
IYP 不是过眼云烟的新闻网站,我们提供实战能力,这里是值得您反复回看的档案室:iyouport.org
A great day with Mr. S - Anti-Forensic Techniques: Easy Ways to Become Untraceable (3)
- There are as many anti-tracking methods as there are tracking methods

If you haven't read earlier in this series, see it here:
- " Creating your own freedom in unfreedom: Simple ways to become untraceable (1) "
- " Building defensive intuition is a basic skill for survival: a simple way to become difficult to track (2) "
Sun Tzu said: It is so insignificant that it is invisible; it is so divine that it is silent, so it can command orders for the enemy. "Subtle and insubstantial, the expert leaves no trace; divinely mysterious, he is inaudible. Thus he is the master of his enemy's fate."
Mr. S came to the public library in a 1986 old Jeep CJ-7.
A pragmatic and low-key man, he prefers reliable old cars that don't rely on computer chips to run and are fast enough.
Mr. S loves books and goes to the library twice a week to check his email on the public computer and exchange books he has read for new ones.
The library's parking lot is equipped with a closed-circuit television (CCTV) camera on the roof of the building that can capture all vehicles entering and exiting, including Mr. S. However, because Mr. S's car was dirty and the license plate was covered with mud, it could not Reads license plates well.
But be aware that in some countries it is illegal to have dirty license plates. Therefore, the way to avoid license plate reader surveillance should not be masking, but deception . For example:
Not only the car, the camera also captured the scene of Mr. S walking into the main entrance of the library - his face, but because Mr. S was wearing a red ball cap with tiny LED lights on the brim, and blurred his face with white letters and sunglasses facial contours that can fool facial recognition algorithms.
There are many other effective methods , see below for details:
Mr. S is an activist who is part of a social movement that resists the excessive power of local and central governments. He values his privacy and does not like the government collecting any information about his habits, such as the books he checks out from the library.
Other than the ball cap, Mr. S's clothing has no features that would make it stand out in any way.
This is important. And it’s not just clothes, please pay attention to these tips :
- " Counter Reconnaissance: In addition to technology, you should also pay attention to many important details "
- " What pitfalls should you pay attention to during counter-reconnaissance ?" 》
Mr. S put his books in the car and walked over to sit at a public computer that offered free Internet access.
This is one of several libraries he visits regularly and Mr S has identified the locations of all CCTV monitors and selected an available computer whose display is not within the monitor's field of view .
Please note that this is a set of techniques , the first thing you need to know is how you appear to the watcher:
- " Knowing People with Your Eyes": Do you want to know what you look like in the eyes of a "spy"? 》
- " Applying Covert Field Techniques to Your Daily Life: Simple Ways to Defend Hostile Surveillance "
Mr. S opened the default browser on the library computer, which happened to be Internet Explorer version 11 (i.e. 11.285.17134.0), since the computer was still running Windows 7. This is a very common phenomenon in public places.
The library has not received the necessary funding for several years to upgrade its 15 public computers.
IE version 11 is like an aging car for web browsers. It is buggy, vulnerable to multiple unpatched vulnerabilities, and is completely helpless as it is no longer supported by Microsoft as of January 12, 2016.
If the administrator has not disabled this feature, Mr. S's first step is to clear his browser history, cache, and cookies.
Often, computers in public libraries are locked so they are heavily restricted to prevent people from using them inappropriately.
Next, Mr. S navigated to Gmail and created a disposable email account (garbage2434234@gmail.com) specifically for the purpose of signing up for a 7-day free trial of the Hide My Ass virtual private network (VPN).
Private email can be dangerous, as you can see below:
- " How to Dig Your Phone Number Just Through Email: A New Approach to Open Source Intelligence Tracking "
- " How to track down a Twitter account using just an email address?" 》
About using secure disposable email accounts like this:
Don't log into your private email directly from a public computer, and don't enter any real private information directly; but be aware that your best bet for hiding your identity is a public computer - if you've been targeted and are planning an escape route , it is a good option. The premise is that you can do what Mr. S does. Remember our "Perfect Stealth" series? Here is the complete list of 7 articles .
