What bad thoughts can little penguins have? ——A personal arrangement of some broken things about Tencent software reading browser information
Tencent software such as QQ, TIM, and even most domestic commercial Internet products generally have privacy problems. It is actually expected to read and sell user information. This time, it was caught by solid evidence.
roughly through
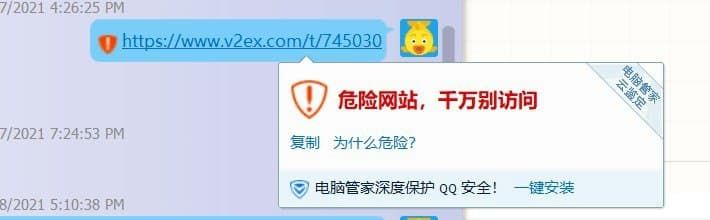
First, a user posted a post on v2ex, and found that the custom security rules of velvet security on the pc blocked the qq client's attempt to read the history of the Chrome browser (the link to the original post is here )
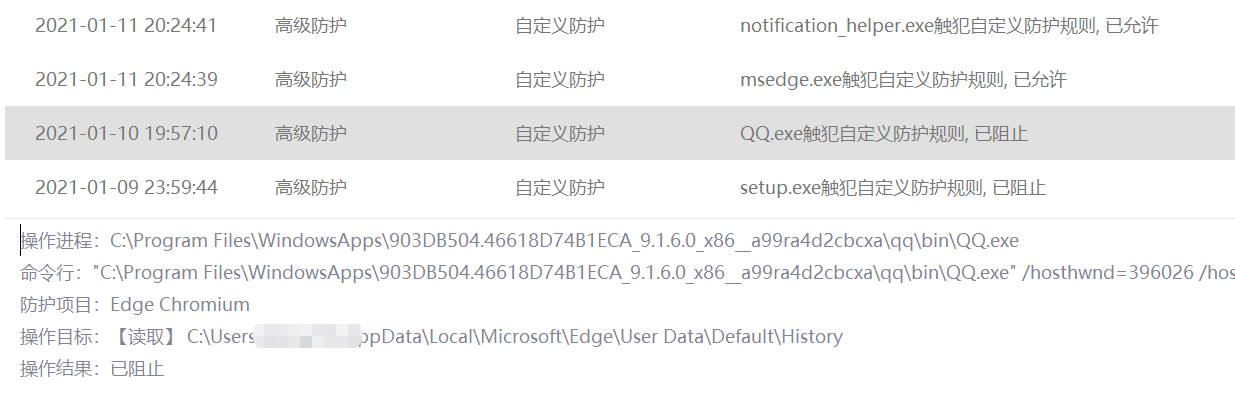
