
A person who does not recognize the existence of the Almighty has neither honor nor dignity.
What is a blockchain code audit?
Auditing smart contracts is an important step before launching a dApp: third-party auditors can find vulnerabilities that the team itself can miss. Audits are conducted using both automated tools and careful manual analysis to prevent most hacks. Learn how an audit is done and why you shouldn't invest in unaudited protocols.
In a nutshell
- The audit process consists of project review, automated testing, manual code review, and peer review. After that, a detailed report is compiled with a list of detected vulnerabilities and recommendations for their elimination.
- Automated smart contract testing tools allow you to find common vulnerabilities such as reentrancy, transaction reordering, overflow, and timestamp dependency. The most popular instruments are Mythril, Manticore, Slither and Oyente.
- Automated testing saves a lot of time, but can miss bugs in the code or give false positives. Therefore, manual line-by-line analysis of the code is necessary.
- Most audit firms work with Solidity and EVM networks, as well as Solana, but some, like OtterSec and Halborn, are already working with Move. Move is a much more secure language than Solidity, but dApps on Move still need to be audited: for example, Pontem Wallet is in its third audit.
- Unaudited dApps are a common target for hackers - or they can simply break due to an internal error. Prominent examples are Nomad, Beanstalk and Yam Finance.
- Leading smart contract auditors include Hacken, OtterSec, CertiK, ConsenSys Diligence, Halborn, and Quantstamp.
What is a smart contract audit and why is it so important?
An audit of a blockchain code or smart contract is an analysis of the code of a blockchain or dApp, carried out either by its creators or by a third-party auditor, the purpose of which is to find errors, vulnerabilities and bugs.
Blockchain security is part of Vitalik Buterin 's famous trilemma : security, scalability and decentralization. These three critical aspects of a network or dApp must be kept in balance.
Like any software project, the dApp cryptocurrency must work reliably and stably, otherwise customers will quickly lose faith in it. But in the case of blockchain, the stakes are higher, since hundreds of millions of dollars of liquidity can be stored in a dApp - and all this money can be withdrawn in one attack if a hacker finds a loophole in the contract code.
A key method to prevent this is a code audit provided by a third party. We'll take a look at how smart contract auditing works, what vulnerabilities it can uncover, which firms operate in this area, and finally, how skipping an audit can lead to catastrophic losses.
Blockchain audit in 5 steps
- Design analysis and top-level code analysis
The external audit team needs to get a good understanding of the project: its architecture, business logic, practical application, etc. Many major DeFi exploits target holes in application logic or economic vulnerabilities. It's great when the verifier can point out such logical flaws, although this may be beyond the scope of smart contract auditing itself.
The client should also describe the objectives of the audit, how the tests should be conducted, what use cases should be tested, and other key information.
Next, the audit team reads the entire repository to understand how the dApp logic is implemented.
2. Automated testing
There are still not so many software tools for testing smart contracts, and almost all of them are designed for Solidity and EVM networks. They cannot find flaws in business logic or tokenomics, but save auditors a lot of time. The most popular of them are:
Mythril by ConsenSys is a powerful open source tool that detects many critical errors; included in the MythX security package.
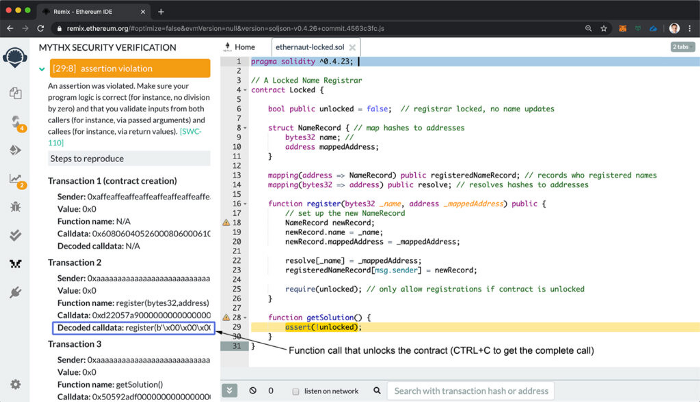
- Manticore is a tool that goes through various attack scenarios by feeding character inputs to see if they will crash the dApp; finds inputs that will lead to a specific error; finds out what caused a particular crash, and so on.