Once the disposable email account was established, Mr. S entered false information into the HideMyAss VPN 7-day trial web registration to include payment information from a prepaid gift card he had purchased earlier with cash .
What if you don’t have the convenience to buy gift cards with cash? Don’t forget these tips:
- " 5 Reputable Disposable Credit Card Number Services: Hide Your True Identity "
- " 3 Best Virtual Debit Card Services : Hide Your Real Identity in Payments "
Since this was a gift card, Mr. S entered the fake address into the address field along with his newly created disposable email address.
He tried opening Command Prompt and discovered that he did not have permission to open the Command Prompt app. Mr. S was familiar with the Windows operating system and searched for PowerShell to gain full access.
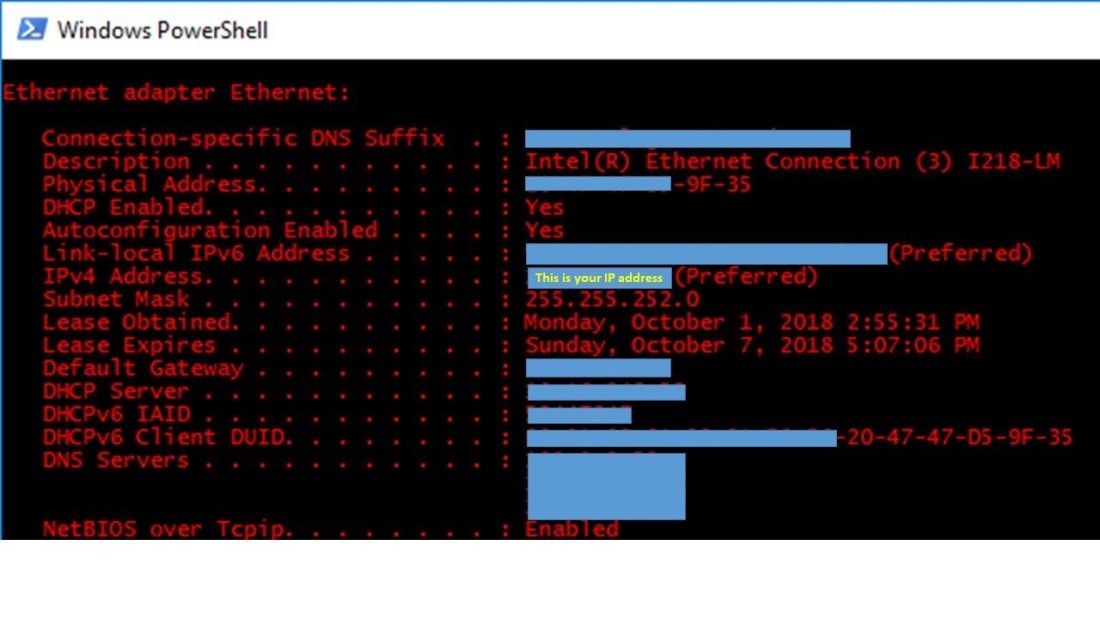
Mr. S types " ipconfig /all " and notes the current unprotected Ethernet adapter IPv4 address of the library computer he is using. Then leave the PowerShell window open.
At the same time, the credit card registration is successfully completed and Mr. S can choose to download the VPN software to his computer. He tried doing this and was able to download the program file to his desktop, but soon discovered that he was blocked from launching the program executable (.exe).
Mr. S received an error message stating that this operation requires elevated privileges.
Mr. S decided to try guessing the administrator credentials and then right-clicked on the executable program file and selected the "Run as administrator" option.
Mr. S successfully guessed the password after only a few attempts. Turns out it was P@ssW0rd123... Looks like the admin is a lazy guy.
He then went on to install the HideMyAss VPN program that he downloaded to his computer desktop.
This took about 5 minutes and Mr. S can now surf the Internet anonymously from a public library computer.
Once the VPN was running properly, Mr. S verified the new IP address by opening a command line window via cmd and typing ipconfig /all, then restarted Internet Explorer 11 and continued opening his actual email, ProtonMail account (ProtonMail offers its own VPN service, but requires For the purpose of this example, select highlight HideMyAss).
The ProtonMail account is " JackerCrack911@protonmail.com " - note that his real identity was never part of his email address .