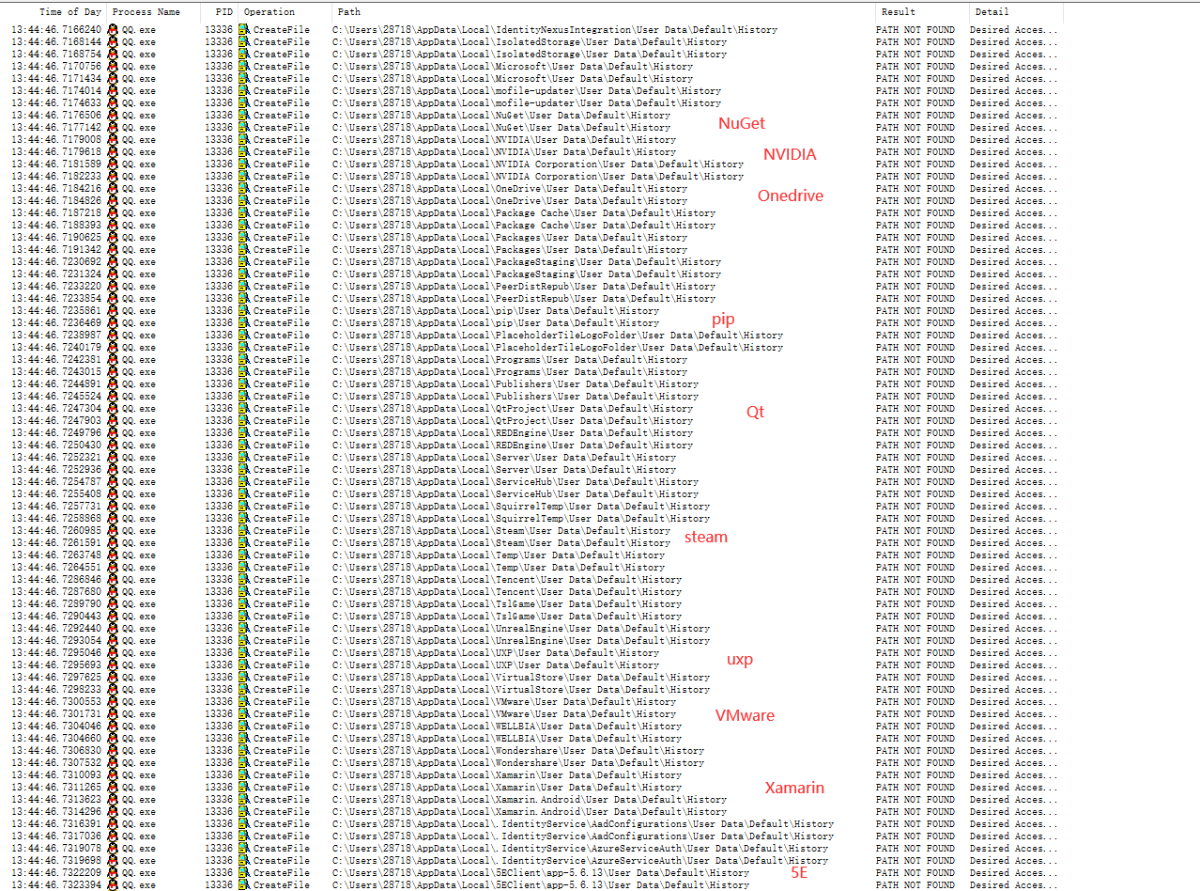
After that, someone on the Kanxue forum verified this ( the original post address , and the backup ), and clarified the fact: not only QQ, but also TIM read all Chrome browsers (including but not limited to Chrome, Chromium, 360 Extreme Speed) , 360 Security, Cheetah, 2345 and other browsers) history.
Quoting the content of the original text is " Look carefully, this thing traverses all the folders under Appdata\Local\, and then adds User Data\Default\History to read. User Data\Default\History is Google browsing. If you are not familiar with browsers such as Firefox, and don’t know how the directory is, the default history record storage location, and it is normal for Chrome to be shot. ”