- Slither is a fast and easy to use checker that highlights critical vulnerabilities and suggests fixes.
- Oyente - Created in 2016, this tool has not been updated for several years, but still gets good reviews for its accuracy.
General vulnerabilities
Smart contract auditing software can detect many kinds of vulnerabilities, including:
- reentrancy - an attacker repeatedly calls the withdraw function to transfer funds from a vulnerable smart contract to a malicious one.
- reordering - the attacker achieves the completion of his transaction before other transactions in the queue in order to manipulate the price (the so-called front-running).
- overflow and underflow - sending incorrect data to force the smart contract to make a calculation error (the result is either greater than the allowed upper limit or less than the lower one). As a result, an attacker can mine a huge amount of tokens.
- timestamp dependency - an attacker passes an incorrect timestamp to the contract to give the impression that his transaction occurred at a certain moment (for example, to win an auction or lottery).
- replay - interception and subsequent re-sending of data to the blockchain (can be used to steal funds during fork events).
3. Manual line-by-line analysis and code testing
This step helps to find all errors missed by automatic tools. It also detects false positives: snippets of code that were erroneously flagged as vulnerabilities by automatic audit programs.
An audit can reveal vulnerabilities of different severity levels: critical (allows an attacker to steal tokens, break a dApp, etc.), medium (potential damage is limited) and low (still a bug, but poses a small risk of financial or structural damage) .
4. Peer review
Ideally, you want multiple auditors for maximum assurance. Sometimes auditors work in teams and review the code together so that the peer review happens at the same time.
Keep reading to learn about the risks associated with refusing peer review.
5. Audit report
Finally, the test results are summarized in a multi-page report that is sent to the client. It contains a list of detected errors, as well as recommendations for their elimination and further improving the security of the project.
It is standard practice in blockchain to make audit reports public: this is actually a good marketing tool for projects as it demonstrates the security and transparency of the dApp. Of course, if any critical vulnerabilities are found, the project usually fixes them first.
Section of Halborn's audit of the Reef protocol
The smart contract audit problem in Move vs. Solidity
As we explained in our article on the Ethereum virtual machine , EVM and Solidity smart contracts are difficult to debug and have many security issues. Add to this the dominance of EVM chains ( 9 of the top 10 DeFi TVL blockchains use EVM ) and you can see why the smart contract industry is so focused on Solidity. It has both a first player advantage and many vulnerabilities that need to be audited.
When you move from the Ethereum/EVM ecosystem to an alternative blockchain environment like Move, you run into a very interesting problem. On the one hand, the Move language and Move VM are much safer than Solidity and EVM. For example, Move contracts are resistant to reentrant attacks.
On the other hand, Move-based dApps still need to be audited – and there aren’t many blockchain security experts working with this language yet. Pontem Wallet auditors OtterSec and Halborn are among the pioneers, and Pontem Wallet itself is one of the first fully verified dApps on Aptos, which we are very proud of.
By the way, our auditor OtterSec has published a very interesting blog post on how to build more secure dApps with Move, using our Liquidswap DEX code as an example!
Top Smart Contract Audit Companies
Founded in 2017, Hacken audits entire blockchain protocols, smart contracts, and dApps. The firm also oversees bug bounty programs for platforms like CoinGecko.
Hacken works with a wide range of blockchains: EVM chains, Solana, NEAR, Cosmos, Polkadot, etc.
Its clients include FTX, Gate.io, Crypto.com, KuCoin, Huobi, Ellipsis, IoTex, 1inch, Aurora, Klaytn, Cirus, Victoria VR, WAX, TrustSwap and dozens of other DeFi, GameFi, infrastructure and NFT projects.
OtterSec is the leading blockchain audit provider in the Solana ecosystem. His impressive portfolio includes Wormhole, Serum, Saber, Raydium, Solend, Socean as well as Anchor, LayerZero and Proximity on NEAR.

Moreover, it is one of the few blockchain audit firms that works with the new Move programming language used by Aptos and Sui. OtterSec has completed the first audit of our Pontem wallet for Aptos as well as the Hippo wallet.
OtterSec also has a great blog with expert advice on smart contract security, especially Solana.
Zellic was founded by the world famous whitehat hacker team called Perfect Blue. In 2020 and 2021, they were ranked as the #1 CTF (Capture the Flag) team in the world, participating in cybersecurity events such as Google CTF and Def Con CTF.