Now, he also knows the administrator password, which will make it easier to wipe his tracks when he's done using it.
Mr. S checked his email and personal banking sites, as well as a few other sites. If he failed to use a VPN on a public library computer, browsing these sensitive sites would be dangerous.
Of course, a better way is Tails, which is installed in a USB and hung on the key .
- More Safety Manual
After surfing the Internet for about 20 minutes, Mr. S closed the Internet browser. But before closing, Mr. S carefully cleared the browser's search history, cleared cookies and cache.
He also deleted the contents of Pagefile.sys, swap and thumb files, so his browsing history cannot be easily recovered without advanced IT forensic software tools and techniques .
Mr. S subsequently terminated the VPN connection and uninstalled the HideMyAss VPN software.
He deleted the program files from the C:\ProgramFiles directory, then typed "regedit" in the Windows search bar and selected "Run as administrator."
He enters the appropriate administrator account login credentials, which he had successfully guessed previously, and the Registry Editor module opens.
Next, Mr. S navigated to “Computer\HKEY_LOCAL_MACHINE\SOFTWARE” where he found and deleted the “HideMyAssVPN” software registry key. Here are the steps outlined by Microsoft:
"You can omit registering an application by removing the RegisterProduct Action , RegisterUser Action , PublishProduct Action , and PublishFeatures Action from the InstallExecuteSequence Table and AdvtExecuteSequence Table . All of these actions must be removed, or some trace of the application may remain in the registry. Removing all of these actions prevents the application from being listed in the Add or Remove Programs feature in Control Panel, and prevents the advertisement of the application. Removing all of these actions also prevents the application from being registered with the Windows Installer configuration data. This means that you cannot remove, repair, or reinstall the application by using the Windows InstallerCommand-Line Options , or the Windows Installer application programming interface (API)." ~ Microsoft Docs
Mr. S then opened the Windows Event Viewer by typing "Event Viewer" in the Windows search bar and right-clicking the app and selecting "Run as administrator."
He enters the administrator account login credentials again and selects the Windows Log, Applications option. He then scrolled down to find events generated by installing the HideMyAssVPN app and uninstalling the program.
Next, since Mr. S completed these actions using an administrator account, he will open the security log and delete *only* the events related to his actions. Don't delete the entire log, otherwise there will be no money here .
Needless to say, the above is a hypothetical event, and while all of these actions can be performed, it would not necessarily be possible for an average user to be so successful at guessing an administrator account password and being able to wipe their records.
Don't be discouraged if you feel like this example is too cumbersome, too detailed, or too technical to follow, but it does suggest that you may not be fully aware of the actual effort required to become virtually untraceable. .
⚠️It’s not easy to become virtually untraceable, and you have to be familiar with technology to understand how computer systems and networks operate to a certain extent.
Can you perform the same operation on a Mac or Linux operating system? Do you know where to find the file or even what the name of the file is? And you should also be aware that VPNs themselves may be insecure.
- " Beware of Malicious VPNs "
- " VPN?" Invasion? Bitcoin? How exactly were the Russian attackers discovered? 》
- " Have you seriously considered the security of VPN? "
- " How to Verify Your VPN Connection is Secure?" 》
- " When Do You Need a VPN?" 》
digital forensics
We've covered digital forensics, including how crappy its current use is, and uploaded two books and a manual, see Digital Forensics Is Flooding: What Data Can the Government Extract from Your Phone? 》.
Although a complete introduction to digital forensics is beyond the scope of this series, it may be useful to briefly mention that there are methods and tools that can be used to recover deleted files and extract critical information from computer systems and hardware .
If investigators are able to establish that Mr. S downloaded and installed HideMyAss VPN, they can also obtain a warrant for the VPN service to provide copies of its logs as part of a digital forensics investigation to prosecute him.
Even if you think you are completely untraceable online, there are still many pitfalls that you may not have thought of. Whether it is your local computer, the oligopoly companies on the Internet, or your ISP, you may be betrayed.
Therefore, ⚠️A person can never become completely untraceable - but, you can make it as difficult as possible. This is enough to throw off most monitors. It's still the idea we emphasized in "Perfect Stealth": beat your opponents to death, exhaust their financial resources and energy, and you will win .