What happened after that is even more unbelievable. Both v2ex and Kanxue Forum were attacked by the network, so that the access timed out or the opening speed was very slow for a long time.
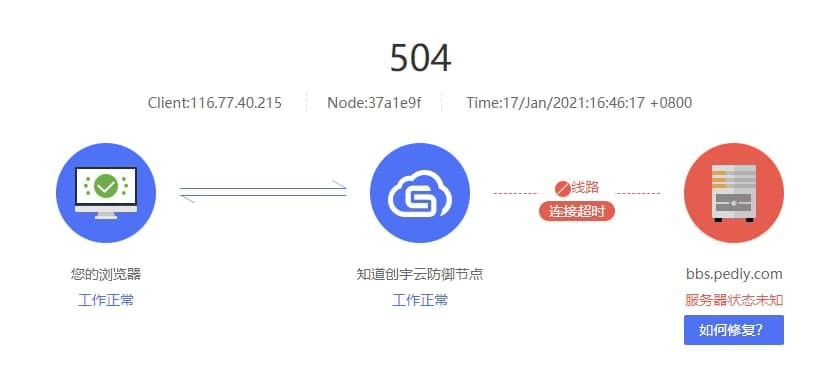
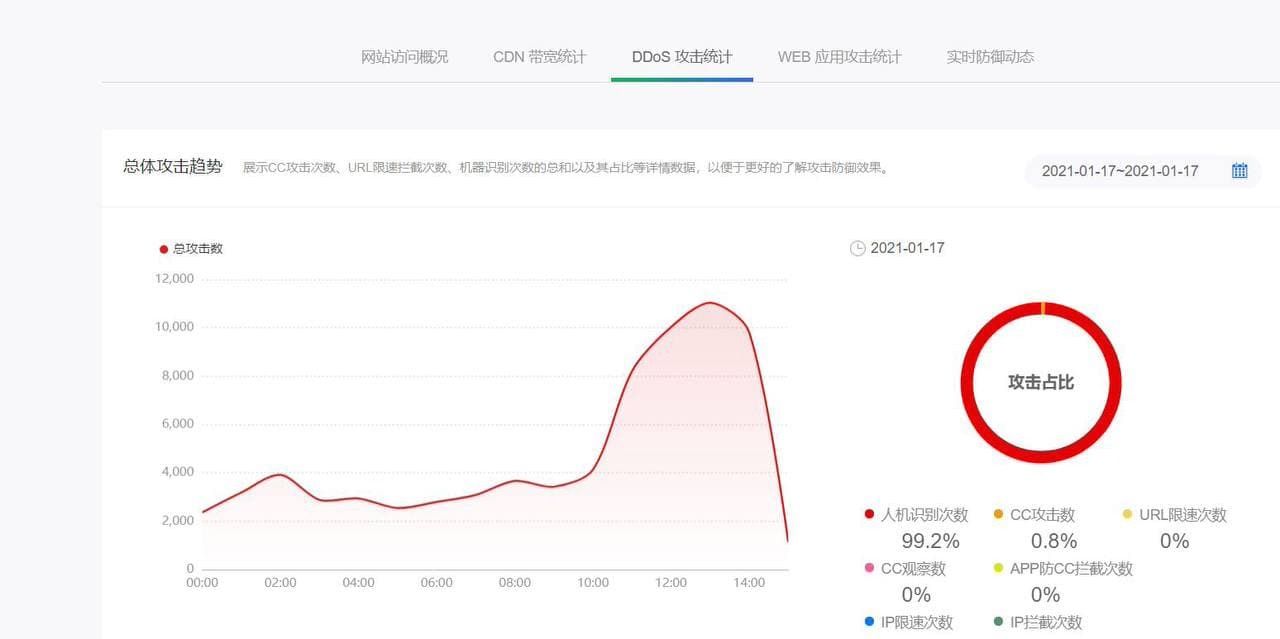
As for v2ex being attacked, at 11:30 noon, the loading speed of the v station became very slow. The author experienced it personally. At that time, I couldn't figure out what happened, and then I thought that it might be because of these broken things.
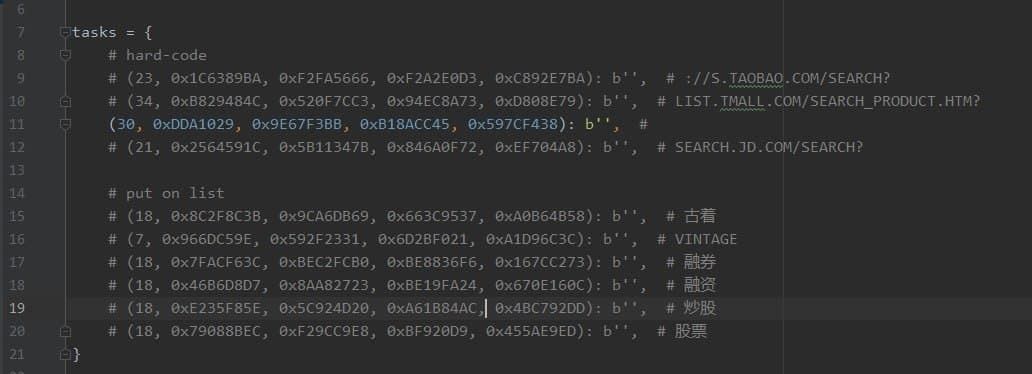