The company is known for its speed of execution and ability to find hidden vulnerabilities. Its security engineers identify not only code flaws, but also economic and business logic flaws.
Zellic's clients include Aptos Labs, Solana Foundation, LayerZero, SushiSwap, 1inch, Wormhole, and more.

CertiK is best known for its blockchain security leaderboard, where 3000+ projects are ranked by their degree of trust. Security audits are an additional area of CertiK's specialty, along with penetration testing (attempts to infiltrate parts of the system that are denied access by any and all means), KYC, error correction, chain monitoring, and wallet tracking.
CertiK has conducted 1800+ audits for Ethereum, Avalanche, BNB Chain, Solana, Algorand, NEAR and Cosmos protocols. It is a trusted audit provider for Binance, The Sandbox, Huobi and OKex.
Halborn was founded by white-hat hackers in 2019 and now includes 50+ blockchain security professionals. In addition to smart contract auditing, the company specializes in security consulting, penetration testing, and security automation.
Halborn has worked with such popular projects as Polygon, Solana, Thorchain, Bancor, Pangolin, Reef, Sushi, BlockFi, Polkadex and even Bored Apes Yacht Club. He is also one of the auditors of Pontem Wallet, the first wallet for the Aptos blockchain.
We recommend Halborn's blog , which provides reveals of recent DeFi hacks and a deep dive into the most common types of blockchain attacks.
Zokyo is a comprehensive security firm with well-known ethical hackers on its team. She specializes not only in smart contract auditing, but also in penetration testing, data leak detection, database assessment, and CMS vulnerability auditing.
Zokyo has worked with dozens of major blockchain projects, including Fuse, yearn.finance, LayerZero, Qredo, CPRX, Shoyu, Badger DAO, ShapeShift, and more. What’s more, Zokyo’s security engineers are among the top rated contributors to “bug bounty” programs, hosted by Twitter, Facebook and Uber.

ConsenSys is the company behind MetaMask, Truffle, and Infura, key tools for Web3 developers. Its smart contract audit division, ConsenSys Diligence, works with over 100 teams such as Aave, OmiseGo, 0x, Aragon, and Horizon.
ConsenSys Diligence provides services in addition to audit: threat modeling, continuous vulnerability testing, retaliatory attack planning, and others.
Quantstamp has worked on over 250 projects, generating over $200 billion in assets and locked liquidity. Her portfolio includes OpenSea, Curve, Maker DAO, Compound, NBA TopShot, Lido, SuperRare, Decentraland, Aave and Axie Infinity.
The firm works with many blockchain ecosystems such as Solana, Ethereum, BNB Chain, Cardano, Flow, Near, Tezos, and Hedera Hashgraph. It also secures Teku and Prysm clients for Ethereum 2.0.
3 DeFi dApps that failed because they didn't audit smart contracts
The unaudited DeFi dApp, which holds millions of dollars, is essentially painted with a target that says “Hack me.” And even if it is not operated by a third party, it can fall victim to internal code problems. Here are three stories that show the consequences of missing an audit.
Nomad bridge: $200 million went free floating
Nomad is a bridge connecting Ethereum, Evmos, Moonbeam, Avalanche and the Milkomeda protocol. According to Paradigm head of security @samczsun, the Aug 2 exploit targeted a recent Nomad update that has not been verified.
3/ My first thought was that there was some mistake in the token decimal setting. After all, the bridge seemed to be running a “send 0.01 WBTC, get 100 WBTC back” pic.twitter.com/H9IOJRYB0G
— samczsun (@samczsun) August 1, 2022
A bug in the contract allowed users to send small amounts of WBTC from Moonbeam and receive back 10,000x WBTC in Ethereum. You didn't have to be a coder to do this: just copy-paste was enough.
As news of the loophole spread, more and more people joined the free game. This was not a one-man hack, but rather a chaotic, opportunistic 41-address attack. In total, about $200 million was lost - all the liquidity stored in the bridge.
Nomad said it will work with blockchain security firms to trace and recover the money. However, perhaps she should have brought in blockchain security experts before pushing the unaudited contract update on the mainnet!
Beanstalk: $180 million hacked via flash loan
Beanstalk is a decentralized stablecoin on Ethereum. Instead of using collateral to maintain the BEAN peg, it uses credit, encouraging holders to lend their BEANs in exchange for interest.