The primary target of a digital forensics investigation is the suspect, and the prosecution must be able to prove that the digital evidence came from a computer allegedly used by the suspect and that the data is an exact copy of the bitstream.
Once again, please read the three materials we uploaded in the telegram channel and become familiar with this knowledge. Once you are wrongly imprisoned, you and your lawyer should know how to defend yourself:
- How to use your mobile phone and computer as evidence in court: https://t.me/iyouport/6313 ;
- Another book: https://t.me/iyouport/6315 ;
- A manual: https://t.me/iyouport/6419
These materials are about professional digital forensics technology. Through them, 💡you will be able to know what aspects are considered in digital forensics, how to connect information, and how to form evidence to assist the court in convicting. So you know what to avoid and how to avoid it.
Anti-forensics techniques and countermeasures
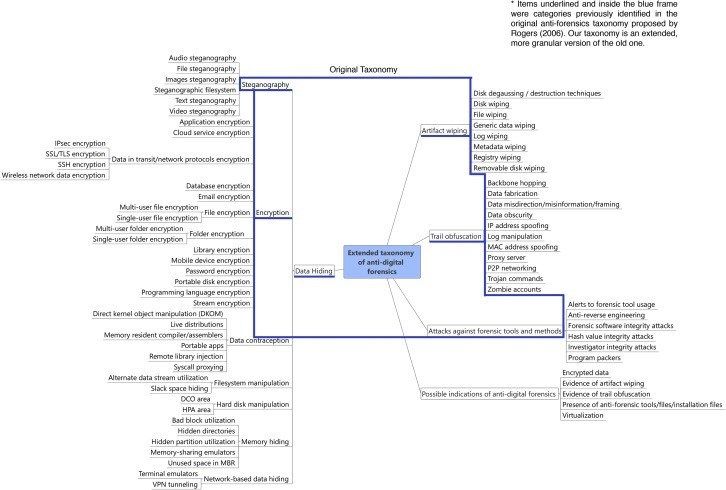
If you want to be difficult to track, you must first recognize it. ⚠️Those knowledgeable and experienced IT professionals - especially law enforcement digital forensic investigators and intelligence agency cyber analysts - who have a variety of methods, techniques and tools that can recover deleted files and can track your online activities , and help discover your true identity.
It's the nature of the centralized Internet to be easy to track and monitor. Not only professional and technical personnel, but also ordinary people can track and monitor certain targets to a certain extent. Anyone familiar with " open source intelligence " investigations will not doubt this.
You need to remain aware of this fact and operate accordingly - as much as the field is devoted to the design of forensic tools, it is devoted to the design of anti-forensic tools, which are tools specifically designed to defeat forensic tools. .
Let’s take a look at the technologies and tools available to help achieve online untraceability.
1. Data hiding
Digital steganography , which has been discussed many times before, can hide confidential data by embedding and encrypting it in other carrier files, such as images, text, video, and audio files. You can review it below:
- " The Careful Tips of Steganography (1) "
- " Sending Secret Messages Using Steganography (2) Simple Tutorial "
- " Building your custom OSINT machine (Part 2) "
Almost any type of file can be used to hide data, as long as you find a steganography application that supports it - and with over 1,100 of them , it's not hard to find.
Cryptography is another method of hiding data that has been covered many times before. Of course, it's always recommended to use Full Disk Encryption (FDE) on your hard drives and phones (including SD cards) . But there are really many ways to hide data.