At the same time, in addition to actively discussing privacy in various groups, enthusiastic netizens also began to reverse QQ-related codes with strong curiosity and strong action. The reversed behavior of QQ is probably to match the URLs in the read browser history (counting as an MD5), and upload the matched records. ( tg original post address )
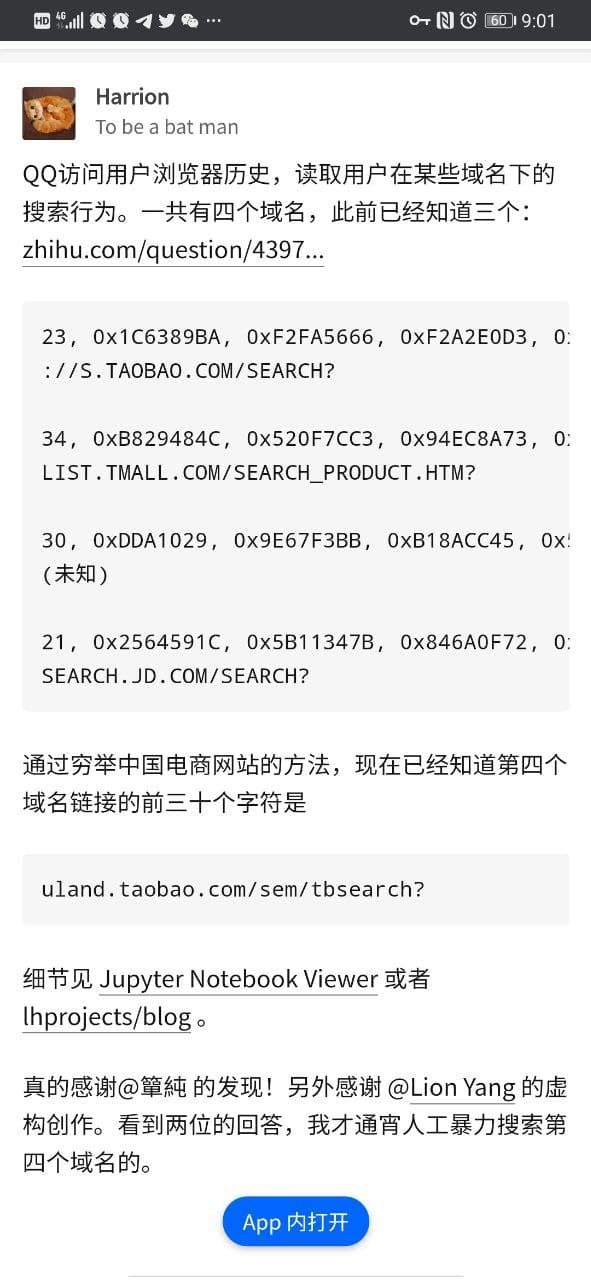
According to the research on the MD5 value, it is probably (building a table, constructing a collision or something?), so far, all the keywords have been solved.
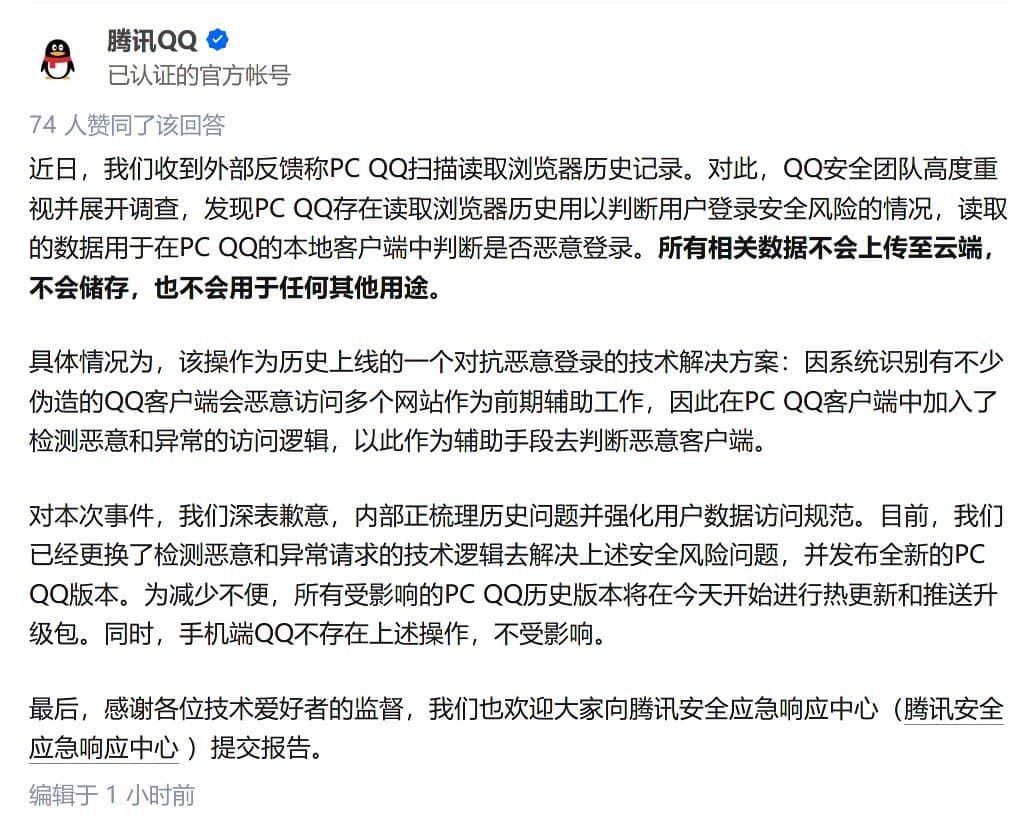
When the matter came to light, Tencent's public relations responded like this ( backup ), and it never changed.
