Sentinel Ecosystem value.
- Drive Adoption - Drive adoption of Sentinel Tokens by envisioning and supporting smart use cases and utility mechanisms.
- Ensuring Token Economic Viability - The mission is to ensure a robust token economic structure Sentinel's ecosystem. It is necessary to monitor inflation and other network parameters with a focus on ensuring that the value of the token does not dilute significantly over the long term.
- Guaranteed Economic Health - Create a healthy and productive environment for validators/nodes/other service providers in the ecosystem. Design and maintain a robust economic structure to ensure that service providers can meet breakeven costs and are properly compensated for their time and effort.
- Increase Ecosystem Partners - Facilitate collaboration between the Sentinel ecosystem and entities that add value to the Sentinel ecosystem and drive protocol usage and token adoption.
- Global Community Expansion - Expand the global Sentinel community by maintaining and supporting each Regional Group and managing Regional Group Ambassadors accordingly. The SNT Foundation is responsible for ensuring that the structure of the ecosystem is compatible with different regions and that the design of the ecosystem does not hinder any particular geographic location.
EXIDIO
The Sentinel ecosystem is rapidly evolving from a more obscure and anonymous network to a transparent real-world ecosystem designed to serve the needs of mainstream consumers. Exidio is a for-profit organization focused on implementation, with the mission to "provide secure access to Web 3.0" by contributing to and implementing Sentinel's dVPN and Sentinel's universe-based blockchain infrastructure. Exidio will work with entrepreneurs as well as existing VPN companies to build a new dVPN application or transition an existing VPN network to a dVPN network.
While Sentinel focuses on providing an environment that houses the various components of the overall dVPN network, Exidio will focus on implementing white-label dVPN applications, with the necessary customizations.
The VPN industry is expected to be a $90 billion-plus market by 2027, and global VPN entrepreneurs are capitalizing on the growing consumer demand for VPN services and implementing white-label solutions. White-label solutions offer the benefits of lower cost-to-market and require less technical expertise and resources to manage.
Exidio's contribution to Cosmos mainly revolves around the following aspects:
- Development Tools - Develop meaningful and creative utilities (e.g. Exidio multi-sig/joint account deployment) that can be implemented by other developers in the Cosmos ecosystem.
- Develop dApps - Develop useful and efficient decentralized and distributed blockchain applications (like Sentinel dVPN) in the Cosmos ecosystem, capable of providing real utility functionality to mainstream users.
- Contribute to the Cosmos SDK and Tendermint Core - Contribute to the proposed roadmap and work on optimizing and improving the efficiency of the current codebase of Tendermint and Cosmos SDK.
Whitepaper: https://sentinel.co/whitepaper
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!

- Author
- More