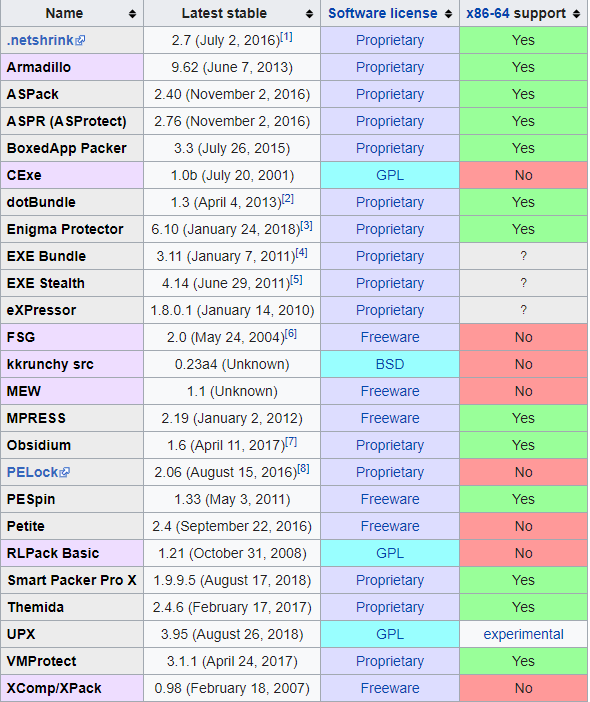
Packers and bundlers, as shown in the table below, compress executable files into other types of files and bundle them together, which also makes the executable file more difficult to reverse engineer.
This is how rootkits are formed. A rootkit is basically a type of malware that consists of "a set of programs and code that allows permanent or consistent undetectable [root-level access] on a computer ( Donzal, 2005 )."
Rootkits are also sometimes used by law enforcement and even corporate IT departments for remote access/surveillance purposes.
Detection is difficult because they are hidden and buried deep in computer operating system files that antivirus software may not scan, and are polymorphic.
Typically, rootkits do not spread themselves like worms. A rootkit can be downloaded to a target's computer by clicking on a malicious link in an email or website, which, while opening the link you want to view, also begins to silently download a so-called "dropper" file.
Additionally you can download a book "Malware, Rootkits and Botnets: A Beginner's Guide" here: https://t.me/iyouport/6504
2. Anti-forensic erasure
If there is sensitive information on your computer that you can't find, you can program your computer to automatically wipe the entire operating system. Once executed it will automatically start deleting files, making the forensic investigator's job more difficult, if not impossible.
But this can also get you into trouble if you forget the correct boot sequence. Better have a backup!
If investigators noticed what was going on, they might be able to shut down the system quickly, but at best, they would only get partial data.
Anti-forensic erasure tools , such as those found in Kali or Black Arch Linux OS distributions, SRM, Wipe, Overwrite, DBAN, BCWipe, Eraser, R-Wipe, DiskZapper, Cryptomite or Evidence Eliminator, will be able to effectively remove and overwrites the memory making it unrecoverable .
For more details, see:
3. Footprint confusion
Imagine a dog is tracking you. They know your scent. If you cover yourself with perfume, rotten eggs, mint leaves, etc., the dog will not be able to find you.
Obfuscation is the logic of planting false information about yourself online to throw you off the radar of stalkers.
In this sense, it involves using sophisticated tools to modify data about your activities.
For example, deleting logs, using a sock puppet identity when accessing a system or website, deliberately providing incorrect information, using a clone account, providing IP address hopping (Tor, I2P, FreeNet), using tools such as Timestomp or Transmogrify to modify timestamps and metadata and File header information .
- About sock puppet making " How to quickly create a dummy? 》
- About " Role Playing " with Different Identities
- About Doppelgänger " The Complete Guide to Doppelgänger: How to Manage Your Online Identity and Stay Safe "
- About Tor " Never do these nine things when using Tor to protect yourself ! 》
- About metadata erasure " They are all tools, from self-protection to effective utilization - good and evil metadata (Part 2). Using them skillfully is a basic skill of digital citizenship "
The thing to remember from all this forensic/anti-forensic thinking is that becoming untraceable is much more difficult than you initially think. Technology is often not on your side here.
It’s not that technology is bad, but the security aspects of most technologies are far from perfect, and we haven’t figured out how to plug the holes yet.
⚠️It must be emphasized that the first requirement for becoming difficult to track is the mental component of how people think and view the world - you need to know how the tracker thinks, and then the technical component of virtual or cyberspace. You'll find it's not hard to do if you know how.
You will gain more confidence as you become more proficient at this. Confidence gives you courage and strength. Keep a low profile and continue to make yourself the master of the fort. ⚪️
——To be continued——
Like my work?
Don't forget to support or like, so I know you are with me..
Comment…