As for whether a large-scale ddos attack was carried out on the platform that raised the question at the same time, since "no terrorist organization has yet declared responsibility for the attack", it is not known whether the cyber attack was the cause.
other follow-up
- Tencent's reply, I believe you a ghost, you can say whether you believe it or not
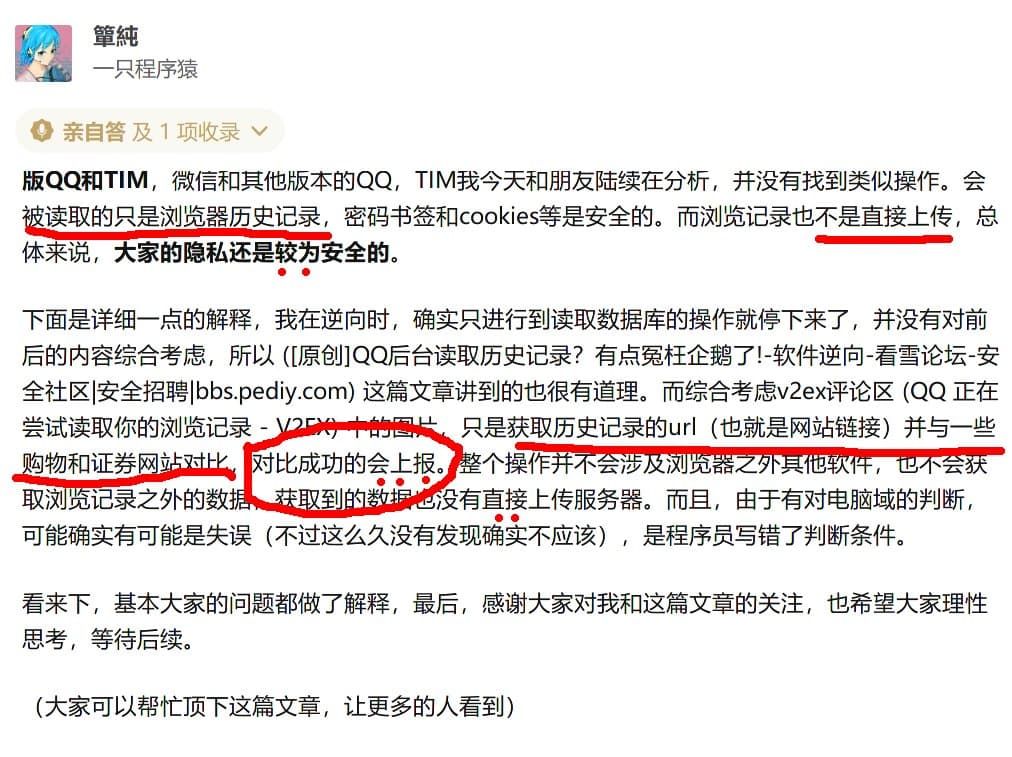
- Look at the reply of the party in the snow forum,
if you are kidnapped/hijacked, just blink.