On April 17, 2022, a hacker exploited a bug in the Beanstalk control code. They have taken out flash loans on Uniswap, SushiSwap and Aave, borrowing about $1 billion in DAI, USDC, USDT and BEAN. The hackers staked this liquidity in the BEAN pools on Curve, raising enough LP tokens to win a majority of the votes in the Beanstalk DAO.
The attacker then submitted a new Beanstalk Improvement Proposal (BIP) to transfer all funds from the protocol to their own address - and voted for it so it automatically passed. In total, the attacker received up to $182 million in BEAN, ETH, and Curve LP tokens. Now all they had to do was pay off the flash loans.
Beanstalk smart contracts have been verified by Omnicia . But the code containing the flash loans vulnerability was added later without auditing. The lesson is that smart contract auditing is an ongoing process: every new feature must be tested.
Yam Finance: 99% not working due to a bug
The Yam Finance project, launched in August 2020, was an early experiment in rebasing, with the supply of YAM increasing or decreasing based on price. The project paid rewards for highly profitable farming, but what really attracted users were cute emojis and memes about yam potatoes (YAM = YFI + Ampleforth, two DeFI protocols, the ideas of which were borrowed by Yam Finance).
The whole project was implemented in just 10 days, while the founders were “running in ideas”. Because it was just an experiment, the team deployed Yam Finance without an audit. It came as a shock when $400 million poured into the protocol in one day.
But just two days after launching, Yam Finance collapsed. The reason was a bug in the rebase function: the contract was mining too much YAM for a certain pool on Uniswap. Most of these YAMs were sent to the treasury, which in turn rendered the control module unusable as the number of YAMs in users became insufficient to achieve a quorum for any vote.
A potential solution was found, but it needed to be pushed through a DAO vote. The team called on the community to delegate all of their YAMs to vote, but the result was not enough. Co-founder Brock Elmore tweeted that he was "heartbroken."
forgive everyone. I failed. thanks for the crazy support today. I am sick with grief.
— Brock🌱 (@brockjelmore) August 13, 2020
Yam Finance lives on with just $200,000 in TVL . The lesson is that the DeFi protocol can go viral so quickly that there is no time to find bugs and fix them. Before launch, an audit must be carried out.
Audit is not a guarantee of security
A single audit of a smart contract is never a 100% guarantee that the project will not be exploited - for several reasons:
1. For example, Grim Finance lost $30 million to a hacker in December 2021 despite being audited by Solidity Finance.
It turned out that the analyst in charge of the audit was new ; although auditors usually review each other's work, the team was “overwhelmed” and the peer review process did not go well. To Solidity's credit, this was only the second exploit among the 900+ projects they've reviewed.
2. The attacker can steal/forge the wallet key instead of breaking the contract. This is exactly what happened to bZX ($55M lost) and EasyFi ($90M). In the latter case, the perpetrator gained access to the MetaMask wallet of the protocol CEO himself.
3. Some exploits use holes in a third-party dApp (unaudited) to attack another protocol integrated with it.
4. Future changes in the blockchain. As the network on which the dApp runs is upgraded, new attack vectors may emerge.
For all these reasons, agreements and audit reports always contain a disclaimer. From the dApp team's point of view, the best way to minimize these risks is to go through multiple independent audits - to have "audit redundancy" if you will.
This is our strategy at Pontem Network as we want our Aptos dApps to be the most secure in the ecosystem. While our Ottersec auditors did not find any vulnerabilities in Pontem Wallet, we are currently working with Halborn on another review and a third review is on the way.
Of course, this slows down the scaling process somewhat, but we believe that user security is a higher priority than rapid growth. In the end, we are building a set of foundational dApps for an ecosystem that can host the first billion blockchain users, and Aptos itself is the most secure L1 blockchain in the world. So it is only fitting that we prioritize safety.”
Watch the latest Pontem AMA livestreams with core protocol developer Alejo Pinto to learn more about security at Pontem Wallet and Aptos. And don't forget to follow us on Twitter and Telegram to learn more about the audit process!
Author CryptoRomb He also has a telegram channel of the same name, I advise you to subscribe =)
Like my work?
Don't forget to support or like, so I know you are with me..
Comment…