- Tencent's actions,
the body is honest
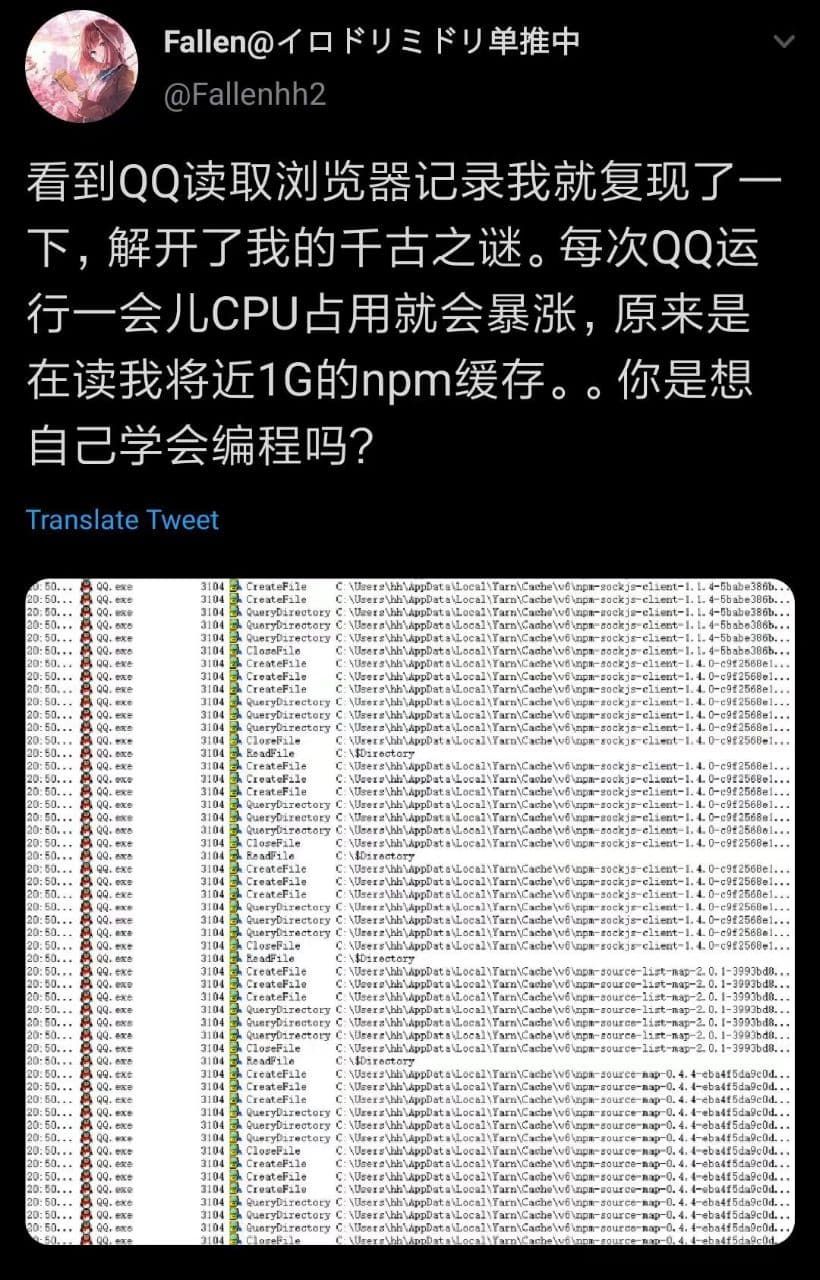
- Trivia: Self-learning
QQ is actively self-learning, you see how you are still so self-deprecating.
Fast forward to the Ascended Penguin (Crossing)
The author's thoughts
The author has absolutely no concept of network security and reverse engineering, and the technical issues are only fancier-level cognition. However, there is still a relatively common sense perception of the virtues of domestic commercial software. "Illegal overcoming the wall" is better not to carry these burdens. There are tens of thousands of ladders, safety first, lack of privacy, and two lines of tears when drinking tea. I don't know how many people this major negative news can make people realize that this kind of characteristic domestic closed-source commercial software is a villain, or it will be business as usual after the popularity passes, and privacy will be changed for convenience.
Some personal experiences that may be useful are probably that dirty things should be isolated, and it is best to do physical isolation. The author personally keeps a mobile phone to install domestic software, WeChat QQ contacts with others, Alipay receives and pays money, Jingdong Taobaomei Missions are carried out on this phone without bringing the hassle to the computer. If using a computer is unavoidable, it is recommended to use a virtual machine (VMware, VirtualBox, etc. VMware recommends turning off the access to the host system by in-VM software such as converged mode), or at least the sandbox software sandboxie ( this article may be available for refer to).
Software such as QQ occupies almost the entire market. It is really frustrating to kidnap users arbitrarily.
Like my work? Don't forget to support and clap, let me know that you are with me on the road of creation. Keep this enthusiasm together!
